The bane of every SharePoint project is permissions and rights. Access is controlled via SharePoint groups, these quirky little groups that exist in the SharePoint vacuum and only in the SharePoint vacuum. SharePoint 2010 introduced the ability to control access via Active Directory groups but gives no way to manage the membership of these groups. So you end up with site admins managing permissions manually or just letting it die on the vine.
The bane of every SharePoint project is permissions and rights. Access is controlled via SharePoint groups, these quirky little groups that exist in the SharePoint vacuum and only in the SharePoint vacuum. SharePoint 2010 introduced the ability to control access via Active Directory groups but gives no way to manage the membership of these groups. So you end up with site admins managing permissions manually or just letting it die on the vine.
What if you could do true role based access control (RBAC) within SharePoint? Have dynamic roles for your users that change as the user changes (new department, title, location, etc)? And then manage site permissions with these roles? Thanks to SharePoint 2010's claims provider functionality you can.
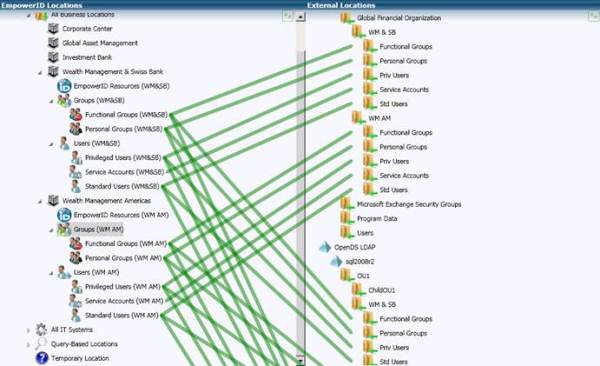
If you set EmpowerID as the claims provider for SharePoint, it exposes EmpowerID roles in the "People Picker", allowing the site administrator to pick a role (for example, HR managers in the investment banking division) to have access to that site. These are the same roles that will be used for resource permissions or application access. And it is possible to see who is a member (if you have permission to view membership of that role) from within SharePoint, making it possible to ensure that the right people have access to the right SharePoint resources.
The thing about roles is that they don't have some of the side effects that Active Directory groups do such as token bloat. You can be a member of as many EmpowerID roles as you want without impacting your ability to log into the network. On top of that, EmpowerID offers a polyarchical role structure so you can pick that HR manager role in investment banking from two trees, limiting the number of roles that you need to create.
Having a true SharePoint RBAC system also allows you to manage separation of duties since you can set an SOD rule that says a user cannot simultaneously be in two conflcting roles. You don't have to worry about accidentally giving an investment banker access to the retail banking SharePoint site.
SharePoint RBAC is just a lot more flexible than managing permissions with groups (either AD or SP). You get all the benefits of maintaining permissions dynamically without the overhead of managing a completely different set of access infrastructure. This same claims provider functionality gives you SharePoint single sign on capabilities for your external partners for example without having to have AD accounts for them.


 I'm being facetious of course, there's nobody in IT named Bob usually. But that's where your identity and access management platform comes in. It is busy giving people access to systems and you need to make sure that you are inserting the "right" into that sentence & process.
I'm being facetious of course, there's nobody in IT named Bob usually. But that's where your identity and access management platform comes in. It is busy giving people access to systems and you need to make sure that you are inserting the "right" into that sentence & process.
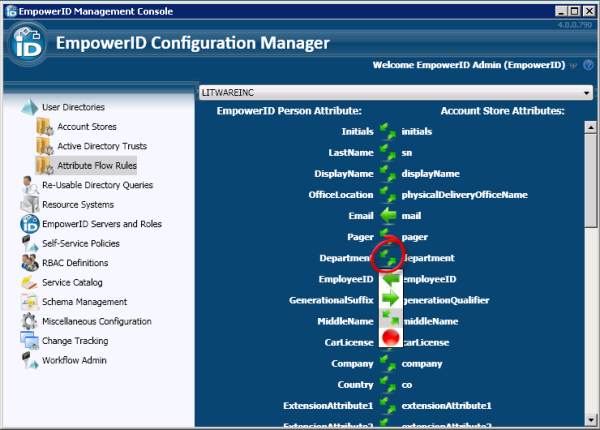
 The most obvious and important identity store to consider is Active Directory. There is a lot of identity information within there to delegate: mobile phone, home address, and other personal information. This is the sort of identity information your company needs and can only be provided by the users themselves. In fact, once they enter it via your self service interface, take advantage of this and flow the information back to the HR system.
The most obvious and important identity store to consider is Active Directory. There is a lot of identity information within there to delegate: mobile phone, home address, and other personal information. This is the sort of identity information your company needs and can only be provided by the users themselves. In fact, once they enter it via your self service interface, take advantage of this and flow the information back to the HR system.
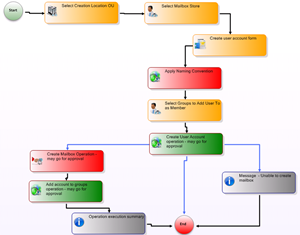 This provisioning workflow is designed around your business rules and processes. EmpowerID offers a visual workflow designer that has almost 400 out of the box templates and the power to customize each worfklow with 400 different actions or shapes.
This provisioning workflow is designed around your business rules and processes. EmpowerID offers a visual workflow designer that has almost 400 out of the box templates and the power to customize each worfklow with 400 different actions or shapes.
 I have seen extremes from one out of business retailer who let every user have access to Active Directory Users & Computers (ADUC) to minimize help desk calls to a very successful international bank who has pretty much shut down ADUC in favor of a granular rights based self service delegation through empowerID.
I have seen extremes from one out of business retailer who let every user have access to Active Directory Users & Computers (ADUC) to minimize help desk calls to a very successful international bank who has pretty much shut down ADUC in favor of a granular rights based self service delegation through empowerID.

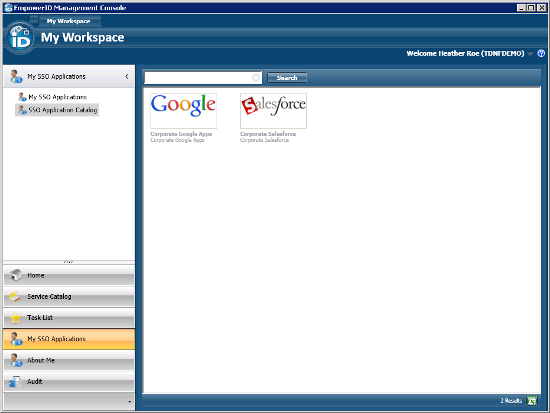
 Now if you want to automate the user account provisioning process, you need to account for any cloud applications the user has. These cloud applications have different UIs, are owned by different lines of business and generally add a wrinkle to your identity and access management that you just don't need.
Now if you want to automate the user account provisioning process, you need to account for any cloud applications the user has. These cloud applications have different UIs, are owned by different lines of business and generally add a wrinkle to your identity and access management that you just don't need.
 At a back to school party this weekend, one of the parents asked what I did. After I explained identity and access management, this parent sounded a familiar refrain, "why do I need so many passwords?" After the perfunctory and admittedly glib, "because you don't use EmpowerID", I gave the real answer: because not everyone knows how simple it is.
At a back to school party this weekend, one of the parents asked what I did. After I explained identity and access management, this parent sounded a familiar refrain, "why do I need so many passwords?" After the perfunctory and admittedly glib, "because you don't use EmpowerID", I gave the real answer: because not everyone knows how simple it is.