We get involved in some very cool intricate discussions on identity management; delving into federation, RBAC, provisioning workflows, all the really fun stuff. But sometimes you have to step back and realize that there is some blocking and tackling needed. You need Active Directory self service.
End users are an incredible source for identity information and permissions management. What you can't automate, delegate. And this is very true.
 The problem is that Active Directory houses some very sensitive information and many extremely important business processes are keyed off of it. As such, you can't let an end user change their title or direct reports or gain access to the shared folder that houses the 10Q documents. So, when delegating, keep RBAR in mind.
The problem is that Active Directory houses some very sensitive information and many extremely important business processes are keyed off of it. As such, you can't let an end user change their title or direct reports or gain access to the shared folder that houses the 10Q documents. So, when delegating, keep RBAR in mind.
What's RBAR you say? Rights based approval routing. The idea that you take your roles and assign what can and cannot be changed in AD based on who is asking. If it's the title attribute and the requester is the VP of HR, you let the change happen. If it's the mobile phone number and it's the user requesting it, make the change. If it's the telephone number and the user's manager asking, route that approval over to IT for an official OK.
It's really that easy. It takes IT out of the process unless it's something that they need to know and/or approve. It gives control to the business owner who should know what needs to happen. And it maintains the integrity of Active Directory.
This RBAR concept also applies to Active Directory group management. Different groups have different levels of security. Anybody should be able to join the "book of the month club" group; but an approval should be needed to join the "Top Secret book binding project" group. CEO approval should be needed to join the "10Q analyst call" group and HR approval should be needed to leave the "Employees on probation" group. RBAR it.
What happens when you flip the tables and offer file share access via self service? Nothing different, apply the RBAR concept to requesting access to a resource. Don't just rely on the outdated AGDLP method to manage access, utilize roles and RBAR.
I could go on and on but our whitepaper already did that, discussing how to delegate permissions into AD without giving permission to AD. Take a look.

 When you start work in the morning, you authenticate against Active Directory; when you start thinking about identity and access management, you start thinking about Active Directory. Active Directory is at the heart of it all but is often oddly neglected.
When you start work in the morning, you authenticate against Active Directory; when you start thinking about identity and access management, you start thinking about Active Directory. Active Directory is at the heart of it all but is often oddly neglected.
 I had a customer years ago who couldn't keep Active Directory identity information accurate, so they gave everyone access to ADUC. You know, so that the users could update their own address, etc. This company went bankrupt; that's what happened when you give fully privileged ADUC access to more than the handful that should have it, you go bankrupt.
I had a customer years ago who couldn't keep Active Directory identity information accurate, so they gave everyone access to ADUC. You know, so that the users could update their own address, etc. This company went bankrupt; that's what happened when you give fully privileged ADUC access to more than the handful that should have it, you go bankrupt. The trouble is that your users' identities stretch far and wide nowadays. There are tons of internal systems that they need access to, scads of databases holding pertinent pieces of their identities, even multiple AD accounts belonging to the same person. You have data governance being handled by AD security groups without an easy way of knowing who has what access. You have cloud applications that need to know who your user is and what they can do.
The trouble is that your users' identities stretch far and wide nowadays. There are tons of internal systems that they need access to, scads of databases holding pertinent pieces of their identities, even multiple AD accounts belonging to the same person. You have data governance being handled by AD security groups without an easy way of knowing who has what access. You have cloud applications that need to know who your user is and what they can do.
 Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.
Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.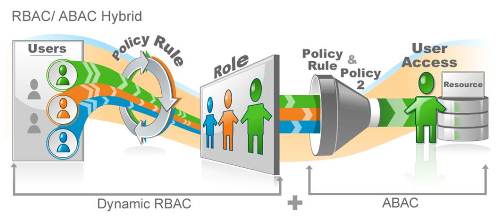

 Dynamic security groups in Active Directory
Dynamic security groups in Active Directory

