I often think of Gartner's quote on identity and access management: "the right people have access to the right systems at the right time" and think how do you know if they are the right people or the right systems or the right access? We work with organizations with hundreds of thousands of users, does Bob in IT know all of them?
 I'm being facetious of course, there's nobody in IT named Bob usually. But that's where your identity and access management platform comes in. It is busy giving people access to systems and you need to make sure that you are inserting the "right" into that sentence & process.
I'm being facetious of course, there's nobody in IT named Bob usually. But that's where your identity and access management platform comes in. It is busy giving people access to systems and you need to make sure that you are inserting the "right" into that sentence & process.
Having trusted authoritative sources really helps. If you know that HR and other systems know all of the employees, contractors, partners and customers, you can usually cover the "right person" aspect of all of this. But, that isn't always the case, so you have your first attestation option right there to solve the "right people" issue.
There will be a departmental owner or manager or HR person who can attest periodically that that user is still an active employee. Build a workflow where somebody has to approve the continuing existence of that user account. Not just a network account, but application accounts too. Think of the savings if you periodically have users attest that they still need that cloud application account for which you are paying a monthly fee.
If the account hasn't been used or accessed for a certain period (say, 90 days), bump up the attestation. It's easy to build this into a BPM-based identity workflow. Make more secure application accounts have a higher degree of attestation involving identity proofing or two factor authentication.
So, with that user attestation process you solve the right systems and the right people but what about the right access? Roles and group attestation helps solve this. Have the role or group owner attest to the membership of the group and the group's rights and permissions on a quarterly or yearly basis. Give them the audit reports to show what that role or group can do and who has been doing it.
This should all be built in to the identity workflows that come with your IAM platform, if not, take a look at EmpowerID. Dont' just give access to people, give the right access to the right people.

 The most obvious and important identity store to consider is Active Directory. There is a lot of identity information within there to delegate: mobile phone, home address, and other personal information. This is the sort of identity information your company needs and can only be provided by the users themselves. In fact, once they enter it via your self service interface, take advantage of this and flow the information back to the HR system.
The most obvious and important identity store to consider is Active Directory. There is a lot of identity information within there to delegate: mobile phone, home address, and other personal information. This is the sort of identity information your company needs and can only be provided by the users themselves. In fact, once they enter it via your self service interface, take advantage of this and flow the information back to the HR system.
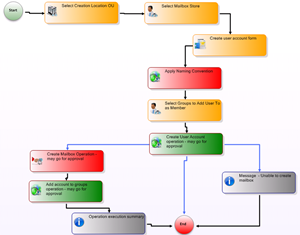 This provisioning workflow is designed around your business rules and processes. EmpowerID offers a visual workflow designer that has almost 400 out of the box templates and the power to customize each worfklow with 400 different actions or shapes.
This provisioning workflow is designed around your business rules and processes. EmpowerID offers a visual workflow designer that has almost 400 out of the box templates and the power to customize each worfklow with 400 different actions or shapes.
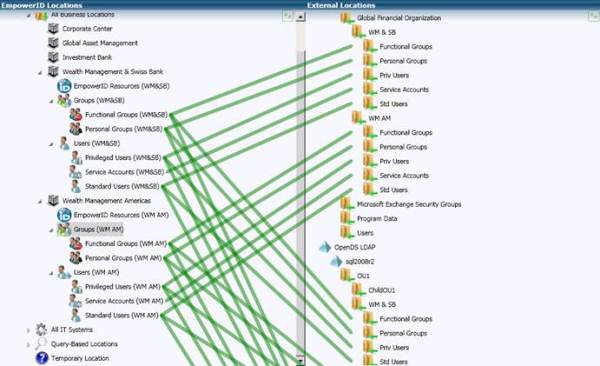
 I have seen extremes from one out of business retailer who let every user have access to Active Directory Users & Computers (ADUC) to minimize help desk calls to a very successful international bank who has pretty much shut down ADUC in favor of a granular rights based self service delegation through empowerID.
I have seen extremes from one out of business retailer who let every user have access to Active Directory Users & Computers (ADUC) to minimize help desk calls to a very successful international bank who has pretty much shut down ADUC in favor of a granular rights based self service delegation through empowerID.

 Now if you want to automate the user account provisioning process, you need to account for any cloud applications the user has. These cloud applications have different UIs, are owned by different lines of business and generally add a wrinkle to your identity and access management that you just don't need.
Now if you want to automate the user account provisioning process, you need to account for any cloud applications the user has. These cloud applications have different UIs, are owned by different lines of business and generally add a wrinkle to your identity and access management that you just don't need.
 At a back to school party this weekend, one of the parents asked what I did. After I explained identity and access management, this parent sounded a familiar refrain, "why do I need so many passwords?" After the perfunctory and admittedly glib, "because you don't use EmpowerID", I gave the real answer: because not everyone knows how simple it is.
At a back to school party this weekend, one of the parents asked what I did. After I explained identity and access management, this parent sounded a familiar refrain, "why do I need so many passwords?" After the perfunctory and admittedly glib, "because you don't use EmpowerID", I gave the real answer: because not everyone knows how simple it is.

 Role based authentication is not RBAC. RBAC determines what resource or application you can access based on your role while role based authentication determines how you will need to authenticate to access that resource or application. In the way EmpowerID performs this function, it is more akin to adaptive authentication.
Role based authentication is not RBAC. RBAC determines what resource or application you can access based on your role while role based authentication determines how you will need to authenticate to access that resource or application. In the way EmpowerID performs this function, it is more akin to adaptive authentication.
 Now you've done it, you have decided to look into an Identity & Access Management (IAM) solution. There aren't a lot of these IAM solutions out there so it's pretty easy to narrow down the list of
Now you've done it, you have decided to look into an Identity & Access Management (IAM) solution. There aren't a lot of these IAM solutions out there so it's pretty easy to narrow down the list of  As
As