Security is not easy. IT's goal is to find a way to increase security without adding complexity to the point where it reduces productivity. It is a fine line and one that needs constant balancing.
 Authentication is a key point on this security balance beam. Password complexity, multi factor authentication, adaptive authentication, federation and single sign on are all considerations in how to deliver security without hindering productivity.
Authentication is a key point on this security balance beam. Password complexity, multi factor authentication, adaptive authentication, federation and single sign on are all considerations in how to deliver security without hindering productivity.
Starting on one end of the spectrum (no security but easy for users) is a simple eight character password synchronized to all of your applications....that is not good. On the other end of the spectrum you can have each application having a separate complex 16 character password with biometrics and identity proofing and an OATH token....your users will kill you.
I believe that targeted two factor authentication with single sign on is the answer. Adaptive authentication is what makes this work. Because EmpowerID is built on a visual business process oriented workflow platform, you can insert additional authentication options into any workflow based on either the role of the user authenticating or based on the application that the user is tying to access.
Examples of these two options are:
- Adaptive authentication based on the user's role: All users should be able to authenticate into the network with a password but more highly privileged users (domain admins or VPs of finance) should have a higher level of security. These users will be placed into a role or group that requires a second authentication factor such as an OATH token. (note: I find it very interesting that those with the highest level of access tend to be those who can control their authentication level such as CxOs or domain admins)
- Adaptive authentication based on application: This option will result in much less resistance and one could argue is actually more secure. When a user tries to access a more highly sensitive application or resource, the EmpowerID workflow will recognize the resource as security level X and apply a more stringent authentication method such as knowledge based questions or an OATH token.
The key to all of this is that the IAM platform must have workflows that can increase authentication levels based on either the user's role or the resource's security level. EmpowerID's visual workflow can even make a hybrid model of this where certain roles accessing certain resources can trigger the advanced authentication.
It is also crucial to use the correct second factor. As you know, the first factor is what you know and the second factor is what you have and the third factor is what you are. Remember that balancing act between security and productivity? The productivity side also incorporates how hard it is to get the second factor into your users' hands.
How hard is it to get iris scans or fingerprints for every user? How hard is it to deploy smart cards for remote users when you have a 5% turnover per year? How difficult is it to manage physical assets to manage the "what your users have" factor?
This is what makes smart phones so darned valuable. Everyone has one. The flip side to the BYOD revolution is the first three letters: users bring their own! You can take advantage of this by having users register their devices as part of the authentication (yes, EmpowerID can do that for you). Then either text a code or demand an OATH token as the second factor.
There are plenty of open source apps available (for example, this one for the iPhone) for the OATH client so you don't even have to deploy hardware. EmpowerID has its own OATH server, creating a simple seamless way to incorporate an open standard such as OATH and the widely available smart phone from your users to create a very flexible adaptive authentication method using two factor authentication.
And you get to balance productivity and security by selectively applying this second factor to highly secure and confidential resources and highly privileged users. Additional security without sacrificing productivity. Schedule a demonstration of EmpowerID and see how we can make that a reality for you.

 Identity and access management (IAM) is a big concept. Google analytics tells me that there are 18,100 searches for this term each and every month. Gartner's definition is that "IAM ensures the right people have the right access to the right resources at the right time, enabling the right business outcomes." That is a big concept.
Identity and access management (IAM) is a big concept. Google analytics tells me that there are 18,100 searches for this term each and every month. Gartner's definition is that "IAM ensures the right people have the right access to the right resources at the right time, enabling the right business outcomes." That is a big concept.
 In the real world, the best example is your driver's license. When you present your driver's license to the bank to prove that you are you, the bank (service provider) is trusting that the DMV (identity provider) has properly vetted you with birth certificates, social security cards, or other identity information. Because of this trust, or federation, you don't have to carry all of these documents with you everywhere and prove to every single person that you are you. They trust the DMV (or whatever institution in your country provides driver's licenses) to have taken the appropriate steps to prove your identity.
In the real world, the best example is your driver's license. When you present your driver's license to the bank to prove that you are you, the bank (service provider) is trusting that the DMV (identity provider) has properly vetted you with birth certificates, social security cards, or other identity information. Because of this trust, or federation, you don't have to carry all of these documents with you everywhere and prove to every single person that you are you. They trust the DMV (or whatever institution in your country provides driver's licenses) to have taken the appropriate steps to prove your identity.
 To paraphrase Gartner, Identity and Access Management is the act of getting the right people the right access to the right resources at the right time. Central to that concept is the right people.
To paraphrase Gartner, Identity and Access Management is the act of getting the right people the right access to the right resources at the right time. Central to that concept is the right people.
 Even these steps aren't as secure as they could be. Self service password reset rides that delicate balance between productivity and security. Users will forget passwords and get locked out, to minimize the disruption to their work day, you need to offer self service with as few roadblocks as possible. However, the bad guys can take advantage of this lack of roadblocks and reset passwords.
Even these steps aren't as secure as they could be. Self service password reset rides that delicate balance between productivity and security. Users will forget passwords and get locked out, to minimize the disruption to their work day, you need to offer self service with as few roadblocks as possible. However, the bad guys can take advantage of this lack of roadblocks and reset passwords. 
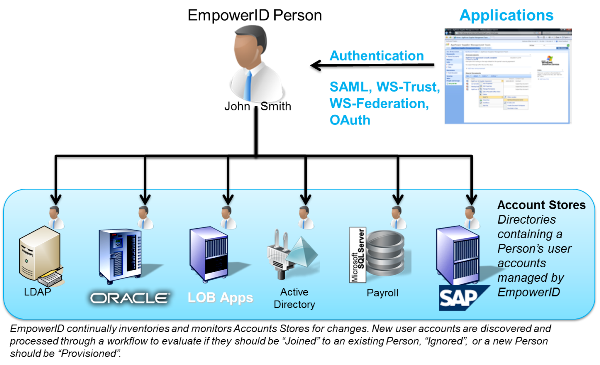
 You don't do it with cloud vendors or traditional IAM solutions. EmpowerID's tagline is a "New breed of Identity Management" and this is why. The platform was built from the ground up without the burdens of acquisitions or partnerships to create the full suite. So, the whole product line shares the same RBAC model, the same API layer, the same metadirectory, the same visual workflow designer. It is a true platform.
You don't do it with cloud vendors or traditional IAM solutions. EmpowerID's tagline is a "New breed of Identity Management" and this is why. The platform was built from the ground up without the burdens of acquisitions or partnerships to create the full suite. So, the whole product line shares the same RBAC model, the same API layer, the same metadirectory, the same visual workflow designer. It is a true platform.
 Reading an article by Earl Perkins titled
Reading an article by Earl Perkins titled 
 The first part that is out of control is that individual business units can go out and contract with a cloud application; they don't necessarily need to rely on IT to install it and configure it. They usually get a web-based management console and take to doing the provisioning & deprovisioning manually despite there being a much smarter way to handle it.
The first part that is out of control is that individual business units can go out and contract with a cloud application; they don't necessarily need to rely on IT to install it and configure it. They usually get a web-based management console and take to doing the provisioning & deprovisioning manually despite there being a much smarter way to handle it.

 The biggest benefit to attribute based access control (ABAC) is its flexibility. You basically are assigning permissions to anyone who meets a certain criteria. Dynamically. As soon as you change a person's job, location, employment status, any attribute in any system you want, you are changing their permissions.
The biggest benefit to attribute based access control (ABAC) is its flexibility. You basically are assigning permissions to anyone who meets a certain criteria. Dynamically. As soon as you change a person's job, location, employment status, any attribute in any system you want, you are changing their permissions.

