 What makes EmpowerID different? In the crowded Identity and Access Management (IAM, also referred to as IDM) market, our slogan, “A new breed of identity management“ and a little of our history are helpful in understanding the answer to this question.
What makes EmpowerID different? In the crowded Identity and Access Management (IAM, also referred to as IDM) market, our slogan, “A new breed of identity management“ and a little of our history are helpful in understanding the answer to this question.
By 2005, we had spent three years developing and deploying an easy to use and quick to deploy Self-Service Password Management and User Provisioning product. We realized that clients were consistently asking for many of the same features that couldn’t be found in one offering:
- The lower cost and ease of use of an application, but also the power and flexibility of a platform
- The ability to make Identity Management processes conform to their business practices, instead of making changes to accommodate the limitations of an IAM application
- A modular approach that allows them to buy just what they need now, with the ability to add support for additional directories, platforms, applications and federated single sign-on (SSO) later
- Freedom from vendor bias, meaning that they don’t want to sacrifice strong support of Microsoft platforms to get strong support for an Oracle, SAP or IBM platform, or any number of other standard and custom applications
- A high degree of integration among the moving parts of an Identity and Access Management (IAM) platform and a “single pane of glass” to see security across all connected applications, platforms and directories
- Powerful Role-Based Access Control (RBAC) that allows them to quickly configure access, views and control by a wide range of hierarchies and locations, but which still can have rights added or subtracted manually
- A standalone Metadirectory that allows them to store information and extended attributes without stuffing them into an internal system like Active Directory
- Highly flexible, modern user interfaces with “rights-trimmed” user views and support for corporate theming
The first thing that struck us when we reviewed this list of client requests was that we had to develop a fresh, innovative vision if we were to achieve all of these objectives in one solution. We concluded that we had to think in terms of a platform, by which we mean a common set of code, logic, services, tools, and interfaces that could span every module that we would want to develop in the foreseeable future. This platform would also have to offer redundancy, high availability and scalability to meet both the demands of the largest enterprises and the rapidly growing number of organizations that need to securely manage Identity information for their partners and customers.
Cobbling together different applications through licensing agreements or acquisitions would not accomplish a key goal for us that has eluded all other major vendors in the IAM market: producing a full-featured platform that could meet all of a client’s major goals while costing significantly less to develop and to expand, as well as costing our customers less to acquire and to maintain. Key to this would be to build the entire platform on a single codebase that would allow for the accelerated development of new modules and features.
We realized we had only one option to include all of the items on our clients’ wish list: to start from scratch. By taking a “greenfield” approach we sought to avoid the architectural and design constraints that limit our competitors and to allow us to offer a breakthrough price point for enterprises that had been excluded from acquiring traditional IAM platforms by their high initial cost and their labor intensive implementation and support requirements.
Our first task was to decide which key elements would be essential to include in this new platform approach to Identity and Access Management, and these are the core components of EmpowerID that when combined make it truly different:
- Workflow – not just a series of simple approvals that other vendors offer, but rather a comprehensive Business Process Automation (BPA) platform that provides the mechanism for executing every action taken by the IAM platform against other connected directories, applications and platforms. We ship with over 375 workflows in our complete suite that can be installed and can start performing work in a day. Our visual workflow designer can modify any workflow and create new ones and allows business managers to collaborate with developers by allowing them to see how IAM information flows and is controlled throughout their enterprise. It collapses the time for producing client-specific customizations and it creates productivity gains through automation.
- Metadirectory – a robust directory that stands apart from all other connected directories so that it can function as a full authoritative source of the “truth” about any identity and its attributes as provided by direct input to it, or by inventorying or directly querying in real-time any connected source. This Metadirectory can be used to create and manage the lifecycle of an identity independently of any other directory. It can exist outside of a corporate firewall to safely manage the increasingly complex world of Federated and Cloud Identity. The Metadirectory also functions as a directory, enabling organizations to allow external partners and customers to authenticate without creating user accounts in the corporate Active Directory.
- Role-Based Access Control (RBAC) – some applications claim to offer this, but a major platform must extend a robust vision of managing roles. EmpowerID’s RBAC can determine rights from multiple hierarchies and locations. It works in conjunction with Attribute Based Access Control (ABAC) and another unique contribution we have made to this technology, Rights Based Approval Routing (RBAR), to create remarkably powerful and efficient security with sophisticated approvals, Separation of Duties (SoD) and Attestation capabilities.
- Flexible and modern User Interfaces (UI) – this would seem to be an obvious component, yet it is frequently overlooked by many vendors, despite being the face of the application that all users encounter. We were determined to lead the industry with highly configurable UI that not only allows the security to control each user’s view, but that also enables client branding to create a rich user experience. This is an important component in driving user acceptance and adoption of self-service components.
So how have we done? In the four years since the first release of the EmpowerID platform, we have achieved a global presence in some of the world’s largest organizations and in market segments that include: finance, banks, regulatory agencies, governments, energy producers, healthcare, retail, manufacturers, advertising agencies, manufacturers, primary and secondary education, and software developers, among others. We have single installations with hundreds of thousands of users managing millions of objects and many projects that connect and provide Identity Management for Cloud applications.
