I am a big fan of role based access control (RBAC). My entire product line is built on the concept. Roles control what systems a user gets provisioned in, what level of access they have in those systems, what files and folders they can use, and basically how they do their job. Having multi-hierarchical roles means that you don't even have to define every single role, they define themselves.
 But even with the greatest role structure ever created, there is going to be that one folder or that one system or that one cloud application that is just a bit different. You don't want to have to create a new role for this one single use case, you might just want to modify it a bit.
But even with the greatest role structure ever created, there is going to be that one folder or that one system or that one cloud application that is just a bit different. You don't want to have to create a new role for this one single use case, you might just want to modify it a bit.
Enter Attribute based access control (ABAC)! Attribute based access control is the concept of having your permissions defined by an attribute in Active Directory or other system to determine if the user has access. Combining its power with RBAC gives you the best of both worlds.
Say you have an HR Manager in the Southwest region and your RBAC rules gives him/her and all of his/her peers access to applicant resumes either in a folder or your HR system. But, your company is in the process of hiring a new CFO. Somebody has to review those resumes but it is highly sensitive and only one manager is tasked with it; the rest should not be able to see them. You don't want to create a new role just for this one task but you know that certain managers are identified in AD as "top secret clearance".
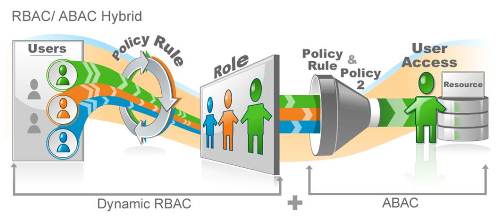
When creating this new access, just use the HR Manager Southwest role, then add the attribute of "top secret clearance", and anyone in that role with that clearance is given permission to manage these resumes. As users' roles and clearances change, that access will always be dynamically assigned to the correct users.
I have often heard, "how is this different from dynamic groups?" Dynamic AD groups mostly are used for file systems; we offer these as well, but to have dynamic role or hybrid role based and attribute based access allows you to extend these permissions past the file system and out to provisioning, application access, even to the cloud applications.
If I didn't describe it well enough or if that cool picture didn't really cover it, let us show you how it works with a personalized demo. With an RBAC / ABAC hybrid structure, your users will have the exact access they need when they need it. Also, download the whitepaper!


