You know that guy in accounting you just don't like and wish you didn't have to talk to? Well, there's a chance that you don't have to! Separation of Duties (SOD) to the rescue.
 It doesn't really work like that but there are some mutually exclusive roles. One where if you have these sets of permissions, you cannot have another set of permissions. Some of these are security related (for example, you have permission to create a user, you should not have permission to add them to the financials group, this keeps one person from being able to create a fake user to access critical financial reports). Some are regulatory (for example, in a bank the analysts should not be able to have access to customer records, the bankers should not have access to analyst reports).
It doesn't really work like that but there are some mutually exclusive roles. One where if you have these sets of permissions, you cannot have another set of permissions. Some of these are security related (for example, you have permission to create a user, you should not have permission to add them to the financials group, this keeps one person from being able to create a fake user to access critical financial reports). Some are regulatory (for example, in a bank the analysts should not be able to have access to customer records, the bankers should not have access to analyst reports).
Once you are controlling permissions and access with roles (using Role based access control aka RBAC), it is simple to make roles mutually exclusive. If you are a member of one role, you cannot be a member of another. If you are a member of one role, you need CEO approval to be a member of another. This creates a separation of duties.
I always picture it in action like a Hollywood movie...you need two keys to detonate the bomb and there is a tense standoff as the one guy knows they shouldn't do it. Separation of duties is just like that. Just. Like. That.
Once you've configured your roles to show what your users can do, you need to take that next deeper dive into what that same user shouldn't be able to do. A good mapping of roles and SOD rules will make your organization more secure and your auditors much happier.
If you are one of those "a picture is worth a thousand words" types, give us 15 minutes to show you how SOD works in RBAC by scheduling a demonstration.

 But even with the greatest role structure ever created, there is going to be that one folder or that one system or that one cloud application that is just a bit different. You don't want to have to create a new role for this one single use case, you might just want to modify it a bit.
But even with the greatest role structure ever created, there is going to be that one folder or that one system or that one cloud application that is just a bit different. You don't want to have to create a new role for this one single use case, you might just want to modify it a bit.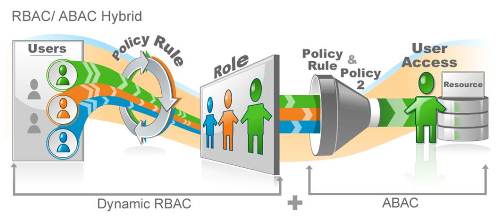

 A common requirement for single sign on (SSO) for partners is that access to systems be role based. This means that when a partner authenticates in to your system, you can give granular access to this user based on their role (or what you know about them).
A common requirement for single sign on (SSO) for partners is that access to systems be role based. This means that when a partner authenticates in to your system, you can give granular access to this user based on their role (or what you know about them).
 You need to fully integrate
You need to fully integrate 
 It's an age old question, do you want to go with roles or Active Directory group management? The answer is, why do you have to choose? Do both. Roles and groups.
It's an age old question, do you want to go with roles or Active Directory group management? The answer is, why do you have to choose? Do both. Roles and groups.
 For years and years,Microsoft has been recommending AGDLP as the way to manage your file system permissions. User and computer accounts are members of global groups which are members of domain local groups that give resource permissions. This is, to put it mildly, the old and busted way of doing things (OBWDT for short).
For years and years,Microsoft has been recommending AGDLP as the way to manage your file system permissions. User and computer accounts are members of global groups which are members of domain local groups that give resource permissions. This is, to put it mildly, the old and busted way of doing things (OBWDT for short).
 I had a customer years ago who couldn't keep Active Directory identity information accurate, so they gave everyone access to ADUC. You know, so that the users could update their own address, etc. This company went bankrupt; that's what happened when you give fully privileged ADUC access to more than the handful that should have it, you go bankrupt.
I had a customer years ago who couldn't keep Active Directory identity information accurate, so they gave everyone access to ADUC. You know, so that the users could update their own address, etc. This company went bankrupt; that's what happened when you give fully privileged ADUC access to more than the handful that should have it, you go bankrupt.
 Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.
Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.
 The cloud is like the wild west right now. Cloud applications are roaming the plains like gunslingers in a Spaghetti Western. That's a crazy analogy but the point is that all the hard work IT has done over the last decade to corral identities within your network has been rendered useless in the cloud.
The cloud is like the wild west right now. Cloud applications are roaming the plains like gunslingers in a Spaghetti Western. That's a crazy analogy but the point is that all the hard work IT has done over the last decade to corral identities within your network has been rendered useless in the cloud.
 This means having an identity management platform that is built on the idea of roles. Provisioning to different systems based on roles. Granting access to resources based on roles. Workflow levels based on roles. Single sign-on based on roles. Roles have to be core to the identity and access management platform that you choose.
This means having an identity management platform that is built on the idea of roles. Provisioning to different systems based on roles. Granting access to resources based on roles. Workflow levels based on roles. Single sign-on based on roles. Roles have to be core to the identity and access management platform that you choose.

