SharePoint's People Picker is one of the strangest user interfaces in the world. A SharePoint site admin generally gives permissions to either SharePoint groups or Active Directory groups. But if he/she uses AD groups, he/she doesn't know who is a member.
SharePoint's People Picker is one of the strangest user interfaces in the world. A SharePoint site admin generally gives permissions to either SharePoint groups or Active Directory groups. But if he/she uses AD groups, he/she doesn't know who is a member.
You can solve this conondrum with dynamic Active Directory groups but that still falls short. Active Directory groups have all sorts of issues with forests and domains and what if the user doesn't exist in AD? Many SharePoint instances are a combination of access for employees, contractors, partners and customers. It would be nice to manage the SharePoint permissions for each of those in one central place.
Luckily, SharePoint 2010 supports an external directory as a claims provider. EmpowerID's metadirectory functions as the claims provider and offers federated single sign on to SharePoint. And this opens up the world of roles (static or dynamic roles) to SharePoint. SharePoint permissions management becomes more robust as you can have roles in EmpowerID that reference any identity store, not just AD.
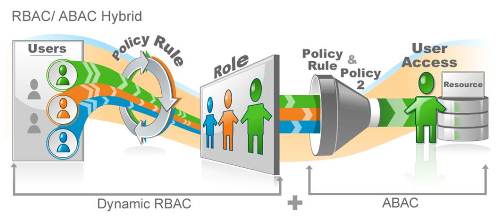
EmpowerID’s powerful hybrid RBAC and ABAC model can be used directly inside SharePoint’s People Picker user interface to grant access to sites, lists, documents, etc. The People Picker allows end-users to search and select any EmpowerID security object such as People, Groups, Roles and dynamic collections just as they would normally search for users or groups.
The EmpowerID RBAC system allows content owners and security administrators to use flexible and dynamically maintained role-based assignments when managing SharePoint permissions. The dynamic nature of these roles can dramatically reduce the administrative burden of manually setting security assignments and automates access granting and revocation based on changes in user’s job status, function or location.
Role based access control (especially when mixed and matched with attribute based access control) gives SharePoint a ton of flexibility in how you assign permissions within SharePoint. That customer can get the exact access they need (and even SSO) without lifting a finger. Your SharePoint team can publish internally and know that role based permissions are keeping it safe.
This is all built-in functionality to EmpowerID, let us know if you'd like to see it in action!

 Let's think through a use case. Your internal developers have created a web app that is crashing, they don't have access to production but need to run some tests and troubleshoot what has happened. They could work with an IT admin and get it done using their credentials but that doesn't always work.
Let's think through a use case. Your internal developers have created a web app that is crashing, they don't have access to production but need to run some tests and troubleshoot what has happened. They could work with an IT admin and get it done using their credentials but that doesn't always work.

 One of the main issues with access requests by your users is they don't know what to ask for! Think about it, your user knows that they want to see the prior year's sales results sorted by average receivables age. They go to your access resource catalog and sure enough there isn't a resource named that.
One of the main issues with access requests by your users is they don't know what to ask for! Think about it, your user knows that they want to see the prior year's sales results sorted by average receivables age. They go to your access resource catalog and sure enough there isn't a resource named that.
 Providing Active Directory self service gives you a good place to store this data. Most of these items have attributes in AD and you can easily synchronize that information from AD to your HRIS or emergency notification system. You can even then start making dynamic Active Directory groups based on the information.
Providing Active Directory self service gives you a good place to store this data. Most of these items have attributes in AD and you can easily synchronize that information from AD to your HRIS or emergency notification system. You can even then start making dynamic Active Directory groups based on the information.
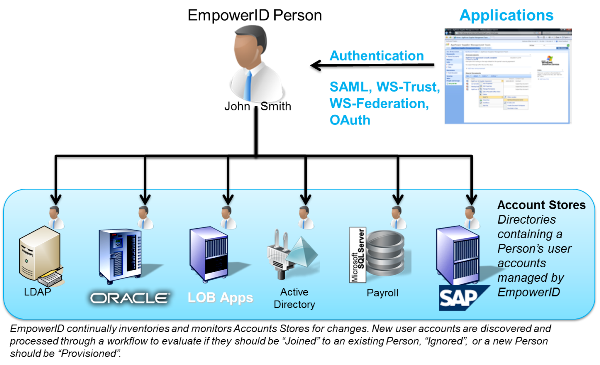
 You have to make it easy for these users to access the correct SharePoint sites based on their role(s). An internal user needs certain access and an external user needs different access; it's like two sides to the same coin. For example, both need to access billing records but have different permissions on what they see.
You have to make it easy for these users to access the correct SharePoint sites based on their role(s). An internal user needs certain access and an external user needs different access; it's like two sides to the same coin. For example, both need to access billing records but have different permissions on what they see.
 But there is a whole new realm of identity management you need to think about: partners and customers. Your external identities. You don't hire them so you probably don't have a tried and true process of provisioning. You certainly don't want to give them Active Directory accounts but they need access to a lot of services and systems that you provide.
But there is a whole new realm of identity management you need to think about: partners and customers. Your external identities. You don't hire them so you probably don't have a tried and true process of provisioning. You certainly don't want to give them Active Directory accounts but they need access to a lot of services and systems that you provide. The problem is that Active Directory houses some very sensitive information and many extremely important business processes are keyed off of it. As such, you can't let an end user change their title or direct reports or gain access to the shared folder that houses the 10Q documents. So, when delegating, keep RBAR in mind.
The problem is that Active Directory houses some very sensitive information and many extremely important business processes are keyed off of it. As such, you can't let an end user change their title or direct reports or gain access to the shared folder that houses the 10Q documents. So, when delegating, keep RBAR in mind.
 When you start work in the morning, you authenticate against Active Directory; when you start thinking about identity and access management, you start thinking about Active Directory. Active Directory is at the heart of it all but is often oddly neglected.
When you start work in the morning, you authenticate against Active Directory; when you start thinking about identity and access management, you start thinking about Active Directory. Active Directory is at the heart of it all but is often oddly neglected.