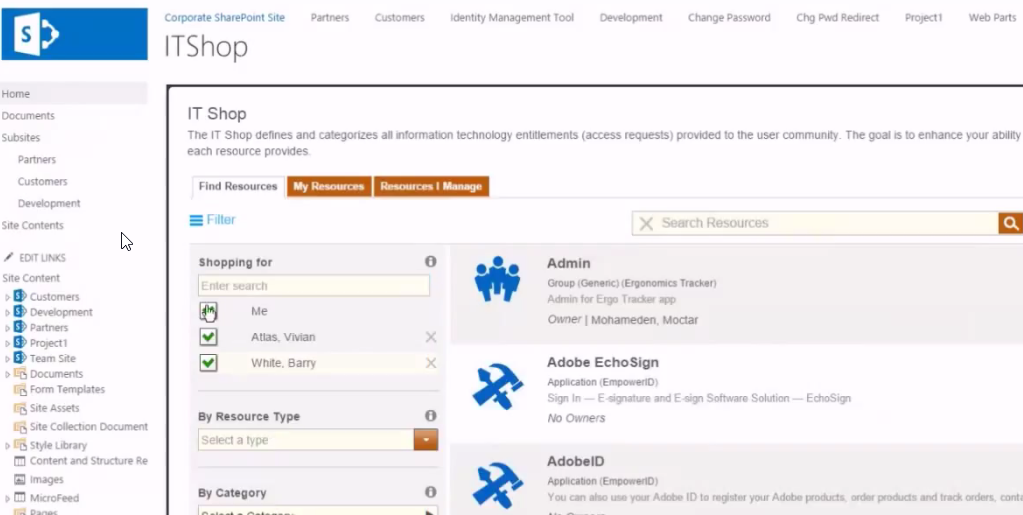
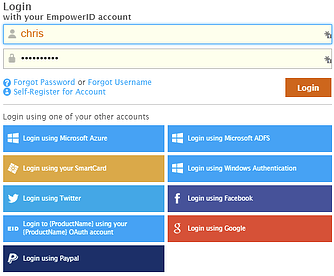
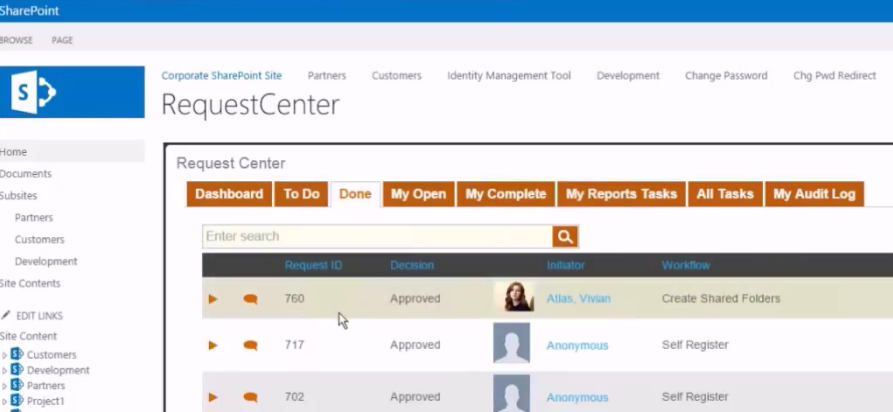
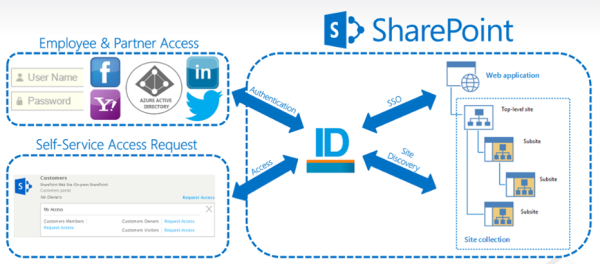
Microsoft Identity Manager (MIM) is a legacy identity management solution that has been around for a while. Organizations have been leveraging Microsoft Identity Manager (MIM) to centrally manage user identities, automate user provisioning and de-provisioning because of its relatively easy integration within the Microsoft Ecosystem. While it has served many organizations well, it lacks some of the essential features that modern identity management software offers.
Here are a few of the key features that MiM is missing compared to modern identity management solutions:
-
Cloud-First Approach:
MIM was designed for on-premises environments, and while it can be extended to support cloud-based environments, it lacks the cloud-first approach that modern identity management solutions offer. This can make it challenging to manage hybrid environments or to take full advantage of the cloud's scalability and flexibility. -
Flexible Identity Models:
MIM relies heavily on the Active Directory schema, which can limit its flexibility when it comes to managing non-AD identities such as contractors, partners, and customers. Modern identity management solutions offer more flexible identity models that can accommodate a wider range of identity types and sources. -
Self-Service Provisioning:
MiM requires significant manual intervention for account provisioning and access request workflows. Modern identity management solutions offer self-service capabilities that enable users to request and manage their own access, reducing the administrative burden on IT staff. -
Access Governance:
MiM offers basic access control functionality but lacks the more advanced access governance features found in modern identity management solutions. This includes capabilities such as entitlement cataloging, risk-based access certification, and access analytics. -
User Experience:
MIM's user interface is complex and challenging to use, MiM’s frustrating User Interface is a common gripe amongst all its customers. Modern identity management solutions offer streamlined user experiences that are more intuitive and user-friendly, reducing the learning curve and improving user adoption.
