I'm on the phone all day every day with clients who are either manually provisioning users or cobbling together scripts with bandaids, duct tape and chewing gum to get their user provisioning automated. If you don't have it fully automated yet, you are not the lone ranger.
That does not mean that you shouldn't, obviously. User provisioning should be automated, it should incorporate all of your applications (cloud and on premise) and it should tie into your access governance as well.
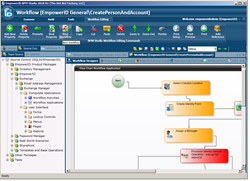 Let's start with the first part: automating your user provisioning process. This is basic identity management workflow. In the case of EmpowerID, it is VISUAL identity management workflow, meaning that the workflow is designed and configured in an easy to manage and visualize visual business process management layout.
Let's start with the first part: automating your user provisioning process. This is basic identity management workflow. In the case of EmpowerID, it is VISUAL identity management workflow, meaning that the workflow is designed and configured in an easy to manage and visualize visual business process management layout.
When you are sitting in a conference room designing the provisioning process, you are most likely at the whiteboard drawing rectangles and arrows and directories. That should translate directly to the identity process workflow in EmpowerID, allowing your business needs to dictate your identity policy instead of your identity software dictating your business.
The identity management system will have connectors to all of your applications and identity stores. Usually, HR is your authoritative system of record; EmpowerID will inventory HR for hired or fired employee records and initiate the onboarding and offboarding workflows. The user account will be created in the metadirectory and based on the rules and policies in EmpowerID, will initiate workflows to all of the other affected systems and applications that this user should access.
The metadirectory sits in the middle and keeps a centralized record of all of the user's accounts and access. This "person record" gives a whole view of the user and allows for auditing, constant updates to attributes and resultant access (whether it be roles or group membership or application access). This makes auditing easy, makes it possible to see changes that happened outside of the system (through native access), and allows for attestation and separation of duties policies.
Those internal users aren't all of your users though. You have partners, customers, dealers, contractors and a host of other external users. The old "keep them in AD" practice won't work, there is too much risk there. EmpowerID's metadirectory and workflows give you the ability to keep user accounts in the same system, design similar workflows and manage rights and access in a much more secure manner. You can even have anonymous workflows to allow external users to create an account with limited access and send requests to internal users to grant additional access.
And, to just what applications are you provisioning users nowadays? Certainly more than you were five years ago. You have cloud applications, AS400 applications, web applications, and the usual suspects of AD and Exchange. You need a modern IAM provisioning software (like EmpowerID) that can handle provisioning to all of these applications. EmpowerID has direct connectors to most major applications and the ability to map APIs to workflow shapes for ones that we don't. Most importantly, by having a framework to quickly deploy and manage connectors, EmpowerID can connect to almost anything, keeping user accounts current and secure.
 The third part that is important is to integrate with all other aspects of Identity and Access Management (IAM). Most legacy applications (I'm looking at IBM and CA and Microsoft and Quest here) are the result of myriad acquisitions and mergers and the products are put together in a way that not all modules work together. EmpowerID is built from the ground up on a single code base and the platform shares common components like the metadirectory and RBAC engine and workflow studio.
The third part that is important is to integrate with all other aspects of Identity and Access Management (IAM). Most legacy applications (I'm looking at IBM and CA and Microsoft and Quest here) are the result of myriad acquisitions and mergers and the products are put together in a way that not all modules work together. EmpowerID is built from the ground up on a single code base and the platform shares common components like the metadirectory and RBAC engine and workflow studio.
So, if you are provisioning to the cloud, you can create role based provisioning so only salespeople get a CRM account and they are automatically federated for single sign on and application roles. When you reset your password in AD, it flows and resets passwords in all applcations. If your user is promoted, this reflects throughout their identity, changing application access and roles within the application. If a user attempts to access a highly secure folder, a second factor authentication can be launched to ensure they are who they say they are (and have what they are supposed to have).
It needs to be a full identity ecosystem.
So, automate your user provisioning process but do it with an identity ecosystem that covers all of your identity needs. Even if you don't deploy all of it right away, have a platform that can handle all of your identity needs.

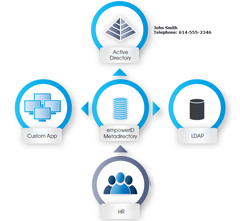 Having a hub and spoke solution allows you to easily flow attributes from the authoritative source to the metadirectory and back out to the appropriate identity stores. An example would be that HR is authoritative for a user's title, then empowerID metadirectory would inventory HR, see the change and update the user's "person" account in the metadirectory. With that change, it will need to be flowed out to the LDAP identity store and Active Directory.
