Microsoft makes Office 365 pretty easy when you are already managing Active Directory with its DirSync utility. However, this doesn't always work if your users are not in AD or if you have multiple forests. So, how do you manage provisioning, group management and SSO to Office 365 without AD?
EmpowerID.
 Let's take the first use case, users that are not in AD but that need an O365 account. This happens often in franchises, education, manufacturing or when offering accounts to non-employees. EmpowerID's metadirectory stores a "person" object that is completely independent of AD, this user account can then be provisioned to O365 and updated through EmpowerID's HTML5 user interface.
Let's take the first use case, users that are not in AD but that need an O365 account. This happens often in franchises, education, manufacturing or when offering accounts to non-employees. EmpowerID's metadirectory stores a "person" object that is completely independent of AD, this user account can then be provisioned to O365 and updated through EmpowerID's HTML5 user interface.
Users have the ability to manage group membership, passwords (including self service password reset) and single sign-on to O365 with the EmpowerID credentials. All of these changes are made in the metadirectory which is synchronized directly to Office 365 without AD in between as well as direct Identity Administration where the workflows make live changes directly to Office 365 like we do to AD. Not all has to go through sync like FIM.
You can automate all of the provisioning/deprovisioning to the metadirectory based on a connector to any other system (student database for example). The EmpowerID Office 365 connector does all of the heavy lifting that DirSync does but adds the complete workflow and RBAC capability of EmpowerID. Without AD in the mix.
The other use case is one that a few customers have brought to us: Office 365 does not work with multiple AD forests unless you want to deal with FIM and the army of consultants / developers necessary to manage that. Again, the EmpowerID metadirectory solves this, easily connecting and synchronizing each AD forest into the metadirectory, creating a person object that joins user accounts in each forest.
The EmpowerID Office 365 connector then does all of the heavy lifting, provisioning accounts, offering password management, single sign-on and group management. Any changes you make can flow out to each AD forest as well.
The customers that have come to us for this scenario always point out the obvious, if they used FIM they are not future proofed, not only do they pay more for the initial deployment, but if there is another acquisition and another forest added, they have to start the whole process again with FIM. With EmpowerID, it is a matter of connecting another AD forest with the connector already in place. Easy peasy.
Office 365 is a great product (we use it internally) but there are limitations to deploying it with DirSync and some very specific use cases where it doesn't work. EmpowerID fixes those use cases while giving a huge number of other IAM platform advantages. Take the time for a demo of how we can manage O365 without AD and see how much more you can do with a robust single codebase IAM platform.

 When SSO projects come our way, the initial conversations are always around SAML federation, Web Access Management (WAM), or password vaulting. We talk about identity providers, service providers, SharePoint claims, and multi-factor authentication. Customers talk about their applications and user experience in SSO. What they don't bring up is how to manage those external users because other SSO vendors avoid that conversation like the plague.
When SSO projects come our way, the initial conversations are always around SAML federation, Web Access Management (WAM), or password vaulting. We talk about identity providers, service providers, SharePoint claims, and multi-factor authentication. Customers talk about their applications and user experience in SSO. What they don't bring up is how to manage those external users because other SSO vendors avoid that conversation like the plague.
 Imagine having your users empty their pockets at a big security checkpoint as they enter your building. What kinds of devices would you find? Tons of tablets, scads of smartphones, the rare Google Glass, and probably one guy who still has a pager. Make a stack of all of these and it's most likely taller than your building.
Imagine having your users empty their pockets at a big security checkpoint as they enter your building. What kinds of devices would you find? Tons of tablets, scads of smartphones, the rare Google Glass, and probably one guy who still has a pager. Make a stack of all of these and it's most likely taller than your building.


 The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.
The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.
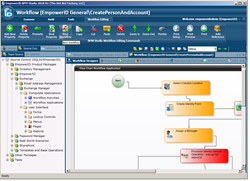 Within the EmpowerID platform is a visual workflow designer. This designer displays your identity workflows with traditional workflow shapes, decision trees and mimics how you would design it on a whiteboard or on a drafting table. It allows you to match your identity processes to your business processes, not the other way around. You simply drag and drop the shapes and the workflow does the work for you. Each "shape" has an identity action that you can easily configure. It is simple and easy and immensely powerful.
Within the EmpowerID platform is a visual workflow designer. This designer displays your identity workflows with traditional workflow shapes, decision trees and mimics how you would design it on a whiteboard or on a drafting table. It allows you to match your identity processes to your business processes, not the other way around. You simply drag and drop the shapes and the workflow does the work for you. Each "shape" has an identity action that you can easily configure. It is simple and easy and immensely powerful.
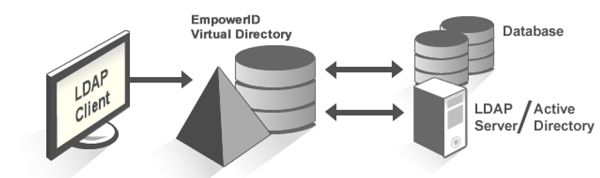
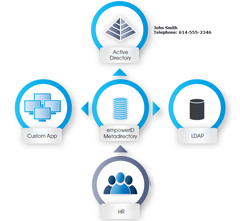 Having a hub and spoke solution allows you to easily flow attributes from the authoritative source to the metadirectory and back out to the appropriate identity stores. An example would be that HR is authoritative for a user's title, then empowerID metadirectory would inventory HR, see the change and update the user's "person" account in the metadirectory. With that change, it will need to be flowed out to the LDAP identity store and Active Directory.
Having a hub and spoke solution allows you to easily flow attributes from the authoritative source to the metadirectory and back out to the appropriate identity stores. An example would be that HR is authoritative for a user's title, then empowerID metadirectory would inventory HR, see the change and update the user's "person" account in the metadirectory. With that change, it will need to be flowed out to the LDAP identity store and Active Directory.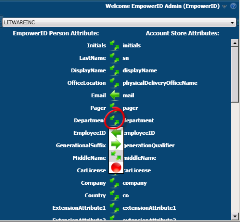 It is as simple as configuring the arrow to indicate the authoritative source. It can be authoritative from either identity store (arrow facing one way), last change wins (arrows facing both ways), or don't sync (big red dot). "Big red dot" is a technical term in the world of UI, trust me.
It is as simple as configuring the arrow to indicate the authoritative source. It can be authoritative from either identity store (arrow facing one way), last change wins (arrows facing both ways), or don't sync (big red dot). "Big red dot" is a technical term in the world of UI, trust me.
 It should be an identity ecosystem. When a user is initially provisioned from HR (or a contractor database or a customer self-registration), you apply an initial role to that user dynamically based on what you know about them. That role (or roles) determine in which systems the user needs to be provisioned. An example is: sales rep in Toledo will need an Active Directory account, an Exchange mailbox, an ERP account and a salesforce.com account.
It should be an identity ecosystem. When a user is initially provisioned from HR (or a contractor database or a customer self-registration), you apply an initial role to that user dynamically based on what you know about them. That role (or roles) determine in which systems the user needs to be provisioned. An example is: sales rep in Toledo will need an Active Directory account, an Exchange mailbox, an ERP account and a salesforce.com account.


