 A common requirement for single sign on (SSO) for partners is that access to systems be role based. This means that when a partner authenticates in to your system, you can give granular access to this user based on their role (or what you know about them).
A common requirement for single sign on (SSO) for partners is that access to systems be role based. This means that when a partner authenticates in to your system, you can give granular access to this user based on their role (or what you know about them).
For this to happen, you have to actually have roles and RBAC incorporated into your identity management system. Specifically, it has to be ingrained into provisioning.
When provisioning a user, you can apply what you know about him/her to create some dynamic roles such as location, partner organization, title, et cetera. As that role is defined, you can bake rules into your provisioning workflow to determine what systems he/she needs access to. For example, a VP in your reseller partner organization will get management access to Salesforce as their account is provisioned. The purchasing agent in your distributor partner gets access to your supply chain system for the products that they are involved in.
This idea of role based provisioning is the pre-cursor to role based access control. You want your provisioning workflows to put users in the correct systems only. Just giving them accounts in an Active Directory OU is not enough, you need it granular and you need it to be accurate.
This is where a visual workflow designer makes a huge difference. It is much easier to design decision trees if you are doing it the way you would design it on a whiteboard, with easily understandable shapes and logic.
Your partners vary more than your employees, they have different needs, offer different benefits to your organization and should have different access. Role based access control and role based provisioning are more important for partners than employees even. You want to control what they can do on your network even more tightly.
Creating granular roles and supplementing it with attributed based access control (ABAC) will enable you to keep your partners effective and secure. Let us take you for a tour of how to design these role based provisioning workflows and put partners in their place!

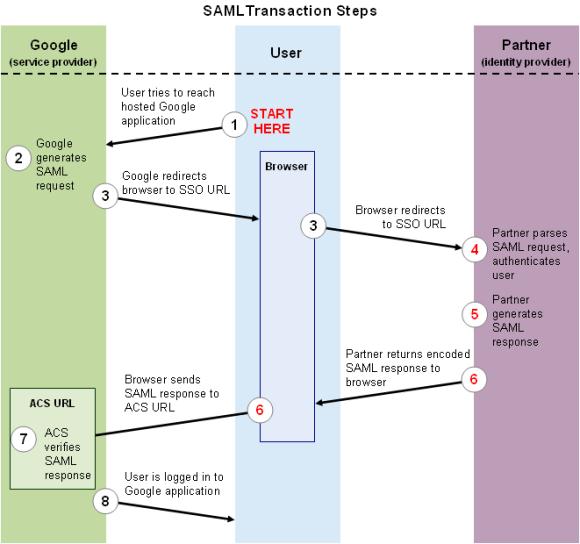.jpg)

 You need to fully integrate
You need to fully integrate 
 While having a discussion with a partner this week, he pointed out that enterprise single sign-on and federation are being confused much less often these days. That led me to asking a few people what the difference is and finding that there is still confusion about the two.
While having a discussion with a partner this week, he pointed out that enterprise single sign-on and federation are being confused much less often these days. That led me to asking a few people what the difference is and finding that there is still confusion about the two.
 It's an age old question, do you want to go with roles or Active Directory group management? The answer is, why do you have to choose? Do both. Roles and groups.
It's an age old question, do you want to go with roles or Active Directory group management? The answer is, why do you have to choose? Do both. Roles and groups.
 For years and years,Microsoft has been recommending AGDLP as the way to manage your file system permissions. User and computer accounts are members of global groups which are members of domain local groups that give resource permissions. This is, to put it mildly, the old and busted way of doing things (OBWDT for short).
For years and years,Microsoft has been recommending AGDLP as the way to manage your file system permissions. User and computer accounts are members of global groups which are members of domain local groups that give resource permissions. This is, to put it mildly, the old and busted way of doing things (OBWDT for short).
 But you cannot manage a user's identity. Because each person is multiple users. They are a user of Salesforce.com, a user of Exchange, a user of quickbooks, et cetera. A user has a department, a title, and a role; but each application they use, gives them a different role, has different identity information about them. Somehow you have to take all of those users and recompile them into a person.
But you cannot manage a user's identity. Because each person is multiple users. They are a user of Salesforce.com, a user of Exchange, a user of quickbooks, et cetera. A user has a department, a title, and a role; but each application they use, gives them a different role, has different identity information about them. Somehow you have to take all of those users and recompile them into a person. 
 I had a customer years ago who couldn't keep Active Directory identity information accurate, so they gave everyone access to ADUC. You know, so that the users could update their own address, etc. This company went bankrupt; that's what happened when you give fully privileged ADUC access to more than the handful that should have it, you go bankrupt.
I had a customer years ago who couldn't keep Active Directory identity information accurate, so they gave everyone access to ADUC. You know, so that the users could update their own address, etc. This company went bankrupt; that's what happened when you give fully privileged ADUC access to more than the handful that should have it, you go bankrupt.
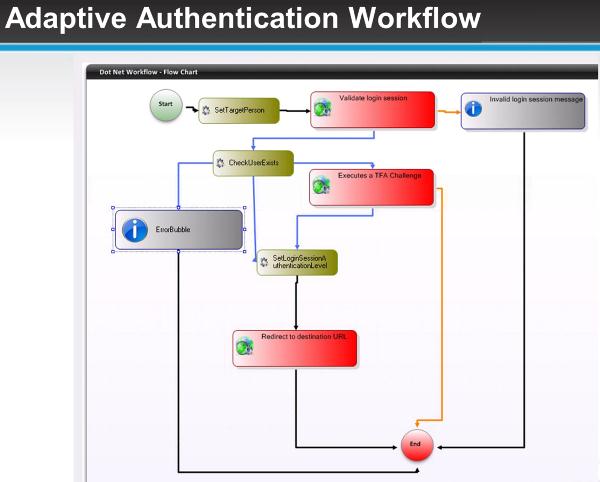


 The trouble is that your users' identities stretch far and wide nowadays. There are tons of internal systems that they need access to, scads of databases holding pertinent pieces of their identities, even multiple AD accounts belonging to the same person. You have data governance being handled by AD security groups without an easy way of knowing who has what access. You have cloud applications that need to know who your user is and what they can do.
The trouble is that your users' identities stretch far and wide nowadays. There are tons of internal systems that they need access to, scads of databases holding pertinent pieces of their identities, even multiple AD accounts belonging to the same person. You have data governance being handled by AD security groups without an easy way of knowing who has what access. You have cloud applications that need to know who your user is and what they can do.

