The average corporate user has to access over 16 applications in the course of their jobs, that can be up to 16 sets of credentials (username and password). Assuming 30 seconds of extra time per credential, that's about 40 minutes per week wasted on usernames and passwords. Factor in a forgotten or locked password per week and you are up to almost an hour spent per week dealing with this wholly un-neccessary routine of passwords.
Why? Single sign on. It is better, it's easier, it's more secure.
Your user has to authenticate at least once, usually with their Windows credentials. Now you know who they are. You know what applications they have access to, both on premise and cloud. So why are they having to continually prove their identities to each application?
 Of those, 16 web and cloud applications, probably half of them support federation, usually SAML or OAuth. Note: EmpowerID supports SAML, OAuth, OpenID, WS-Trust, and WS-Federation. You can federate with those applications, knowing that it trusts that you know who you users are. Your Identity Provider (EmpowerID) will simply send a token to that application verifying who your user is and the access they have. No username or password typed.
Of those, 16 web and cloud applications, probably half of them support federation, usually SAML or OAuth. Note: EmpowerID supports SAML, OAuth, OpenID, WS-Trust, and WS-Federation. You can federate with those applications, knowing that it trusts that you know who you users are. Your Identity Provider (EmpowerID) will simply send a token to that application verifying who your user is and the access they have. No username or password typed.
For those web applications that are not federated, Web Access Management (WAM) is the way to go. For these applications, EmpowerID either uses an agent in the application or a reverse proxy to secure the URL and pass a secure header variable with your user's credentials. This tried and true method can usually cover a quarter of applications.
For those remaining applications that cannot federate or use WAM, secure password vaulting can keep the exact same SSO experience for your users. Your user will claim the account, enter their username and password ONCE, and EmpowerID will encrypt and pass these credentials as your user signs in.
Your users will have a single SSO dashboard for all of these applications and never have to type another set of credentials for any web applications, on premise or the cloud.
That being said, making it too easy can be an issue sometimes as well. Say one of those web applications stores all of the company secrets, like the Colonel's secret recipe or the location of the exhaust vent on the Death Star. You have to secure that, right?
That's when you add a second factor authentication to that specific application. Incorporate an OATH token into the authentication process for that application, send it to a known device for the user and be doubly sure that they are who they say they are. With EmpowerID, this two factor authentication can be added into any SSO workflow and even be based on the user's role.
Save your users time while increasing your security seems like a win-win situation with single sign on. Schedule a demonstration of EmpowerID's complete SSO capabilities and/or download our whitepaper on the Top 5 Federated Single Sign On Scenarios.

 The project list of things to automate is a mile long, starting with user provisioning and permissions, group and role memberships, identity synchronization, and so on. For delegation, the list is equally as long -- password reset, group membership, single sign-on, cloud accounts, and the lowest hanging fruit: Active Directory self-service.
The project list of things to automate is a mile long, starting with user provisioning and permissions, group and role memberships, identity synchronization, and so on. For delegation, the list is equally as long -- password reset, group membership, single sign-on, cloud accounts, and the lowest hanging fruit: Active Directory self-service.
 The OATH encryption algorithm is an open source standard and, as such, is widely available. EmpowerID ships with an OATH server to encrypt the OATH token while clients such as Google Authenticator are free and widely available for smart phones and tablets.
The OATH encryption algorithm is an open source standard and, as such, is widely available. EmpowerID ships with an OATH server to encrypt the OATH token while clients such as Google Authenticator are free and widely available for smart phones and tablets.
 There are basically two types of group management: delegated group management and dynamic group management. Each has its place. There is a third facet to group management where you manage resources and what groups have access to the resource but that is slightly out of scope of our discussion here.
There are basically two types of group management: delegated group management and dynamic group management. Each has its place. There is a third facet to group management where you manage resources and what groups have access to the resource but that is slightly out of scope of our discussion here.
 I like to think that I am unique. However, to my IT, security and identity teams, I am just a mix of sales, marketing, management and location roles. Knowing those four things about me can generally define what system access I will need.
I like to think that I am unique. However, to my IT, security and identity teams, I am just a mix of sales, marketing, management and location roles. Knowing those four things about me can generally define what system access I will need.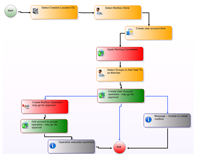 As you are designing these role based user provisioning rules, you are probably mapping them on a whiteboard. EmpowerID's visual workflow platform actually allows you to drag and drop shapes (identity actions such as provision account, go for approval, etc) exactly as you are drawing it. Though it is most likely more colorful and exciting in EmpowerID!
As you are designing these role based user provisioning rules, you are probably mapping them on a whiteboard. EmpowerID's visual workflow platform actually allows you to drag and drop shapes (identity actions such as provision account, go for approval, etc) exactly as you are drawing it. Though it is most likely more colorful and exciting in EmpowerID!
 In a perfect world, all of your applications would run on one OS, built by one vendor and speak to each other seamlessly. Every user of every application would have the correct level of access and sign on easily with a single set of secure credentials. Of course, this perfect world doesn't exist and will never exist.
In a perfect world, all of your applications would run on one OS, built by one vendor and speak to each other seamlessly. Every user of every application would have the correct level of access and sign on easily with a single set of secure credentials. Of course, this perfect world doesn't exist and will never exist.
 The first two Identity Management hurdles you have to overcome are provisioning and Single Sign-on. Without proper IdM planning you could very easily end up back in the dark ages of manual provisioning for your cloud applications.
The first two Identity Management hurdles you have to overcome are provisioning and Single Sign-on. Without proper IdM planning you could very easily end up back in the dark ages of manual provisioning for your cloud applications.
 Security groups seem like the best fit from 30,000 feet...both AD and Dynamics AX are part of the Microsoft stack. Microsoft has set it up so that if you are in a specific security group for Dynamics AX , you can authenticate and use Dynamics AX. But they stopped there, close but not close enough to actually use the solution for our client's needs.
Security groups seem like the best fit from 30,000 feet...both AD and Dynamics AX are part of the Microsoft stack. Microsoft has set it up so that if you are in a specific security group for Dynamics AX , you can authenticate and use Dynamics AX. But they stopped there, close but not close enough to actually use the solution for our client's needs.
 Where we always do better than our competition is our IAM implementation plan. We believe in putting the full solution and plan and cost and SOW up front to help make the decision easier for our clients. Other vendors don't always do that; if you found this blog post by searching for IAM implementation plan then you might already realize that. Here are the items to consider when looking for an implementation plan from your IAM vendor.
Where we always do better than our competition is our IAM implementation plan. We believe in putting the full solution and plan and cost and SOW up front to help make the decision easier for our clients. Other vendors don't always do that; if you found this blog post by searching for IAM implementation plan then you might already realize that. Here are the items to consider when looking for an implementation plan from your IAM vendor.
 Remember your first day on the job at your company, you were given access to a few things, keys to the kingdom if you will. A year later you were promoted, given new responsibilities and a few more of these "keys". By the time you've been at a company for a few years, your "keychain" looks like one of those giant keyrings that a NY super has.
Remember your first day on the job at your company, you were given access to a few things, keys to the kingdom if you will. A year later you were promoted, given new responsibilities and a few more of these "keys". By the time you've been at a company for a few years, your "keychain" looks like one of those giant keyrings that a NY super has.

