An OATH token is a secure one time password that can be used for two factor authentication. The first factor is something you know (a password, mother's maiden name, the whereabouts of Jimmy Hoffa) while the second factor is something you have (a smartphone, email address, etc.). The OATH token is sent to something you have as a one time password to increase security in authentication.
 The OATH encryption algorithm is an open source standard and, as such, is widely available. EmpowerID ships with an OATH server to encrypt the OATH token while clients such as Google Authenticator are free and widely available for smart phones and tablets.
The OATH encryption algorithm is an open source standard and, as such, is widely available. EmpowerID ships with an OATH server to encrypt the OATH token while clients such as Google Authenticator are free and widely available for smart phones and tablets.
When the OATH server is combined with a sophisticated Identity & Access Management platform like EmpowerID, it opens up a wide range of uses for multi factor authentication. You don't have to broadly apply the increased level of authentication across all use cases; rather, you can choose the resources or users/roles that require enhanced security and apply two factor authentication strategically.
Since EmpowerID ships with multi-factor authentication as part of the base platform, we see a lot of use cases on how organizations apply OATH tokens.
Self service password reset - When users are locked out or forget their passwords, you need an additional means of verifying their identity. The traditional method is a series of knowledge based questions (mother's maiden name, eye color, etc). However, since most of this information can be gleaned from social media profiles, an OATH token as a second factor is almost mandatory to determine the user's identity.
Step up authentication - Once your users are already authenticated, you may want to increase the level of security based on what they are accessing. An example of this is when your user is attempting to access the financial reports for the 10K report. They have already entered their username and password, but you want to have that second factor for both security and auditing reasons when they access a resource with a higher security level.
Single sign on to cloud applications - This use case is similar to the previous step up authentication, but is more broadly applied. If you are offering single sign on (SSO) to internal applications, you might want to step up the authentication before leaving the network to access cloud applications. This extra level of authentication coupled with Federation or Web Access Management keeps your SaaS applications doubly secure and your CISO happy with precautions you are taking with the cloud.
Admin or executive accounts -I have always found it interesting that the users with the highest privileges tend to get away with the lowest security -- admins because they control security and CxOs because they sign the admins' checks. These are exactly the users who should have multi factor authentication and OATH tokens are a fairly innocuous way to deliver that security. Plus, it gives them a chance to look at their phones in meetings!
After x number of incorrect authentication attempts - This use case requires a fairly powerful workflow based IAM platform like EmpowerID that can re-route the authentication requirements based on calculations or an algorithm. This can be applied to any of the use cases above but is especially useful to prevent hacking attempts.
OATH tokens as second factor authentication are incredibly useful but it's more than just spinning up an OATH server. It needs to be integrated in with your IAM platform to be able to strategically and surgically apply its extra level of security and protection. If you roll it out en masse, you will have a user revolt. If you apply it in a way that makes sense to the users without an undue burden on them, you win and security wins.
EmpowerID's extensive and customizable visual Identity Management workflows have multiple second factor authentication shapes out of the box, allowing you to simply select a template, configure it for the use case you need and get the most out of OATH and two factor authentication.

 There are basically two types of group management: delegated group management and dynamic group management. Each has its place. There is a third facet to group management where you manage resources and what groups have access to the resource but that is slightly out of scope of our discussion here.
There are basically two types of group management: delegated group management and dynamic group management. Each has its place. There is a third facet to group management where you manage resources and what groups have access to the resource but that is slightly out of scope of our discussion here.
 I like to think that I am unique. However, to my IT, security and identity teams, I am just a mix of sales, marketing, management and location roles. Knowing those four things about me can generally define what system access I will need.
I like to think that I am unique. However, to my IT, security and identity teams, I am just a mix of sales, marketing, management and location roles. Knowing those four things about me can generally define what system access I will need.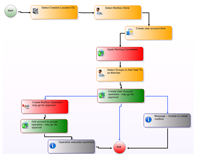 As you are designing these role based user provisioning rules, you are probably mapping them on a whiteboard. EmpowerID's visual workflow platform actually allows you to drag and drop shapes (identity actions such as provision account, go for approval, etc) exactly as you are drawing it. Though it is most likely more colorful and exciting in EmpowerID!
