Today, The Dot Net Factory releases EmpowerID 2013 for general availability. Building on its industry leading visual workflow platform, EmpowerID expands Identity & Access Management (IAM) to manage the two hottest trends in the market: mobility and single sign-on.

EmpowerID is innovating with the changes in today’s business climate. More users are using mobile devices, requiring more flexible and secure authentication, and demanding a single username and password. Users no longer means just your employees, you need a way to manage the identities and login experience for customers, partners and other external users. EmpowerID 2013 provides new exciting features to match these changing needs.
New in EmpowerID 2013
- Web Access Management (WAM) to complement Federated SSO
- Virtual directory LDAP server built on Node.js
- HTML5 interface for a complete mobile experience
- Forced device registration for strong authentication
- OATH compliant server for software and hardware Time Based One Time Passwords (for web login, RADIUS login, LDAP and others)
- Full smart card login support
- FIPS compliance
The balance between security and productivity is a challenge for all businesses, EmpowerID provides a critical fulcrum by getting your users the correct access exactly when they need it. From authentication to authorization to actually getting work done, your users need to have the correct permissions, have access to the correct systems, and know how to manage this access. EmpowerID is the only Identity Management platform that maps these needs to your business processes.
These new features give more flexibility in how to manage users identities and how the users can access resources. Coupled with EmpowerID’s already existing extensive collection of identity workflows, full rights based access control, and metadirectory, these new features will allow companies to keep up with the needs of their employees.

 The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.
The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.
 Additionally, the applications they are accessing are growing more varied and widespread. You have legacy applications, cloud applications, web applications, and mobile applications. Organizations demand an IAM platform that can authenticate and authorize not against the ones that support a specific standard, but all of them.
Additionally, the applications they are accessing are growing more varied and widespread. You have legacy applications, cloud applications, web applications, and mobile applications. Organizations demand an IAM platform that can authenticate and authorize not against the ones that support a specific standard, but all of them.
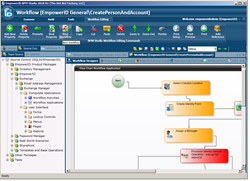 Within the EmpowerID platform is a visual workflow designer. This designer displays your identity workflows with traditional workflow shapes, decision trees and mimics how you would design it on a whiteboard or on a drafting table. It allows you to match your identity processes to your business processes, not the other way around. You simply drag and drop the shapes and the workflow does the work for you. Each "shape" has an identity action that you can easily configure. It is simple and easy and immensely powerful.
Within the EmpowerID platform is a visual workflow designer. This designer displays your identity workflows with traditional workflow shapes, decision trees and mimics how you would design it on a whiteboard or on a drafting table. It allows you to match your identity processes to your business processes, not the other way around. You simply drag and drop the shapes and the workflow does the work for you. Each "shape" has an identity action that you can easily configure. It is simple and easy and immensely powerful.

 Just don't stop at Active Directory. There are more passwords out there, a lot more. A study of just
Just don't stop at Active Directory. There are more passwords out there, a lot more. A study of just 
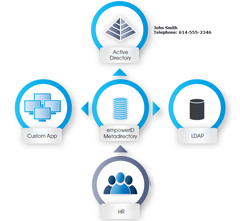 Having a hub and spoke solution allows you to easily flow attributes from the authoritative source to the metadirectory and back out to the appropriate identity stores. An example would be that HR is authoritative for a user's title, then empowerID metadirectory would inventory HR, see the change and update the user's "person" account in the metadirectory. With that change, it will need to be flowed out to the LDAP identity store and Active Directory.
Having a hub and spoke solution allows you to easily flow attributes from the authoritative source to the metadirectory and back out to the appropriate identity stores. An example would be that HR is authoritative for a user's title, then empowerID metadirectory would inventory HR, see the change and update the user's "person" account in the metadirectory. With that change, it will need to be flowed out to the LDAP identity store and Active Directory.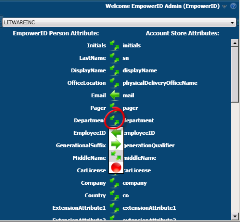 It is as simple as configuring the arrow to indicate the authoritative source. It can be authoritative from either identity store (arrow facing one way), last change wins (arrows facing both ways), or don't sync (big red dot). "Big red dot" is a technical term in the world of UI, trust me.
It is as simple as configuring the arrow to indicate the authoritative source. It can be authoritative from either identity store (arrow facing one way), last change wins (arrows facing both ways), or don't sync (big red dot). "Big red dot" is a technical term in the world of UI, trust me.