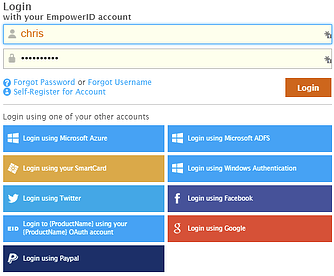
The SharePoint 2013 People Picker is the tool you use to find and select users, groups and claims to grant someone a permission to a site in SharePoint. The SharePoint 2013 People Picker is heavily dependent on how authentication is configured for your site so you need to ensure your SAML or claim provider is intelligent.
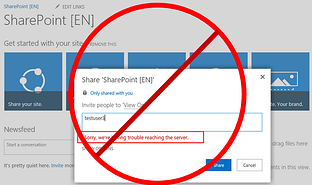
All claim providers created equally!
Today the most common issue SharePoint administrators find with an authentication claim provider is that any name you type in the People Picker, SharePoint will accept. Even worse, with a typical claims provider you can type nonsense and you will see two results, neither of them valid!
Credit:Kirk Evans Microsoft Blog
This is not because the SharePoint People Picker needs to be fixed, it's working as designed, it is a result of the claim provider.
The EmpowerID SharePoint Manager solves this problem, we have created the most intelligent claim provider in the market today. In doing so we set out to do 4 things which will have a huge impact on the day to day operations of your SharePoint site.
1. Create the most intelligent claim provider in the world. We didn't stop at providing intelligent responses to the query, we also segregate the data so that delegated administrators can only view results for data that they can see. This is a very important point, if a business partner administrator wants to grant someone rights to a site the EmpowerID data filtering and masking is still maintained.
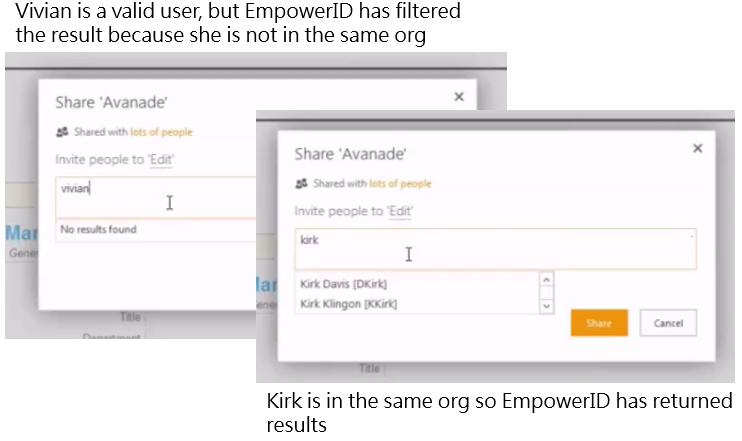
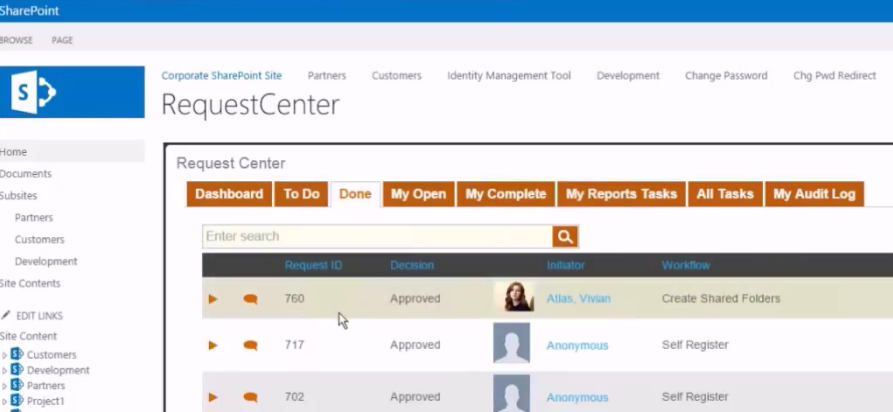
2. Provide SharePoint "web parts". This is technology that allows users to find new sites and request access to it. It also allows site administrators to approve site access, all directly within SharePoint.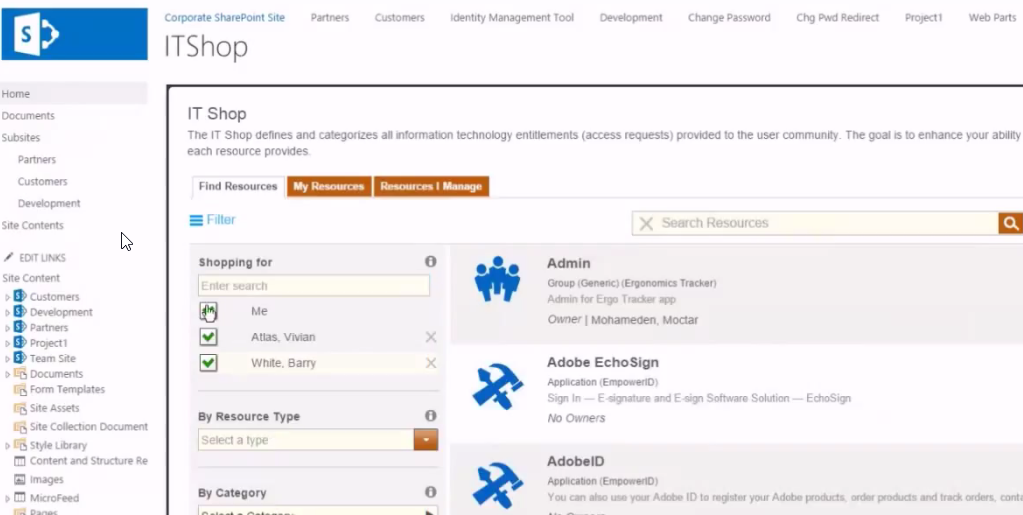
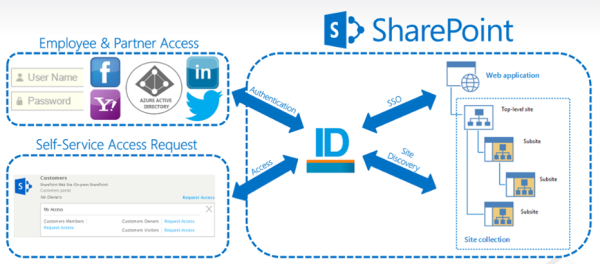
3. Fully support federated or claims based authentication into SharePoint. Users can authenticate with EmpowerID, bring their own social identity or use another.
