I often talk about how a person is a person until hired, then they become an employee. Once IT gets ahold of them, they become a user. And this link between being a person and a user gets lost. At its core, this is the goal of identity management, to understand that user as a person/employee.
Think about that person for a second, how many user accounts does each person have? In each system, there is one. And in many cases, each person could have multiple Active Directory accounts. How do you correlate them? How do you lump all of these user accounts into a person? A metadirectory.
With a metadirectory, or the person directory as we call it, you can correlate all of the identities and all of the identity information into one person. The key is to have a key, or keys if necessary. The metadirectory inventories all of these systems with all of these user accounts and logs changes, creating an up-to-date person.
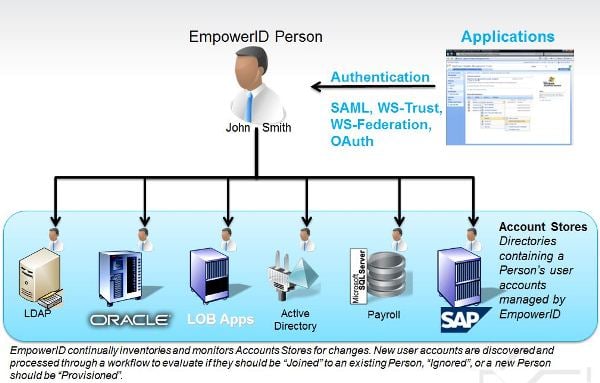
And, of course, this is where it gets fun. Once you have this person with all of his identity information in the metadirectory, you can now authenticate against this directory, creating a federated single sign on to any of your connected applications, even in the cloud! The roles that you create can apply to each application, creating a true RBAC environment. Provisioning and de-provisioning are built into each application automatically; people are productive immediately.
Now, do you want to have to code each and every attribute synchronization? No. You need a WYSIWYG synchronization engine that defines workflows of what goes where. Which system is authoritative? The best and simplest example is HR and AD...HR is authoritative for everything but email address...so you send identity information to Active Directory from your HRIS, provision an Exchange account, and shoot that email address back to HR.
Make your users people again, give them the correct access, unify and correlate their identity to make them whole again.