Having a hub and spoke solution allows you to easily flow attributes from the authoritative source to the metadirectory and back out to the appropriate identity stores. An example would be that HR is authoritative for a user's title, then empowerID metadirectory would inventory HR, see the change and update the user's "person" account in the metadirectory. With that change, it will need to be flowed out to the LDAP identity store and Active Directory.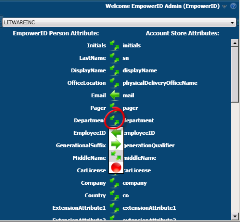 It is as simple as configuring the arrow to indicate the authoritative source. It can be authoritative from either identity store (arrow facing one way), last change wins (arrows facing both ways), or don't sync (big red dot). "Big red dot" is a technical term in the world of UI, trust me.
It is as simple as configuring the arrow to indicate the authoritative source. It can be authoritative from either identity store (arrow facing one way), last change wins (arrows facing both ways), or don't sync (big red dot). "Big red dot" is a technical term in the world of UI, trust me.
 Let's start with the first part: automating your user provisioning process. This is basic identity management workflow. In the case of EmpowerID, it is VISUAL
Let's start with the first part: automating your user provisioning process. This is basic identity management workflow. In the case of EmpowerID, it is VISUAL  The third part that is important is to integrate with all other aspects of Identity and Access Management (IAM). Most legacy applications (I'm looking at IBM and CA and Microsoft and Quest here) are the result of myriad acquisitions and mergers and the products are put together in a way that not all modules work together. EmpowerID is built from the ground up on a single code base and the platform shares common components like the metadirectory and RBAC engine and workflow studio.
The third part that is important is to integrate with all other aspects of Identity and Access Management (IAM). Most legacy applications (I'm looking at IBM and CA and Microsoft and Quest here) are the result of myriad acquisitions and mergers and the products are put together in a way that not all modules work together. EmpowerID is built from the ground up on a single code base and the platform shares common components like the metadirectory and RBAC engine and workflow studio. 
 It should be an identity ecosystem. When a user is initially provisioned from HR (or a contractor database or a customer self-registration), you apply an initial role to that user dynamically based on what you know about them. That role (or roles) determine in which systems the user needs to be provisioned. An example is: sales rep in Toledo will need an Active Directory account, an Exchange mailbox, an ERP account and a salesforce.com account.
It should be an identity ecosystem. When a user is initially provisioned from HR (or a contractor database or a customer self-registration), you apply an initial role to that user dynamically based on what you know about them. That role (or roles) determine in which systems the user needs to be provisioned. An example is: sales rep in Toledo will need an Active Directory account, an Exchange mailbox, an ERP account and a salesforce.com account.
 What goes up must come down. For every action there is an equal and opposite reaction. Every user provisioned is eventually deprovisioned. It's the circle of identity, a term I just made up.
What goes up must come down. For every action there is an equal and opposite reaction. Every user provisioned is eventually deprovisioned. It's the circle of identity, a term I just made up.
 Let's take my favorite and most frequent use case: the wild world of Salesforce.com! You want your users to be able to authenticate into salesforce without having to re-enter credentials or, worse yet, enter a completely different set of credentials. So you
Let's take my favorite and most frequent use case: the wild world of Salesforce.com! You want your users to be able to authenticate into salesforce without having to re-enter credentials or, worse yet, enter a completely different set of credentials. So you 
 Identity and access management (IAM) is a big concept. Google analytics tells me that there are 18,100 searches for this term each and every month. Gartner's definition is that "IAM ensures the right people have the right access to the right resources at the right time, enabling the right business outcomes." That is a big concept.
Identity and access management (IAM) is a big concept. Google analytics tells me that there are 18,100 searches for this term each and every month. Gartner's definition is that "IAM ensures the right people have the right access to the right resources at the right time, enabling the right business outcomes." That is a big concept.
 To paraphrase Gartner, Identity and Access Management is the act of getting the right people the right access to the right resources at the right time. Central to that concept is the right people.
To paraphrase Gartner, Identity and Access Management is the act of getting the right people the right access to the right resources at the right time. Central to that concept is the right people. You don't do it with cloud vendors or traditional IAM solutions. EmpowerID's tagline is a "New breed of Identity Management" and this is why. The platform was built from the ground up without the burdens of acquisitions or partnerships to create the full suite. So, the whole product line shares the same RBAC model, the same API layer, the same metadirectory, the same visual workflow designer. It is a true platform.
You don't do it with cloud vendors or traditional IAM solutions. EmpowerID's tagline is a "New breed of Identity Management" and this is why. The platform was built from the ground up without the burdens of acquisitions or partnerships to create the full suite. So, the whole product line shares the same RBAC model, the same API layer, the same metadirectory, the same visual workflow designer. It is a true platform. Your finance department is watching the cloud. Not because they are tech literate and following IT trends, but because they can cut your budget quickly with cloud applications. And it's up to you to help them before they help themselves.
Your finance department is watching the cloud. Not because they are tech literate and following IT trends, but because they can cut your budget quickly with cloud applications. And it's up to you to help them before they help themselves.