4. Answer the "Why" question. Why does someone have access and when was it granted? The other side a SharePoint claim provider is tracking these finer details. EmpowerID includes full certification and attestation for SharePoint access, this provides your enterprise with a host of risk controls not previously available.
Want to know more?
Watch a previously recorded webinar that discusses these points here
click the button to request more information.

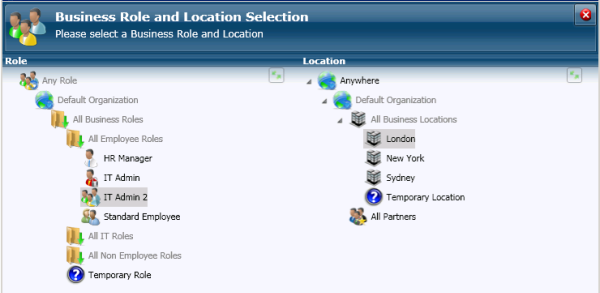

 Groups are not roles. Especially when they are static by nature. Over 85% of organizations manage groups manually, you can never really be certain that the correct users are in the correct groups if that is the case. You need your roles to be dynamic and rule-based. You need your RBAC to be augmented by ABAC for on the fly
Groups are not roles. Especially when they are static by nature. Over 85% of organizations manage groups manually, you can never really be certain that the correct users are in the correct groups if that is the case. You need your roles to be dynamic and rule-based. You need your RBAC to be augmented by ABAC for on the fly 
 EmpowerID makes role based SharePoint permissions possible by being a
EmpowerID makes role based SharePoint permissions possible by being a  The bane of every SharePoint project is permissions and rights. Access is controlled via SharePoint groups, these quirky little groups that exist in the SharePoint vacuum and only in the SharePoint vacuum. SharePoint 2010 introduced the ability to control access via Active Directory groups but gives no way to manage the membership of these groups. So you end up with site admins managing permissions manually or just letting it die on the vine.
The bane of every SharePoint project is permissions and rights. Access is controlled via SharePoint groups, these quirky little groups that exist in the SharePoint vacuum and only in the SharePoint vacuum. SharePoint 2010 introduced the ability to control access via Active Directory groups but gives no way to manage the membership of these groups. So you end up with site admins managing permissions manually or just letting it die on the vine.
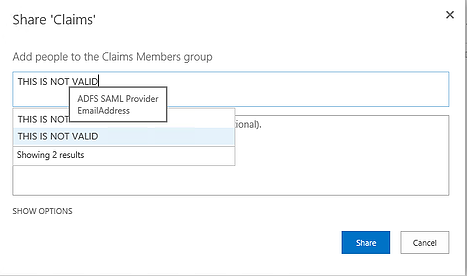
 SharePoint's People Picker is one of the strangest user interfaces in the world. A SharePoint site admin generally gives permissions to either SharePoint groups or Active Directory groups. But if he/she uses AD groups, he/she doesn't know who is a member.
SharePoint's People Picker is one of the strangest user interfaces in the world. A SharePoint site admin generally gives permissions to either SharePoint groups or Active Directory groups. But if he/she uses AD groups, he/she doesn't know who is a member. You have to make it easy for these users to access the correct SharePoint sites based on their role(s). An internal user needs certain access and an external user needs different access; it's like two sides to the same coin. For example, both need to access billing records but have different permissions on what they see.
You have to make it easy for these users to access the correct SharePoint sites based on their role(s). An internal user needs certain access and an external user needs different access; it's like two sides to the same coin. For example, both need to access billing records but have different permissions on what they see.
 You need to fully integrate
You need to fully integrate 

