You know that guy in accounting you just don't like and wish you didn't have to talk to? Well, there's a chance that you don't have to! Separation of Duties (SOD) to the rescue.
 It doesn't really work like that but there are some mutually exclusive roles. One where if you have these sets of permissions, you cannot have another set of permissions. Some of these are security related (for example, you have permission to create a user, you should not have permission to add them to the financials group, this keeps one person from being able to create a fake user to access critical financial reports). Some are regulatory (for example, in a bank the analysts should not be able to have access to customer records, the bankers should not have access to analyst reports).
It doesn't really work like that but there are some mutually exclusive roles. One where if you have these sets of permissions, you cannot have another set of permissions. Some of these are security related (for example, you have permission to create a user, you should not have permission to add them to the financials group, this keeps one person from being able to create a fake user to access critical financial reports). Some are regulatory (for example, in a bank the analysts should not be able to have access to customer records, the bankers should not have access to analyst reports).
Once you are controlling permissions and access with roles (using Role based access control aka RBAC), it is simple to make roles mutually exclusive. If you are a member of one role, you cannot be a member of another. If you are a member of one role, you need CEO approval to be a member of another. This creates a separation of duties.
I always picture it in action like a Hollywood movie...you need two keys to detonate the bomb and there is a tense standoff as the one guy knows they shouldn't do it. Separation of duties is just like that. Just. Like. That.
Once you've configured your roles to show what your users can do, you need to take that next deeper dive into what that same user shouldn't be able to do. A good mapping of roles and SOD rules will make your organization more secure and your auditors much happier.
If you are one of those "a picture is worth a thousand words" types, give us 15 minutes to show you how SOD works in RBAC by scheduling a demonstration.

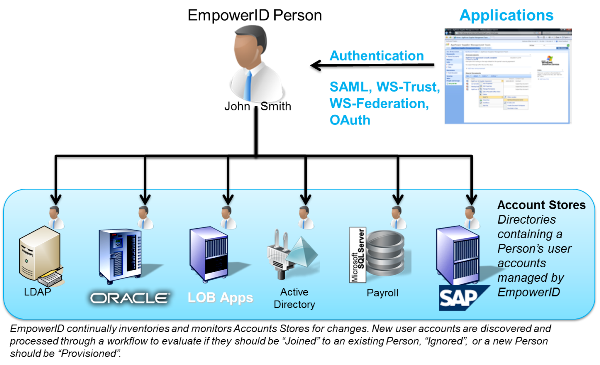

 You have to make it easy for these users to access the correct SharePoint sites based on their role(s). An internal user needs certain access and an external user needs different access; it's like two sides to the same coin. For example, both need to access billing records but have different permissions on what they see.
You have to make it easy for these users to access the correct SharePoint sites based on their role(s). An internal user needs certain access and an external user needs different access; it's like two sides to the same coin. For example, both need to access billing records but have different permissions on what they see.
 But even with the greatest role structure ever created, there is going to be that one folder or that one system or that one cloud application that is just a bit different. You don't want to have to create a new role for this one single use case, you might just want to modify it a bit.
But even with the greatest role structure ever created, there is going to be that one folder or that one system or that one cloud application that is just a bit different. You don't want to have to create a new role for this one single use case, you might just want to modify it a bit.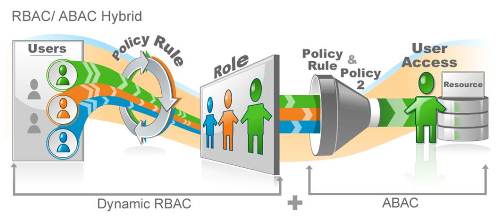

 But there is a whole new realm of identity management you need to think about: partners and customers. Your external identities. You don't hire them so you probably don't have a tried and true process of provisioning. You certainly don't want to give them Active Directory accounts but they need access to a lot of services and systems that you provide.
But there is a whole new realm of identity management you need to think about: partners and customers. Your external identities. You don't hire them so you probably don't have a tried and true process of provisioning. You certainly don't want to give them Active Directory accounts but they need access to a lot of services and systems that you provide. The problem is that Active Directory houses some very sensitive information and many extremely important business processes are keyed off of it. As such, you can't let an end user change their title or direct reports or gain access to the shared folder that houses the 10Q documents. So, when delegating, keep RBAR in mind.
The problem is that Active Directory houses some very sensitive information and many extremely important business processes are keyed off of it. As such, you can't let an end user change their title or direct reports or gain access to the shared folder that houses the 10Q documents. So, when delegating, keep RBAR in mind.
 When you start work in the morning, you authenticate against Active Directory; when you start thinking about identity and access management, you start thinking about Active Directory. Active Directory is at the heart of it all but is often oddly neglected.
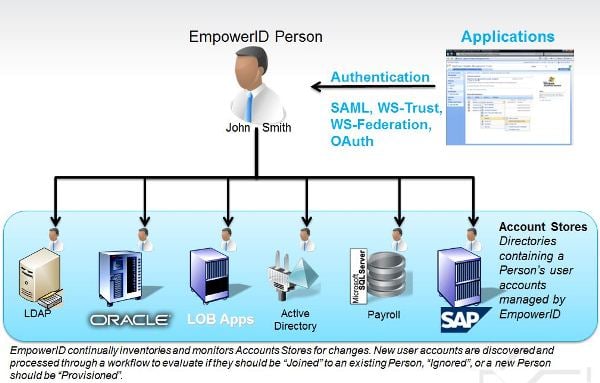
When you start work in the morning, you authenticate against Active Directory; when you start thinking about identity and access management, you start thinking about Active Directory. Active Directory is at the heart of it all but is often oddly neglected.
 The question is, will users ever take this advice and stop using passw0rd as their password? No. And, even if they do, they will continue to write it on a post-it note affixed to the bottom of their keyboard. This is the inevitable and painful flaw in any password policy.
The question is, will users ever take this advice and stop using passw0rd as their password? No. And, even if they do, they will continue to write it on a post-it note affixed to the bottom of their keyboard. This is the inevitable and painful flaw in any password policy.
 Once confirmed as a problem, what about a solution? There are two ways to go about this, Google Apps password reset or Google Apps single sign-on. It depends on your infrastructure I'm sure and I'm probably looking at this from a very EmpowerID-centric view, but neither is a difficult proposition.
Once confirmed as a problem, what about a solution? There are two ways to go about this, Google Apps password reset or Google Apps single sign-on. It depends on your infrastructure I'm sure and I'm probably looking at this from a very EmpowerID-centric view, but neither is a difficult proposition.

