As George Orwell said, "All animals are equal but some animals are more equal than others." How does this apply to resetting passwords? Everyone needs passwords reset, but some need a little extra security around their password resetting.
As George Orwell said, "All animals are equal but some animals are more equal than others." How does this apply to resetting passwords? Everyone needs passwords reset, but some need a little extra security around their password resetting.
Let's take the scourge of the help desk, active directory password reset. Everybody has seen the statistics of how expensive it is to have your help desk take these calls, somehow verify that the user is who they say they are and reset the user's AD password. On average, $35 per call.
The obvious solution is self service AD password reset. Give the users an easy link to reset their password when it is either forgotten or they are locked out. They will answer a pre-configured number of knowledge based questions (eye color, favorite pasta noodle, etc); once answered, the software trusts who they are and lets them reset their password.
The issue with this is that some animals are more equal than others. Do you really want the CFO's password to be compromised because someone read his facebook profile and figured out his eye color and the astounding amount of fusilli that he eats?
The way to solve this is role based Active Directory password reset. Based on the user's role in your RBAC system, you will require a higher level of authentication before allowing them to reset their password. Maybe it's just more questions. Or it could be two factor authentication via SMS. Or it could be identity proofing. Or it could require approval by a help desk employee. The point is, based on a user's role, you can make this password reset more secure.
I have always found it distressing that the higher level of security needed for a user's role, the more likely they are to be violating some basic security rules. For example, the CFO has a bit of influence in a company; if he hates changing his password, he can talk people into allowing his account to have a "never change" policy. Same thing for domain admins.
Role based password management should do just the opposite, it should make these more sensitive roles more secure. Two factor authentication is not that intrusive, just a quick SMS message that your user plugs into a form during password reset. Identity proofing is even easier, it again is something the user knows like their monthly mortgage payment. Security doesn't have to be painful.
And by managing security based on role, you don't have to assign this stricter level of authentication if all that role does is punch in and out of the timeclock application. You still save that $35 per call but can also protect your network with more dexterity.
And here's the best part. This isn't limited to Active Directory. If you are managing all of your passwords through EmpowerID, you can reset all of your passwords together or separately. You can reset your salesforce.com password separate from AD. And you can do all of this based on your user's role.
EmpowerID password manager utilizes roles and resets passwords, one of the benefits of having a purpose-built integrated IAM platform. Schedule a demo and see how you can keep your CFO's account more secure.

 Your finance department is watching the cloud. Not because they are tech literate and following IT trends, but because they can cut your budget quickly with cloud applications. And it's up to you to help them before they help themselves.
Your finance department is watching the cloud. Not because they are tech literate and following IT trends, but because they can cut your budget quickly with cloud applications. And it's up to you to help them before they help themselves.


 Until you observe and measure your IAM practices and policies, you don't know if the right people have the right access. And you don't know if the wrong people got the wrong access. That is where auditing actually helps your business, not just satisfying a regulatory requirement.
Until you observe and measure your IAM practices and policies, you don't know if the right people have the right access. And you don't know if the wrong people got the wrong access. That is where auditing actually helps your business, not just satisfying a regulatory requirement.
 Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
Delegate and Automate. The first two words of IT. It is especially true with respect to managing Active Directory. There are a lot of authoritative sources of identity information that Active Directory needs and not one of them is your help desk employees.
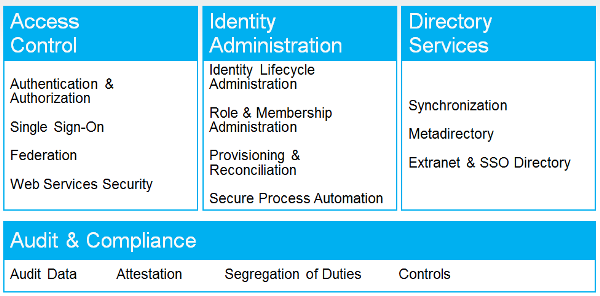
 Not all applications are created equal. Not all users are created equal. Different users need access to different applications; different users need different access to these applications. We call this
Not all applications are created equal. Not all users are created equal. Different users need access to different applications; different users need different access to these applications. We call this  Active Directory groups are essential for fileshare permissions, for email communications, a few GPOs, and just plain useful for some application permissions. You can use them for SharePoint, though I recommend
Active Directory groups are essential for fileshare permissions, for email communications, a few GPOs, and just plain useful for some application permissions. You can use them for SharePoint, though I recommend 

 The bane of every SharePoint project is permissions and rights. Access is controlled via SharePoint groups, these quirky little groups that exist in the SharePoint vacuum and only in the SharePoint vacuum. SharePoint 2010 introduced the ability to control access via Active Directory groups but gives no way to manage the membership of these groups. So you end up with site admins managing permissions manually or just letting it die on the vine.
The bane of every SharePoint project is permissions and rights. Access is controlled via SharePoint groups, these quirky little groups that exist in the SharePoint vacuum and only in the SharePoint vacuum. SharePoint 2010 introduced the ability to control access via Active Directory groups but gives no way to manage the membership of these groups. So you end up with site admins managing permissions manually or just letting it die on the vine.