Andras Cser of Forrester writes that XACML is Dead. The first analyst question I was asked as head of marketing at EmpowerID was, "do you support XACML?" The easy answer was (and is), "we will when application vendors do." Andras' first point as the cause of the death of XACML: "Lack of broad adoption."
Andras' second point is the one that really gets to the technical heart of the matter rather than the logistical: XACMML's "inability to serve the federated, extended enterprise." Identity and Access Management (IAM) has moved way beyond the borders of an Active Directory forest. Organizations are managing their internal users, partners, customers, and contractors and need a flexible authentication and authorization system that can accomodate the unique needs of each constituency.
 Additionally, the applications they are accessing are growing more varied and widespread. You have legacy applications, cloud applications, web applications, and mobile applications. Organizations demand an IAM platform that can authenticate and authorize not against the ones that support a specific standard, but all of them.
Additionally, the applications they are accessing are growing more varied and widespread. You have legacy applications, cloud applications, web applications, and mobile applications. Organizations demand an IAM platform that can authenticate and authorize not against the ones that support a specific standard, but all of them.
So, while some analysts have been trumpeting loudly that XACML is going to make authorization easy and standards based, the market and forward thinking analysts like Andras have realized that IAM in today's world is too complicated for it.
Unfortunately, this leaves us at the question: how the heck do we manage authorization in this new complicated world? We believe that EmpowerID has hit on the best way to manage it, by integrating roles into every single aspect of IAM from provisioning to authentication to password reset to SSO. Making your roles pervasive in all aspects of IAM gives you flexibility on the who has access to what and when question.
EmpowerID's role engine was designed as part of a purpose-built single codebase IAM platform; roles fit in as an integral part of each IAM function. Our polyarchical role structure is flexible and intuitive, allowing organizations a tremendous amount of flexibility in how they apply permissions and authorization.
When roles are too static, we combine ABAC with RBAC to give runtime decisions based on attributes in any connected system, giving even more flexibility.
EmpowerID includes an advanced authorization policy engine that allows organizations to define a user’s access to a diverse set of corporate and cloud-hosted resources via flexible RBAC and ABAC rules. This “resultant access” information is then either consumed or “pulled” by systems that support leveraging an external authorization engine to make access decisions or “pushed” down onto systems that don’t.
Read more about EmpowerID's authorization engine, schedule a demo, or request a whitepaper on Best Practices in Enterprise Authorization. XACML isn't walking through that door ready to save enterprise authorization, take a look at a solution that will.

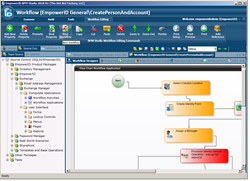 Within the EmpowerID platform is a visual workflow designer. This designer displays your identity workflows with traditional workflow shapes, decision trees and mimics how you would design it on a whiteboard or on a drafting table. It allows you to match your identity processes to your business processes, not the other way around. You simply drag and drop the shapes and the workflow does the work for you. Each "shape" has an identity action that you can easily configure. It is simple and easy and immensely powerful.
Within the EmpowerID platform is a visual workflow designer. This designer displays your identity workflows with traditional workflow shapes, decision trees and mimics how you would design it on a whiteboard or on a drafting table. It allows you to match your identity processes to your business processes, not the other way around. You simply drag and drop the shapes and the workflow does the work for you. Each "shape" has an identity action that you can easily configure. It is simple and easy and immensely powerful.

 Just don't stop at Active Directory. There are more passwords out there, a lot more. A study of just
Just don't stop at Active Directory. There are more passwords out there, a lot more. A study of just 
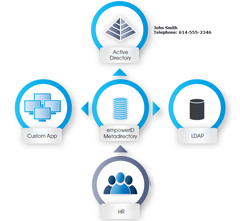 Having a hub and spoke solution allows you to easily flow attributes from the authoritative source to the metadirectory and back out to the appropriate identity stores. An example would be that HR is authoritative for a user's title, then empowerID metadirectory would inventory HR, see the change and update the user's "person" account in the metadirectory. With that change, it will need to be flowed out to the LDAP identity store and Active Directory.
Having a hub and spoke solution allows you to easily flow attributes from the authoritative source to the metadirectory and back out to the appropriate identity stores. An example would be that HR is authoritative for a user's title, then empowerID metadirectory would inventory HR, see the change and update the user's "person" account in the metadirectory. With that change, it will need to be flowed out to the LDAP identity store and Active Directory.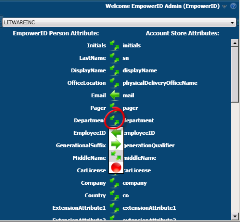 It is as simple as configuring the arrow to indicate the authoritative source. It can be authoritative from either identity store (arrow facing one way), last change wins (arrows facing both ways), or don't sync (big red dot). "Big red dot" is a technical term in the world of UI, trust me.
It is as simple as configuring the arrow to indicate the authoritative source. It can be authoritative from either identity store (arrow facing one way), last change wins (arrows facing both ways), or don't sync (big red dot). "Big red dot" is a technical term in the world of UI, trust me.

 The third part that is important is to integrate with all other aspects of Identity and Access Management (IAM). Most legacy applications (I'm looking at IBM and CA and Microsoft and Quest here) are the result of myriad acquisitions and mergers and the products are put together in a way that not all modules work together. EmpowerID is built from the ground up on a single code base and the platform shares common components like the metadirectory and RBAC engine and workflow studio.
The third part that is important is to integrate with all other aspects of Identity and Access Management (IAM). Most legacy applications (I'm looking at IBM and CA and Microsoft and Quest here) are the result of myriad acquisitions and mergers and the products are put together in a way that not all modules work together. EmpowerID is built from the ground up on a single code base and the platform shares common components like the metadirectory and RBAC engine and workflow studio. 
 Groups are not roles. Especially when they are static by nature. Over 85% of organizations manage groups manually, you can never really be certain that the correct users are in the correct groups if that is the case. You need your roles to be dynamic and rule-based. You need your RBAC to be augmented by ABAC for on the fly
Groups are not roles. Especially when they are static by nature. Over 85% of organizations manage groups manually, you can never really be certain that the correct users are in the correct groups if that is the case. You need your roles to be dynamic and rule-based. You need your RBAC to be augmented by ABAC for on the fly 

