Back in the old days, user account provisioning meant "get that guy an Active Directory account" {note: old days not that long ago}. And the world was easy, provision an Exchange mailbox and your user could get going, productive as the proverbial bee.
Today, you have bigger fish to fry with cloud applications, multiple AD user accounts, line of business applications, and myriad other accounts that need provisioning. This all has to be sorted out, provisioned based on roles (marketing probably doesn't need access to financial systems, engineering can probably do without SalesForce access for example) and kept constantly updated.
Having a "people directory" solves this. Each person has an account that is linked to all of their user accounts whether it be Active Directory (Exchange, Lync, etc), CRM, ERP, weird cloud applications. Workflow rules can provision the user from an authoritative source (usually the HR system) and give them all the accounts they need based on their role (I love role based provisioning!). A constant inventorying process will detect any changes and change access based on that.
Your user leaves the company? Boom! De-provision all of the accounts at once.
Take a look:
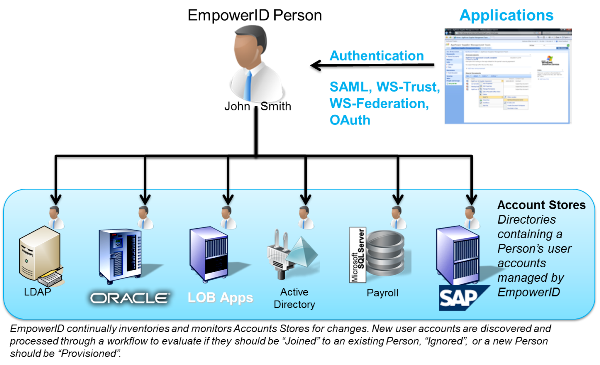
User provisioning and deprovisioning should be that simple and that automated. Joining user accounts, monitoring directories and databases for changes, keeping accounts active that should be active, inactive that should be inactive. All done because you have a "people directory."
The first time I saw that graphic, I already realized the benefits of this type of automated user account provisioning. I've seen enough complex corporate environments to know how important this is. But it was the box at the upper right that knocked my socks off.
Users can authenticate against this directory. That means that using SAML or WS-Trust or other standards, we can federate with any application that supports it. Users get not only the benefits of role based provisioning and RBAC, but single sign-on as well. And, the people directory obviously knows what apps they should have access to, heck, it provisioned those apps.
Let's summarize: lots of applications and systems, easy provisioning and deprovisioning, role based access control and federated single sign-on. Would it shock you if I said EmpowerID makes this easy and installs and configures in a fraction of the time you would expect? Let us show you, schedule a demo.
Tags: User provisioning, Identity and Access Management (IAM)


