Your finance department is watching the cloud. Not because they are tech literate and following IT trends, but because they can cut your budget quickly with cloud applications. And it's up to you to help them before they help themselves.
Your finance department is watching the cloud. Not because they are tech literate and following IT trends, but because they can cut your budget quickly with cloud applications. And it's up to you to help them before they help themselves.
In the on premise world, if a user leaves the company and you keep an application account for a few extra weeks, it only hurts your security. In the cloud world, you just paid an extra month of service for a user account you didn't need to. Take a look at your internal and external turnover, pull out a calculator and see if you can make a dent in your budget by managing your cloudy accounts better.
The way I see it, you have two simple options to help you reduce your monthly cloud expenditures:
- timely provisioning & deprovisioning of all user accounts
- role based provisioning to the cloud applications
The first is obvious, if a user leaves the company, you need to deprovision ALL of their accounts, on premise and cloud. A metadirectory that has inventoried all of their accounts from connected systems (AD, HR, ERP, Salesforce, Gotomeeting, etc) can delete or deactivate those accounts quickly and easily. This is your external turnover.
But what about internal turnover? That user who moves from marketing to sales and needs new access to some systems (SharePoint sales site and the line of business quote application for example) and different access to other systems (like Salesforce)? And they certainly don't need access to applications like their cloud based marketing automation software (Hubsport or Eloqua).
They are going to have a different role in your metadirectory (now sales in Iowa instead of marketing in Ohio) and that can trigger the workflows that will provision new user accounts (in that quote application), change access in some (a different native application role in Salesforce), and deprovision access in their marketing automation application (like HubSpot or Eloqua).
Did you see what just happened by managing application access and provisioning by roles? We just deleted a cloud based application account (the marketing automation account) and saved the company money. Every single month. If you are handling this manually or allowing the line of business (marketing department) to manage it, chances are the company is paying for a lot of cobwebbed accounts in your cloud applications.
Keep finance off your back; take a look at empowerID to manage your role based provisioning for the cloud.

 The bane of every SharePoint project is permissions and rights. Access is controlled via SharePoint groups, these quirky little groups that exist in the SharePoint vacuum and only in the SharePoint vacuum. SharePoint 2010 introduced the ability to control access via Active Directory groups but gives no way to manage the membership of these groups. So you end up with site admins managing permissions manually or just letting it die on the vine.
The bane of every SharePoint project is permissions and rights. Access is controlled via SharePoint groups, these quirky little groups that exist in the SharePoint vacuum and only in the SharePoint vacuum. SharePoint 2010 introduced the ability to control access via Active Directory groups but gives no way to manage the membership of these groups. So you end up with site admins managing permissions manually or just letting it die on the vine.
 I'm being facetious of course, there's nobody in IT named Bob usually. But that's where your identity and access management platform comes in. It is busy giving people access to systems and you need to make sure that you are inserting the "right" into that sentence & process.
I'm being facetious of course, there's nobody in IT named Bob usually. But that's where your identity and access management platform comes in. It is busy giving people access to systems and you need to make sure that you are inserting the "right" into that sentence & process.
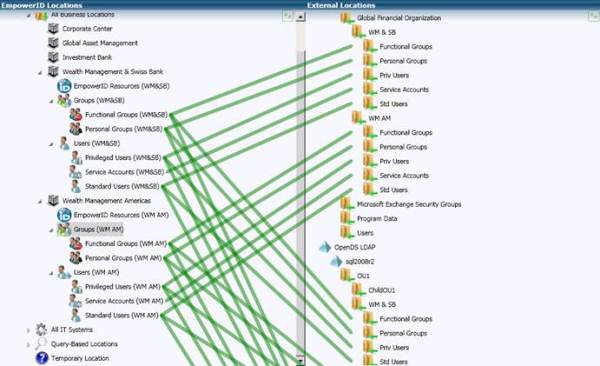
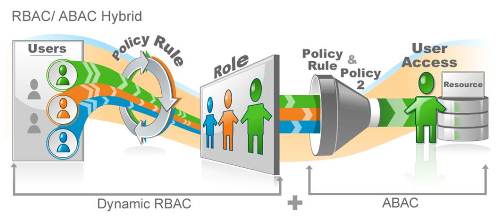
 Role based authentication is not RBAC. RBAC determines what resource or application you can access based on your role while role based authentication determines how you will need to authenticate to access that resource or application. In the way EmpowerID performs this function, it is more akin to adaptive authentication.
Role based authentication is not RBAC. RBAC determines what resource or application you can access based on your role while role based authentication determines how you will need to authenticate to access that resource or application. In the way EmpowerID performs this function, it is more akin to adaptive authentication.
 SharePoint's People Picker is one of the strangest user interfaces in the world. A SharePoint site admin generally gives permissions to either SharePoint groups or Active Directory groups. But if he/she uses AD groups, he/she doesn't know who is a member.
SharePoint's People Picker is one of the strangest user interfaces in the world. A SharePoint site admin generally gives permissions to either SharePoint groups or Active Directory groups. But if he/she uses AD groups, he/she doesn't know who is a member.
 Talking to a client the other day about enterprise to cloud access, it became apparent that before considering cloud SSO, cloud provisioning needed to be taken care of. More than that, role based cloud provisioning.
Talking to a client the other day about enterprise to cloud access, it became apparent that before considering cloud SSO, cloud provisioning needed to be taken care of. More than that, role based cloud provisioning.
 Let's think through a use case. Your internal developers have created a web app that is crashing, they don't have access to production but need to run some tests and troubleshoot what has happened. They could work with an IT admin and get it done using their credentials but that doesn't always work.
Let's think through a use case. Your internal developers have created a web app that is crashing, they don't have access to production but need to run some tests and troubleshoot what has happened. They could work with an IT admin and get it done using their credentials but that doesn't always work.

 One of the main issues with access requests by your users is they don't know what to ask for! Think about it, your user knows that they want to see the prior year's sales results sorted by average receivables age. They go to your access resource catalog and sure enough there isn't a resource named that.
One of the main issues with access requests by your users is they don't know what to ask for! Think about it, your user knows that they want to see the prior year's sales results sorted by average receivables age. They go to your access resource catalog and sure enough there isn't a resource named that.