In the realm of cybersecurity, the Zero Trust model has emerged as a robust framework for enhancing security. A key aspect of this model is effective identity governance, which can be significantly streamlined and made more efficient through the use of proxy models and workflows.
Today we'll be exploring how these tools can be leveraged to bolster security and efficiency in identity governance within Zero Trust environments.
What are Proxy Models?
Proxy Models in identity governance can be likened to gatekeepers in a business organization, ensuring that only authorized individuals gain access to sensitive resources. Just as a gatekeeper verifies the identity and permissions of individuals before granting entry, proxy models act as intermediaries between users and the systems they wish to access. They authenticate and validate user identities, ensuring that only authorized personnel are granted appropriate access privileges.

The Power of Proxy Models
Proxy models provide a powerful tool for managing identities in a Zero Trust environment. By acting as an intermediary between users and resources, proxy models can enforce strict access controls, ensuring that users only have access to the resources they need. This approach significantly reduces the attack surface and helps to prevent unauthorized access.
Moreover, proxy models can help to alleviate some of the challenges of the cybersecurity labor shortage and skills gap. By reducing the need for costly IT staff with specific knowledge and training in each of the proxied systems, proxy models can help organizations to manage their resources more efficiently.
By implementing proxy models, businesses can establish a robust and secure system where user actions are monitored and controlled, mitigating the risk of unauthorized access and potential data breaches. Think of proxy models as vigilant guards, protecting your business assets and maintaining the integrity of your identity governance framework.
The Efficiency of Workflows
Workflows, particularly those that are automated, can greatly enhance efficiency in identity governance. By automating routine tasks, workflows can reduce the time and effort required to manage identities, freeing up IT staff to focus on more strategic tasks.
For instance, consider the process of onboarding a new employee. An automated workflow could streamline this process, ensuring that the new employee's identity is properly set up across all necessary systems. This not only saves time but also reduces the risk of errors that could lead to security vulnerabilities.
Practical Strategies for Implementation
Implementing proxy models and workflows in identity governance involves several key steps. First, organizations need to identify the resources that need to be managed and the users who will need access to these resources. Next, they need to define the access controls that will be enforced by the proxy models.
Once the proxy models are in place, organizations can then develop workflows to automate routine identity governance tasks. These workflows should be designed to be flexible and adaptable, allowing for changes in the organization's needs and circumstances.
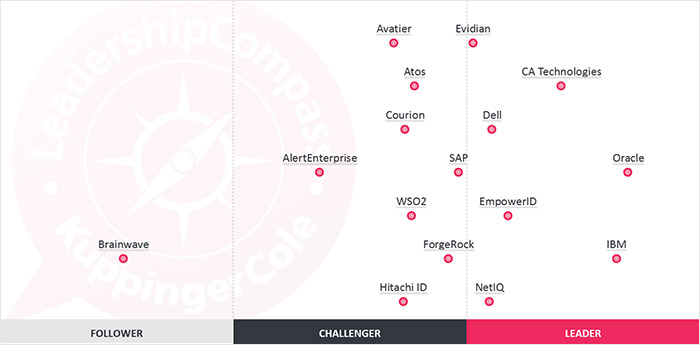
Today, most modern Identity Governance Platforms such as EmpowerID, are equipped with the requisite toolsets to implement these robust policy frameworks. Developing and integrating these systems separately might require significant planning, resources, and expertise for most organizations; instead opting for a modern Identity Platform that easily integrates with your enterprise's existing applications might be the way to go forward. The flexibility to easily handle on-prem, cloud, and even hybrid workflows paired with the ability to integrate with Microsoft 365, SAP, ServiceNow, SalesForce, etc creates an extremely compelling offering for any organization looking to manage their identities.
Conclusion
Proxy models and workflows offer powerful tools for enhancing security and efficiency in identity governance, particularly within Zero Trust environments. By implementing these tools and techniques, organizations can streamline their identity governance processes, improve their security posture, and better manage their resources. As the cybersecurity landscape continues to evolve, such strategies will be crucial for maintaining robust security.


 There are basically two types of group management: delegated group management and dynamic group management. Each has its place. There is a third facet to group management where you manage resources and what groups have access to the resource but that is slightly out of scope of our discussion here.
There are basically two types of group management: delegated group management and dynamic group management. Each has its place. There is a third facet to group management where you manage resources and what groups have access to the resource but that is slightly out of scope of our discussion here.
 Security groups seem like the best fit from 30,000 feet...both AD and Dynamics AX are part of the Microsoft stack. Microsoft has set it up so that if you are in a specific security group for Dynamics AX , you can authenticate and use Dynamics AX. But they stopped there, close but not close enough to actually use the solution for our client's needs.
Security groups seem like the best fit from 30,000 feet...both AD and Dynamics AX are part of the Microsoft stack. Microsoft has set it up so that if you are in a specific security group for Dynamics AX , you can authenticate and use Dynamics AX. But they stopped there, close but not close enough to actually use the solution for our client's needs.

 Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
 Active Directory groups are essential for fileshare permissions, for email communications, a few GPOs, and just plain useful for some application permissions. You can use them for SharePoint, though I recommend
Active Directory groups are essential for fileshare permissions, for email communications, a few GPOs, and just plain useful for some application permissions. You can use them for SharePoint, though I recommend 

 I'm being facetious of course, there's nobody in IT named Bob usually. But that's where your identity and access management platform comes in. It is busy giving people access to systems and you need to make sure that you are inserting the "right" into that sentence & process.
I'm being facetious of course, there's nobody in IT named Bob usually. But that's where your identity and access management platform comes in. It is busy giving people access to systems and you need to make sure that you are inserting the "right" into that sentence & process.
 The most obvious and important identity store to consider is Active Directory. There is a lot of identity information within there to delegate: mobile phone, home address, and other personal information. This is the sort of identity information your company needs and can only be provided by the users themselves. In fact, once they enter it via your self service interface, take advantage of this and flow the information back to the HR system.
The most obvious and important identity store to consider is Active Directory. There is a lot of identity information within there to delegate: mobile phone, home address, and other personal information. This is the sort of identity information your company needs and can only be provided by the users themselves. In fact, once they enter it via your self service interface, take advantage of this and flow the information back to the HR system.

