 Active Directory password management is a three part problem: self service password reset; password synchronization to other applications; and to eliminate passwords entirely!!!!
Active Directory password management is a three part problem: self service password reset; password synchronization to other applications; and to eliminate passwords entirely!!!!
The first two are part of password management, but the third is the trend for forward looking IT organizations. Let's talk about self service password reset and synchronization first and then talk about how to eliminate passwords completely.
Most users start the day with their Active Directory password. And most users will eventually forget that password or get locked out. To delegate the reset and unlocking, you need to have a way to verify (authenticate) who that user is before letting them change the password. There are a few ways to do this:
- the traditional knowledge based question and answer
- second factor authentication -- not something they know but something they have like a mobile phone or software token
- help desk questions
The key to making self service password reset work is to force users to enroll. EmpowerID builds an enrollment check into each authentication workflow; if the user is not enrolled, they will be re-directed to an enrollment form, keeping your password management system from becoming shelfware.
Second factor authentication likewise should have choices, either using EmpowerID's built in OATH tokens, sending a PIN to an SMS gateway, or accepting a hardware token. Adding this on top of the knowledge based questions helps ensure that your user is who they say they are.
Users will still forget their own knowledge based answers or have a phone battery die so you need a help desk backup. EmpowerID does not let the help desk see the knowledge based questions and answers so we provide a set that is visible to the help desk to aid in verifying the user's identity. Once verified, the help desk can easily reset or unlock the account.
For most password management solutions, this is as far as it extends: Active Directory. Since EmpowerID is a full IAM platform with connectors into almost any cloud or on-premise application, passwords can be synchronized to those applications. For example, if a user has an AD account, a Google apps account, and three line of business accounts, EmpowerID can synchronize that password from AD upon reset and ensure that the user has a single cohesive password meeting all of the password complexity rules. This is extremely valuable for your end users.
But why stop there. Single sign on can eliminate the need to even have all of those passwords. If your applications can be federated with SAML or OAuth or any other federation standard, EmpowerID can authenticate your user with their AD credentials, then pass a token to the application to authenticate them there without your user ever using or needing to know that other password. If the applicaiton isn't federated, EmpowerID also offers Web Access Management (WAM), secure password vaulting, and a built-in virtual directory for authentication.
Eliminating the need for all of these passwords is definitely preferable and adds security. With EmpowerID you can also have role based or resource based step up authentication, requiring a second factor for more secure assets. Users don't know their passwords so deprovisioning is more thorough with fewer moving parts.
EmpowerID is a single code base, purpose built Identity & Access Management platform that performs all of these functions seamlessly and interoperably. Don't fall into a trap of buying a password management software that doesn't do everything you need it to. Take a look at EmpowerID and see how you can solve all of the password challenges.


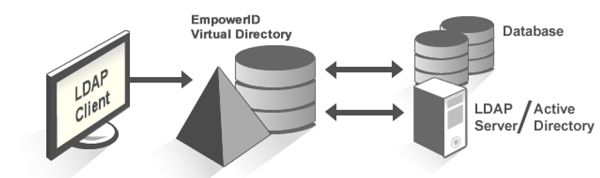
 Let's take the first use case, users that are not in AD but that need an O365 account. This happens often in franchises, education, manufacturing or when offering accounts to non-employees. EmpowerID's metadirectory stores a "person" object that is completely independent of AD, this user account can then be provisioned to O365 and updated through EmpowerID's HTML5 user interface.
Let's take the first use case, users that are not in AD but that need an O365 account. This happens often in franchises, education, manufacturing or when offering accounts to non-employees. EmpowerID's metadirectory stores a "person" object that is completely independent of AD, this user account can then be provisioned to O365 and updated through EmpowerID's HTML5 user interface.
 When SSO projects come our way, the initial conversations are always around SAML federation, Web Access Management (WAM), or password vaulting. We talk about identity providers, service providers, SharePoint claims, and multi-factor authentication. Customers talk about their applications and user experience in SSO. What they don't bring up is how to manage those external users because other SSO vendors avoid that conversation like the plague.
When SSO projects come our way, the initial conversations are always around SAML federation, Web Access Management (WAM), or password vaulting. We talk about identity providers, service providers, SharePoint claims, and multi-factor authentication. Customers talk about their applications and user experience in SSO. What they don't bring up is how to manage those external users because other SSO vendors avoid that conversation like the plague.
 Single sign-on does not have a magic bullet; instead, it requires a swiss army knife. Meaning many different ways to get users authenticated into an application using only one set of credentials. A German partner of ours calls this
Single sign-on does not have a magic bullet; instead, it requires a swiss army knife. Meaning many different ways to get users authenticated into an application using only one set of credentials. A German partner of ours calls this 
 Imagine having your users empty their pockets at a big security checkpoint as they enter your building. What kinds of devices would you find? Tons of tablets, scads of smartphones, the rare Google Glass, and probably one guy who still has a pager. Make a stack of all of these and it's most likely taller than your building.
Imagine having your users empty their pockets at a big security checkpoint as they enter your building. What kinds of devices would you find? Tons of tablets, scads of smartphones, the rare Google Glass, and probably one guy who still has a pager. Make a stack of all of these and it's most likely taller than your building.



 The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.
The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.

