A customer was showing us his current state of role based access control for their business intelligence application. What had happened was that for each segment of BI reporting, he had to create a role. The real issue was that each of those roles was needed for each region. So suddenly he had 10 management roles TIMES 4 regions for a grand total of 40 roles that he needed. Just for his BI app.
He needed an easier way to manage this. Their solution had been to allow an EMEA user to request North American access and then the approver had to deny it. It was confusing for both the access requester and the approver.
What helps this is our combination RBAC and ABAC (attribute based access control) hybrid model. 10 business roles are defined and then access requests are security trimmed based on the requester's region (an attribute in the directory). Attribute based access control allows you to take an actual role and get fine grained for the access request system without the requester even knowing it is happening.
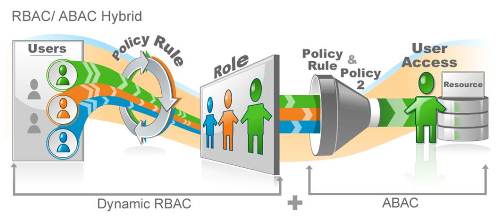
We could even fine tune it further by using rights based approval routing (RBAR). Let's say they want to define it that anyone in a certain department gets auto-approved, RBAR does that while still requring approval for someone outside of that department even though they are both in the same role!
Remember that the whole goal of Identity Management is to get the right user the right access to the right resources. What is left unsaid there is "with as little IT interaction as necessary". You can add some components like ABAC and RBAR on top of RBAC to map these workflows to your business process.
In the end, the customer won't need to create an exorbitant amount of roles, they reduce the back and forth approval process, and make it easier for the end users. Then for the auditing and intelligence portion of IDM, you'll have a full report and view into whether a person approved the access or a business policy did. You will be conforming to least privilige principles by security trimming what a user can even request.
Take a look at this whitepaper if you want more information. If you are ready to start controlling your access with EmpowerID, we'll show you a demo and prepare a trial for you!
Tags: Role Based Access Control (RBAC), Identity and Access Management (IAM)


