 Listening to a Gartner webinar on Identity & Access Management this morning, this line struck me: "Cloud breaks legacy IAM approaches". Because it is true, most legacy IAM vendors are stuck with old codebases, old products, and components that have been cobbled together to form "frankenproducts". They have no more chance of seamlessly managing cloud identities than they do of installing and configuring on time and on budget.
Listening to a Gartner webinar on Identity & Access Management this morning, this line struck me: "Cloud breaks legacy IAM approaches". Because it is true, most legacy IAM vendors are stuck with old codebases, old products, and components that have been cobbled together to form "frankenproducts". They have no more chance of seamlessly managing cloud identities than they do of installing and configuring on time and on budget.
Cloud identity management is hindered by these old legacy approaches to IAM. The industry is, in many ways, in the exact same position as it was ten years ago with on premise applications. The solution to each cloud problem (SSO, provisioning, access governance) is met by a different vendor, or a different product within the legacy vendor's "suite".
In the webinar, Gregg Kreizman says that the larger vendors "have been able to provide functionally across the IAM function set through acquisition, through some development. They have slowly and somewhat shortly have been incorporating these things into suites, some of them very loosely integrated some of them better than others."
The problem, though, isn't the legacy IAM vendors. The problem is that it's easier to justify a legacy IAM vendor to your CFO, despite the higher cost and lengthy deployment. Gregg also says, "I hope no one would base election or implementation decisions based on identifying the largest vendors only." For the exact reasons above.
Because there are approaches to the cloud that isn't burdened with tons of legacy baggage. To a newer, more modern IAM platform, that cloud application is just another identity store. In some ways, even easier to work with due to its requirements for SDKs and APIs.
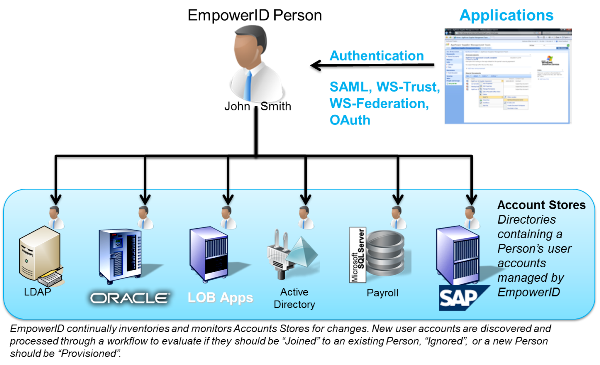
Having a platform that integrates easily between cloud and on-premise brings you up to date in Identity & Access Management. EmpowerID has connectors to most major cloud applications and a flexible connector platform to build new ones for others. Provisioning, deprovisioning, updates are all seamless and fit into your IAM workflows the same as an on premise application.
But that isn't what breaks most legacy applications, it's the integration of IAM functionality. Provision a cloud user AND provide cloud single sign-on. Role based provisioning for cloud applications that integrates with role based adaptive authentication for cloud applications. These are the things that test your ability to manage identities in the cloud.
Chances are the legacy IAM "frankenproduct" cannot do that for on premise applications, much less the cloud. The only way to make this sort of modern IAM functionality to happen is to have a purpose-built, single codebase IAM platform. One that can easily have the roles engine speak to the workflow engine speak to the metadirectory. One that can insert a second factor authentication shape into an access authorization workflow. One that can provision any number of cloud or on premise applications within a single visually based workflow. In short, EmpowerID: the modern IAM approach.
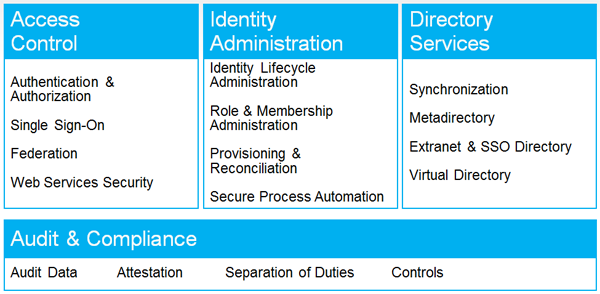
That is a list of the capabilities of EmpowerID. The same platform manages all of this functionality. What changes is the workflow shapes (think of them like identity management actions) that are exposed by module. For example, if you have the User Manager and Group Manager modules, you can insert a dynamic group membership provisioning shape into your user provisioning workflow, allowing provisioning to extend to groups. If you have User Manager and SSO Manager, you can check a user's role and demand additional authentication before passing them along to the cloud application if the role and application mix is identified as highly secure.
The cloud doesn't have to break your IAM. In fact, IAM is too important to let it. What you need is an approach that is modern, flexible and built to manage change in both identities and your business process. Seeing is believing, we can demonstrate IAM that extends seamlessly to the cloud with EmpowerID. Schedule a demo and you will never think about going back to those legacy IAM approaches.
 Prior to The Dot Net Factory, I spent over six years helping healthcare organizations implement software solutions. During that time I helped doctors, frontline care workers, financial staff, even maintence staff to replace paper documentation systems with electronic documentation solutions. Now my time in Identity & Access Management (IAM) has helped me to bridge the gap between healthcare and IAM. Here is a list of common complaints that I heard in the healthcare world:
Prior to The Dot Net Factory, I spent over six years helping healthcare organizations implement software solutions. During that time I helped doctors, frontline care workers, financial staff, even maintence staff to replace paper documentation systems with electronic documentation solutions. Now my time in Identity & Access Management (IAM) has helped me to bridge the gap between healthcare and IAM. Here is a list of common complaints that I heard in the healthcare world:
 Authentication is a key point on this security balance beam. Password complexity, multi factor authentication, adaptive authentication,
Authentication is a key point on this security balance beam. Password complexity, multi factor authentication, adaptive authentication, 
 Identity and access management (IAM) is a big concept. Google analytics tells me that there are 18,100 searches for this term each and every month. Gartner's definition is that "IAM ensures the right people have the right access to the right resources at the right time, enabling the right business outcomes." That is a big concept.
Identity and access management (IAM) is a big concept. Google analytics tells me that there are 18,100 searches for this term each and every month. Gartner's definition is that "IAM ensures the right people have the right access to the right resources at the right time, enabling the right business outcomes." That is a big concept.
 To paraphrase Gartner, Identity and Access Management is the act of getting the right people the right access to the right resources at the right time. Central to that concept is the right people.
To paraphrase Gartner, Identity and Access Management is the act of getting the right people the right access to the right resources at the right time. Central to that concept is the right people.
 Reading an article by Earl Perkins titled
Reading an article by Earl Perkins titled 
 The first part that is out of control is that individual business units can go out and contract with a cloud application; they don't necessarily need to rely on IT to install it and configure it. They usually get a web-based management console and take to doing the provisioning & deprovisioning manually despite there being a much smarter way to handle it.
The first part that is out of control is that individual business units can go out and contract with a cloud application; they don't necessarily need to rely on IT to install it and configure it. They usually get a web-based management console and take to doing the provisioning & deprovisioning manually despite there being a much smarter way to handle it.

 Until you observe and measure your IAM practices and policies, you don't know if the right people have the right access. And you don't know if the wrong people got the wrong access. That is where auditing actually helps your business, not just satisfying a regulatory requirement.
Until you observe and measure your IAM practices and policies, you don't know if the right people have the right access. And you don't know if the wrong people got the wrong access. That is where auditing actually helps your business, not just satisfying a regulatory requirement.
 Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.