As you are designing these role based user provisioning rules, you are probably mapping them on a whiteboard. EmpowerID's visual workflow platform actually allows you to drag and drop shapes (identity actions such as provision account, go for approval, etc) exactly as you are drawing it. Though it is most likely more colorful and exciting in EmpowerID!
 In a perfect world, all of your applications would run on one OS, built by one vendor and speak to each other seamlessly. Every user of every application would have the correct level of access and sign on easily with a single set of secure credentials. Of course, this perfect world doesn't exist and will never exist.
In a perfect world, all of your applications would run on one OS, built by one vendor and speak to each other seamlessly. Every user of every application would have the correct level of access and sign on easily with a single set of secure credentials. Of course, this perfect world doesn't exist and will never exist.
 The first two Identity Management hurdles you have to overcome are provisioning and Single Sign-on. Without proper IdM planning you could very easily end up back in the dark ages of manual provisioning for your cloud applications.
The first two Identity Management hurdles you have to overcome are provisioning and Single Sign-on. Without proper IdM planning you could very easily end up back in the dark ages of manual provisioning for your cloud applications.
 Security groups seem like the best fit from 30,000 feet...both AD and Dynamics AX are part of the Microsoft stack. Microsoft has set it up so that if you are in a specific security group for Dynamics AX , you can authenticate and use Dynamics AX. But they stopped there, close but not close enough to actually use the solution for our client's needs.
Security groups seem like the best fit from 30,000 feet...both AD and Dynamics AX are part of the Microsoft stack. Microsoft has set it up so that if you are in a specific security group for Dynamics AX , you can authenticate and use Dynamics AX. But they stopped there, close but not close enough to actually use the solution for our client's needs.
 Where we always do better than our competition is our IAM implementation plan. We believe in putting the full solution and plan and cost and SOW up front to help make the decision easier for our clients. Other vendors don't always do that; if you found this blog post by searching for IAM implementation plan then you might already realize that. Here are the items to consider when looking for an implementation plan from your IAM vendor.
Where we always do better than our competition is our IAM implementation plan. We believe in putting the full solution and plan and cost and SOW up front to help make the decision easier for our clients. Other vendors don't always do that; if you found this blog post by searching for IAM implementation plan then you might already realize that. Here are the items to consider when looking for an implementation plan from your IAM vendor.
 Remember your first day on the job at your company, you were given access to a few things, keys to the kingdom if you will. A year later you were promoted, given new responsibilities and a few more of these "keys". By the time you've been at a company for a few years, your "keychain" looks like one of those giant keyrings that a NY super has.
Remember your first day on the job at your company, you were given access to a few things, keys to the kingdom if you will. A year later you were promoted, given new responsibilities and a few more of these "keys". By the time you've been at a company for a few years, your "keychain" looks like one of those giant keyrings that a NY super has.
 So, that's how we define who has access. But more often than not, there is an approval layer in the workflow. We know that an admin role can create a new user but might need an HR approval before it happens. A user can update their own phone number but their manager needs to approve it. A user can join a distribution list but the group owners need to approve it. It's a simple business control but can get complex.
So, that's how we define who has access. But more often than not, there is an approval layer in the workflow. We know that an admin role can create a new user but might need an HR approval before it happens. A user can update their own phone number but their manager needs to approve it. A user can join a distribution list but the group owners need to approve it. It's a simple business control but can get complex.
 This problem is exacerbated due to SAP HCM's e-recruitment capabilities and the need to create accounts and identities for job applicants. They can't be expected to wait for such a long time to have access to systems that they need for their job application.
This problem is exacerbated due to SAP HCM's e-recruitment capabilities and the need to create accounts and identities for job applicants. They can't be expected to wait for such a long time to have access to systems that they need for their job application.