Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
And that's one of the main issues with managing AD, it often falls into the help desks' hands. They get an email from HR saying to create some users. They get requests to add users to AD security groups. They might get an email that Jane Doe got promoted to a new job in Operations. And for all of these changes, they have to have access to Active Directory Users & Computers (ADUC).
Once you have access to ADUC, you have access to ADUC. By that I mean that the help desk user can not only create a new user but delete an OU. Not only can they add a member to a security group but they can make themselves a domain admin or member of the executive security group. It just isn't that safe or secure.
So you want to be able to delegate and automate your Active Directory management. Have end users have only the access they need to make changes. Give them a self service portal that follows pretty strong workflow rules, giving field level security to changes on their profile or their users. Give them the ability to request membership in some groups and not others. Allow them to manage the membership of a group that they own.
By using rights based approval routing, anything that user is allowed to do is done instantly. Anything that needs approval from another user is routed for their approval. Anything that they shouldn't even see (the distribution group of users on steps of discipline for example) never appears before them.
EmpowerID allows this self service management with a level of granularity and security and role based access control that makes ADUC completely irrelevant. Grant access only to make changes in AD that the user is allowed to.
But that doesn't cover everything. Automation is your other big step. Creating a user still shouldn't be done manually. You probably have an authoritative source like HR that can be inventoried to see if a new employee exists or if an existing employee has changed. Once the new user is inventoried, EmpowerID will provision the user into Active Directory or make changes to their job title or any other change.
These new or changed users will have a specific dynamic role and will be provisioned into the correct systems, given access to the right resources and be a productive member of the corporation immediately.
With the right combination of delegation and automation, you don't need to have ADUC access for any user. You can manage all of the AD objects and attributes without the "everything" access that comes with native tools like ADUC.
Take a look at our whitepaper on replacing ADUC and schedule a demonstration of how we can help you delegate and automate.

 Not all applications are created equal. Not all users are created equal. Different users need access to different applications; different users need different access to these applications. We call this
Not all applications are created equal. Not all users are created equal. Different users need access to different applications; different users need different access to these applications. We call this 
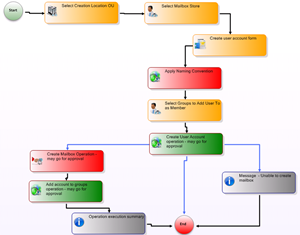 This provisioning workflow is designed around your business rules and processes. EmpowerID offers a visual workflow designer that has almost 400 out of the box templates and the power to customize each worfklow with 400 different actions or shapes.
This provisioning workflow is designed around your business rules and processes. EmpowerID offers a visual workflow designer that has almost 400 out of the box templates and the power to customize each worfklow with 400 different actions or shapes. Now if you want to automate the user account provisioning process, you need to account for any cloud applications the user has. These cloud applications have different UIs, are owned by different lines of business and generally add a wrinkle to your identity and access management that you just don't need.
Now if you want to automate the user account provisioning process, you need to account for any cloud applications the user has. These cloud applications have different UIs, are owned by different lines of business and generally add a wrinkle to your identity and access management that you just don't need.
 Talking to a client the other day about enterprise to cloud access, it became apparent that before considering cloud SSO, cloud provisioning needed to be taken care of. More than that, role based cloud provisioning.
Talking to a client the other day about enterprise to cloud access, it became apparent that before considering cloud SSO, cloud provisioning needed to be taken care of. More than that, role based cloud provisioning.
 Providing Active Directory self service gives you a good place to store this data. Most of these items have attributes in AD and you can easily synchronize that information from AD to your HRIS or emergency notification system. You can even then start making dynamic Active Directory groups based on the information.
Providing Active Directory self service gives you a good place to store this data. Most of these items have attributes in AD and you can easily synchronize that information from AD to your HRIS or emergency notification system. You can even then start making dynamic Active Directory groups based on the information.
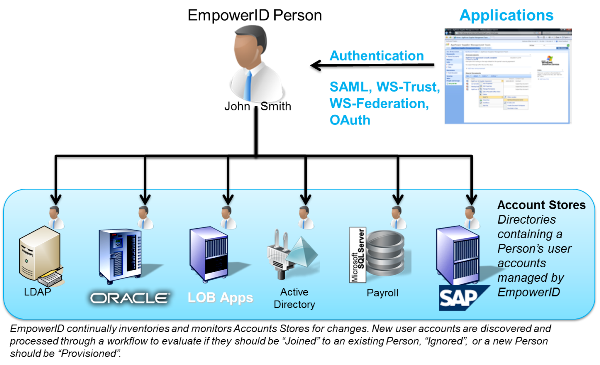
 Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.
Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.