How about a trick question? What is your most authoritative source for identity information? It's not that tricky....your HRIS. But your actual users are an awfully close second. They know themselves and if you give them a self service portal, they can make your life easier.
 The real trick is what you allow them to update via self service. Most shops allow some limited Active Directory self service. But there is so much more that you can open up with a well designed self service identity management system...as long as you put controls, approvals and lifecycle into effect.
The real trick is what you allow them to update via self service. Most shops allow some limited Active Directory self service. But there is so much more that you can open up with a well designed self service identity management system...as long as you put controls, approvals and lifecycle into effect.
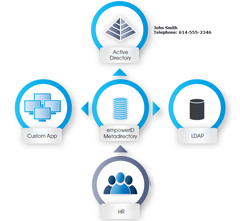
EmpowerID's HTML5 interface gives users a clean view into any application or identity store via a single interface from any device. Attributes, group and role memberships, and permissions for any identity store / application can be managed via the metadirectory with updates either pushed directly to the application or synchronized on a scheduled basis.
Any field can be hidden, read-only, or editable based on the user's role(s). Approval workflows are managed via EmpowerID's unique RBAR architecture (Rights Based Approval Routing), allowing you to easily manage who can and cannot make and approve changes. Lifecycle can be applied to any object or membership, allowing you to have full identity lifecycle and temporary privileged access.
But the most important factor is what your users have access to self-serve. Where most solutions stop at Active Directory, EmpowerID just starts there. If a user needs to change their home phone number, that information needs to filter to AD for the GAL, HR for contact information, the emergency notification system, and to benefits databases. Important information like this should not be left to scripts written by some contractor who won't work there in 3 months.
There are other glaring examples around group memberships which affect other systems. Dynamic group memberships that are driven off of identity information. Office locations that determine parking privileges. Mobile phone numbers for second factor authentication and device registration.
Think of all of the things your users know about themselves that you cannot find out. That is your list of attributes and systems that you allow self service for. Think of everyplace that those attributes need to be synchronized. That is your list of applications, databases and directories that you need to connect to. Think of everyone who can actually approve those changes, that is your RBAR structure.
Allowing self service for identity management does not replace the connectors, synchronization and metadirectory. It complements it and makes a more thorough identity management solution.

 Active Directory is a bear to manage through ADUC. It is clumsy and all-encompassing and the ability to manage granulary is exceptionally complex. Delegating and instituting fine grained permissions requires deep and arcane knowledge of Active Directory. In short, Active Directory management is difficult with ADUC and it doesn't have to be that way.
Active Directory is a bear to manage through ADUC. It is clumsy and all-encompassing and the ability to manage granulary is exceptionally complex. Delegating and instituting fine grained permissions requires deep and arcane knowledge of Active Directory. In short, Active Directory management is difficult with ADUC and it doesn't have to be that way.
 The project list of things to automate is a mile long, starting with user provisioning and permissions, group and role memberships, identity synchronization, and so on. For delegation, the list is equally as long -- password reset, group membership, single sign-on, cloud accounts, and the lowest hanging fruit: Active Directory self-service.
The project list of things to automate is a mile long, starting with user provisioning and permissions, group and role memberships, identity synchronization, and so on. For delegation, the list is equally as long -- password reset, group membership, single sign-on, cloud accounts, and the lowest hanging fruit: Active Directory self-service. Let's take the first use case, users that are not in AD but that need an O365 account. This happens often in franchises, education, manufacturing or when offering accounts to non-employees. EmpowerID's metadirectory stores a "person" object that is completely independent of AD, this user account can then be provisioned to O365 and updated through EmpowerID's HTML5 user interface.
Let's take the first use case, users that are not in AD but that need an O365 account. This happens often in franchises, education, manufacturing or when offering accounts to non-employees. EmpowerID's metadirectory stores a "person" object that is completely independent of AD, this user account can then be provisioned to O365 and updated through EmpowerID's HTML5 user interface.

 But this information belongs in more places than Active Directory. If your user updates her home address, that information should flow to your payroll application. If mobile phone is updated, that should flow to your emergency contact list. Identity is a lot more far reaching than Active Directory, but AD is the place that your users understand; it's the global address list, they see it all the time.
But this information belongs in more places than Active Directory. If your user updates her home address, that information should flow to your payroll application. If mobile phone is updated, that should flow to your emergency contact list. Identity is a lot more far reaching than Active Directory, but AD is the place that your users understand; it's the global address list, they see it all the time.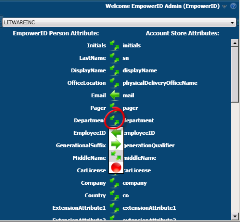 Having a
Having a  As George Orwell said, "All animals are equal but some animals are more equal than others." How does this apply to resetting passwords? Everyone needs passwords reset, but some need a little extra security around their password resetting.
As George Orwell said, "All animals are equal but some animals are more equal than others." How does this apply to resetting passwords? Everyone needs passwords reset, but some need a little extra security around their password resetting.
 Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
 Active Directory groups are essential for fileshare permissions, for email communications, a few GPOs, and just plain useful for some application permissions. You can use them for SharePoint, though I recommend
Active Directory groups are essential for fileshare permissions, for email communications, a few GPOs, and just plain useful for some application permissions. You can use them for SharePoint, though I recommend 
 Providing Active Directory self service gives you a good place to store this data. Most of these items have attributes in AD and you can easily synchronize that information from AD to your HRIS or emergency notification system. You can even then start making dynamic Active Directory groups based on the information.
Providing Active Directory self service gives you a good place to store this data. Most of these items have attributes in AD and you can easily synchronize that information from AD to your HRIS or emergency notification system. You can even then start making dynamic Active Directory groups based on the information.