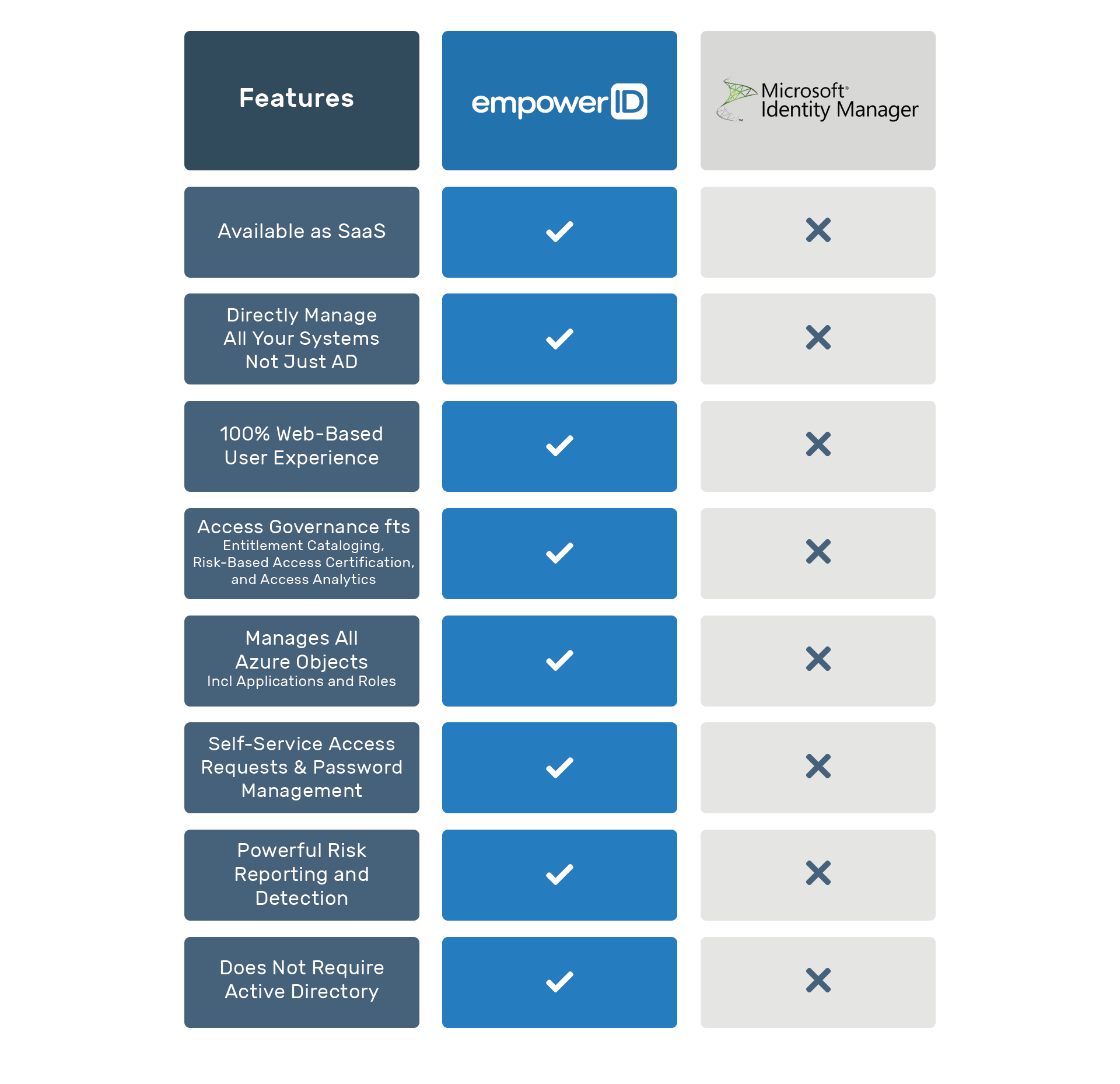
In summary, while MIM has been a reliable identity management solution for many organizations, it lacks some of the essential features that modern identity management solutions offer. If you're looking for a more flexible, scalable, and user-friendly identity management solution, it's time to consider upgrading to a modern identity management platform such as EmpowerID.
EmpowerID is a next-generation identity and access management platform that provides unparalleled flexibility and scalability. With EmpowerID, you can easily manage identities, applications, and resources across your entire organization, regardless of size or complexity.
Here are just a few reasons why you should consider moving to EmpowerID:
- Greater Flexibility: EmpowerID offers a highly configurable platform that can be customized to fit your organization's unique needs. With our flexible architecture and robust API, you can easily integrate EmpowerID with your existing systems and workflows.
- Improved Security: EmpowerID provides comprehensive security features, including multi-factor authentication, role-based access control, and privileged access management. With EmpowerID, you can ensure that your organization's sensitive data and resources are protected from unauthorized access.
- Simplified Administration and Self-Service: EmpowerID's intuitive user interface and streamlined workflows make it easy for administrators to manage user accounts, access requests, and other identity-related tasks. With EmpowerID, you can reduce the administrative burden on your IT team and improve overall efficiency.
- Better User Experience: EmpowerID offers a seamless user experience, with a single sign-on portal that provides easy access to all of your organization's applications and resources. With EmpowerID, your users can enjoy a streamlined, hassle-free experience that improves productivity and reduces frustration.
So if you're looking for a powerful, flexible, and easy-to-use identity management solution, look no further than EmpowerID. Contact us today to learn more about how EmpowerID can help you take control of your organization's identity and access management needs.