The introduction of the Network and Information Security Directive 2 (NIS2) marks a significant step forward in the European Union's efforts to strengthen cybersecurity across a broader range of sectors and organizations. With a compliance deadline set for October 17, 2024, NIS2 extends the foundational cybersecurity risk management measures and reporting obligations established by its predecessor, aiming to mitigate cyber threats and enhance the overall cybersecurity posture within the EU. This directive introduces more rigorous accountability through enhanced reporting obligations and increased sanctions, positioning NIS2 as a critical milestone for organizations committed to maintaining a robust cybersecurity framework.
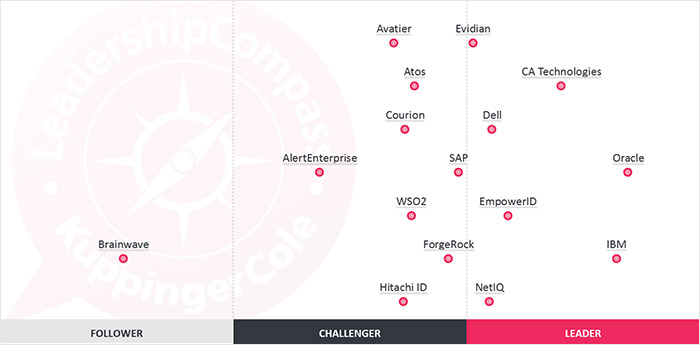
For enterprises, understanding NIS2's granular impact on daily operations is crucial for strategic planning and compliance. As a leader in the cybersecurity and identity management space, EmpowerID is uniquely positioned to guide and support organizations navigating the complexities of NIS2 compliance. This article delves into the specific changes brought about by NIS2 and how you can facilitate your organization's journey toward compliance and beyond. For business executives, download our NIS2 compliance checklist designed to offer strategic insights into the roles of personnel, planning processes, and collaborative partnerships essential for devising robust NIS2 compliance strategies.
A Closer Look at NIS2
NIS2, the successor to the original Network and Information Systems Directive, aims to fortify the cybersecurity framework across the EU. It introduces stringent requirements for a broader spectrum of sectors, demanding enhanced resilience against cyber-attacks. The directive's reach now extends to digital platforms, cloud computing services, and an expanded array of essential and important entities, signaling a comprehensive approach to cybersecurity.
One of the pivotal changes under NIS2 is the extension of its regulatory scope. Previously focused on critical sectors like energy, transport, and finance, NIS2 now encompasses a wider array of digital services, including social networks and data processing services. This broadened scope means that more enterprises will find themselves under the directive's purview, necessitating a reevaluation of their cybersecurity posture.
NIS2: A New Paradigm in Cybersecurity Regulation
NIS2 introduces several key enhancements designed to fortify the cybersecurity landscape for entities within the EU:
- Broader Sectoral Coverage: Expanding beyond the original directive, NIS2 includes additional sectors and digital services, broadening its applicability and ensuring that a wide array of organizations are covered under its protective umbrella.
- Advanced Cybersecurity Mandates: Organizations are now required to implement comprehensive risk assessments, multifactor authentication, secure protocols for sensitive data access, and robust supply chain security measures. Incident management and business continuity planning are also emphasized, representing a significant advancement from prior directives.
- Streamlined Incident Reporting: The directive mandates a more efficient and effective reporting mechanism for cybersecurity incidents, enhancing communication with national authorities.
- Stricter Penalties for Non-compliance: Reflecting the directive's commitment to cybersecurity, NIS2 establishes severe repercussions for non-compliance, including substantial fines and legal liabilities for organizational management
Strategic Implications for Daily Operations
For enterprise leaders, NIS2 introduces several strategic considerations that will influence day-to-day operations:
- Cybersecurity as a Continuous Process
The directive necessitates a shift towards continuous risk management and adaptation of cybersecurity measures. Enterprises must regularly update their risk assessments and security practices in response to evolving threats, integrating cybersecurity into the operational DNA of the organization.
- Enhanced Collaboration and Information Sharing
NIS2 encourages greater collaboration and information sharing among enterprises and between enterprises and national authorities. This requires establishing communication channels and protocols for sharing threat intelligence, which can enhance collective cybersecurity resilience but also demands careful handling of sensitive information.
- Operationalizing Compliance
Compliance with NIS2 is not a one-time effort but a continuous obligation. Enterprises must operationalize their compliance efforts, embedding them into daily workflows. This includes ongoing monitoring of cybersecurity practices, regular training for staff, and periodic audits to ensure adherence to the directive's requirements.
- Strategic Vendor Management
With the directive's focus on supply chain security, enterprises must scrutinize their vendors and partners more closely. This involves conducting cybersecurity assessments of third parties, renegotiating contracts to include cybersecurity clauses, and possibly reconfiguring supply chains to mitigate risks.
- Financial Planning and Resource Allocation
The financial implications of NIS2 compliance are significant. Enterprises must allocate resources not only for the initial implementation of required cybersecurity measures but also for their ongoing maintenance and the potential costs associated with incident response and recovery. Additionally, the risk of substantial fines for non-compliance necessitates a strategic approach to financial planning and risk management.
Preparing for NIS2 with EmpowerID
As the deadline for NIS2 compliance approaches, EmpowerID is ready to assist organizations in preparing for and achieving compliance. Our guiding principles for NIS2 readiness emphasize proactive defense, strategic planning, and the importance of leveraging the right partners and solutions. It's also important to consider how the principles of Zero Trust, a fundamental aspect of EmpowerID’s approach to security, naturally align with the objectives of NIS2 to bolster your organization’s defenses against evolving cyber threats.
EmpowerID's comprehensive suite of identity management and cybersecurity solutions offers a path to not just compliance but enhanced security and operational efficiency. By choosing EmpowerID, organizations can navigate the complexities of NIS2 with confidence, ensuring a secure, compliant, and resilient cybersecurity framework.
Don’t forget to grab your free copy of the NIS2 compliance checklist to make your compliance journey easier with our strategic insights.