The distinguishing characteristics of our wins include:
- We are highly competitive on the pricing of the EmpowerID suite while offering lower implementation costs and shortened project timeframes due to our requiring less of the custom development and heavy scripting that characterizes our competitors
- We have replaced many IAM applications or we coexist and interoperate in environments with existing IAM investments because of our ability to incorporate existing code with our open workflow platform and our flexible connector and communications models
- Clients make extensive use of our workflow, using it to automate and to design and automate many non-IAM functions because of the extraordinary capabilities of the platform that allow it to drive efficiencies with secure Business Process Automation. Some clients have gone as far as to build complete applications on their own using our workflow designer.
- We retain responsibility for a successful completed project – we don’t push our clients to buy EmpowerID independent of delivering a successfully completed project like much of our competition that relies on partners of varying quality to deliver a finished result
We continue to aggressively develop EmpowerID, with the release in March of the 2012 version of EmpowerID in conjunction with two new modules: SSO Manager, which integrates Federated Single Sign-On (SSO) into the platform and File Share Manager, which provides shared folder permissions inventory and management.
EmpowerID allows enterprises to securely manage their identities while generating cost-savings from automating and securely delegating tasks. Our goal is to continue to make Identity and Access Management easier to implement and easier to maintain, permitting an increasingly broader range of enterprises to own the critical IAM technology they need to realize their automation, compliance and Cloud goals.
Discover the new breed in IAM software by exploring EmpowerID.
 Role based authentication is not RBAC. RBAC determines what resource or application you can access based on your role while role based authentication determines how you will need to authenticate to access that resource or application. In the way EmpowerID performs this function, it is more akin to adaptive authentication.
Role based authentication is not RBAC. RBAC determines what resource or application you can access based on your role while role based authentication determines how you will need to authenticate to access that resource or application. In the way EmpowerID performs this function, it is more akin to adaptive authentication.
 Now you've done it, you have decided to look into an Identity & Access Management (IAM) solution. There aren't a lot of these IAM solutions out there so it's pretty easy to narrow down the list of
Now you've done it, you have decided to look into an Identity & Access Management (IAM) solution. There aren't a lot of these IAM solutions out there so it's pretty easy to narrow down the list of 
 As
As 
 What makes EmpowerID different? In the crowded Identity and Access Management (IAM, also referred to as IDM) market, our slogan, “A new breed of identity management“ and a little of our history are helpful in understanding the answer to this question.
What makes EmpowerID different? In the crowded Identity and Access Management (IAM, also referred to as IDM) market, our slogan, “A new breed of identity management“ and a little of our history are helpful in understanding the answer to this question. SharePoint's People Picker is one of the strangest user interfaces in the world. A SharePoint site admin generally gives permissions to either SharePoint groups or Active Directory groups. But if he/she uses AD groups, he/she doesn't know who is a member.
SharePoint's People Picker is one of the strangest user interfaces in the world. A SharePoint site admin generally gives permissions to either SharePoint groups or Active Directory groups. But if he/she uses AD groups, he/she doesn't know who is a member.
 Talking to a client the other day about enterprise to cloud access, it became apparent that before considering cloud SSO, cloud provisioning needed to be taken care of. More than that, role based cloud provisioning.
Talking to a client the other day about enterprise to cloud access, it became apparent that before considering cloud SSO, cloud provisioning needed to be taken care of. More than that, role based cloud provisioning.
 Let's think through a use case. Your internal developers have created a web app that is crashing, they don't have access to production but need to run some tests and troubleshoot what has happened. They could work with an IT admin and get it done using their credentials but that doesn't always work.
Let's think through a use case. Your internal developers have created a web app that is crashing, they don't have access to production but need to run some tests and troubleshoot what has happened. They could work with an IT admin and get it done using their credentials but that doesn't always work.
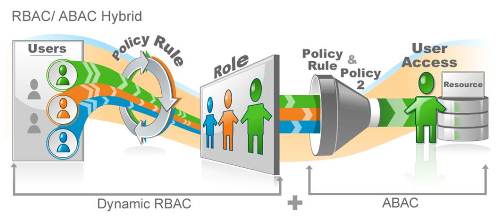

 One of the main issues with access requests by your users is they don't know what to ask for! Think about it, your user knows that they want to see the prior year's sales results sorted by average receivables age. They go to your access resource catalog and sure enough there isn't a resource named that.
One of the main issues with access requests by your users is they don't know what to ask for! Think about it, your user knows that they want to see the prior year's sales results sorted by average receivables age. They go to your access resource catalog and sure enough there isn't a resource named that.
 Providing Active Directory self service gives you a good place to store this data. Most of these items have attributes in AD and you can easily synchronize that information from AD to your HRIS or emergency notification system. You can even then start making dynamic Active Directory groups based on the information.
Providing Active Directory self service gives you a good place to store this data. Most of these items have attributes in AD and you can easily synchronize that information from AD to your HRIS or emergency notification system. You can even then start making dynamic Active Directory groups based on the information.

