Tackling the cleaning up of Active Directory can be a cumbersome chore to say the least. Without the proper tools you can easily get stuck searching for expired accounts, groups with no members and even worse, users with access to resources that should have been removed.
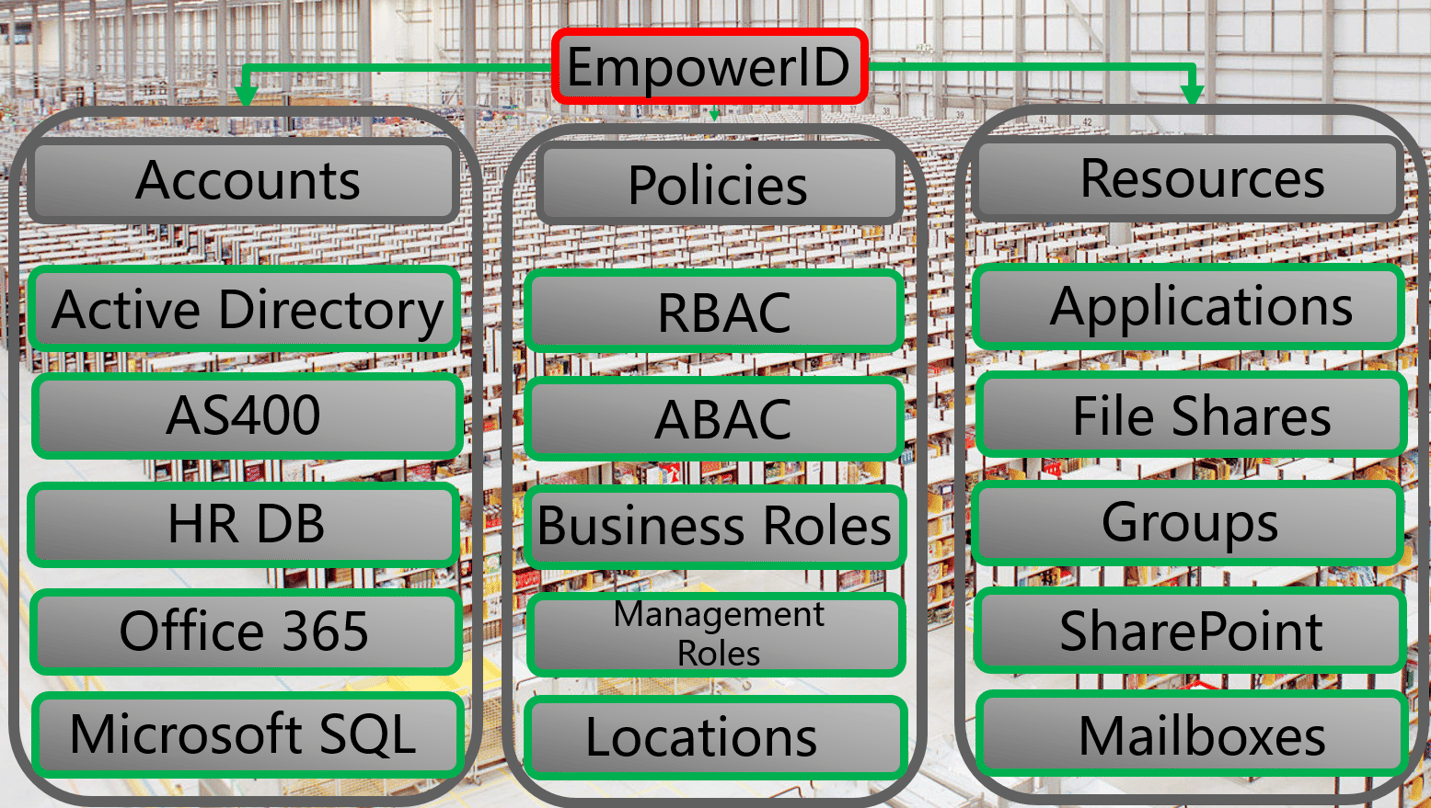
EmpowerID 2016 connects and inventories all of your systems providing a unique platform to easily manage a spring cleanup. Allowing your team to easily identify risky access, out of date users, groups with no members or even users with access they should not have it is the fastest way to get control of your current environment or even an environment that you are bringing on board. Best of all EmpowerID enpowers your helpdesk and business users to manage things like password resets, group and application access and more.
Directory Cleanup Check List
Active Directory Cleanup:
EmpowerID continuously inventories and monitors your systems for changes. This produces a large amount of actionable intelligence that can be used to clean up your directories. Common candidates for cleanup include:
- Dormant Accounts - EmpowerID can help you identify user accounts that have not been used in a while and apply automated clean-up tasks such as removing group memberships.
- Groups with No Owners – Groups without owners represent an audit risk and can often be old groups that are no longer used. EmpowerID assists with identifying owners and provides processes to assign ownership.
- Groups with No Members - Groups with no members can be a potential security risk and are often an easy choice for cleanup.
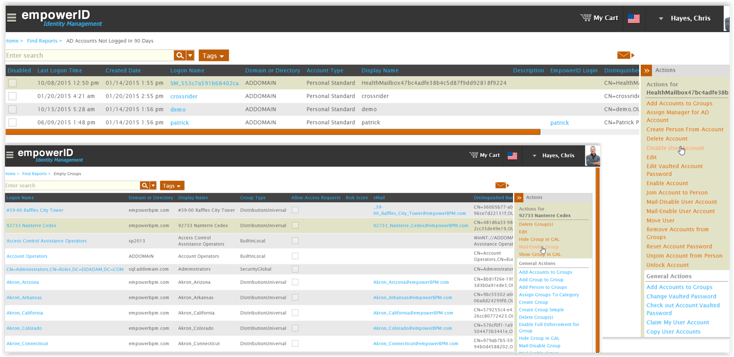
Delegated Administration:
This creates an immense group management challenge for IT security departments as each system is a new security island with its own set of users and groups to manage. EmpowerID solves this security challenge by applying a single security model to replace security administration tools and removes the requirement to grant native permissions in order to perform identity administration. Group admins can manage groups in any system, on-premise and Cloud in a single web-based console with laborious multi-step processes automated by visually-designed workflows. The workload is further reduced by enabling business users the ability to manage access to the groups they own in a non-technical interface.
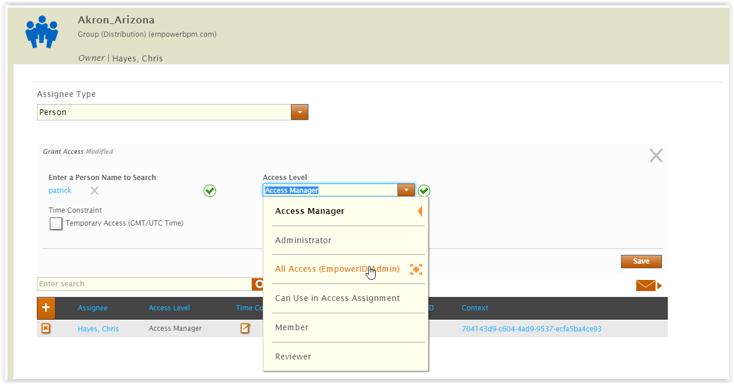
Dynamic Group Automation:
Automating the bulk of your group management tasks is the key to lowering management costs and keeping users happy and productive with shorter wait times. EmpowerID’s Dynamic Hierarchies engine is like auto-pilot for the most common security and distribution groups most organizations need. It automatically creates, manages the membership and retires groups based on the most common criteria (manager, department, location, etc.).
Manage On-Premise and Cloud Groups:
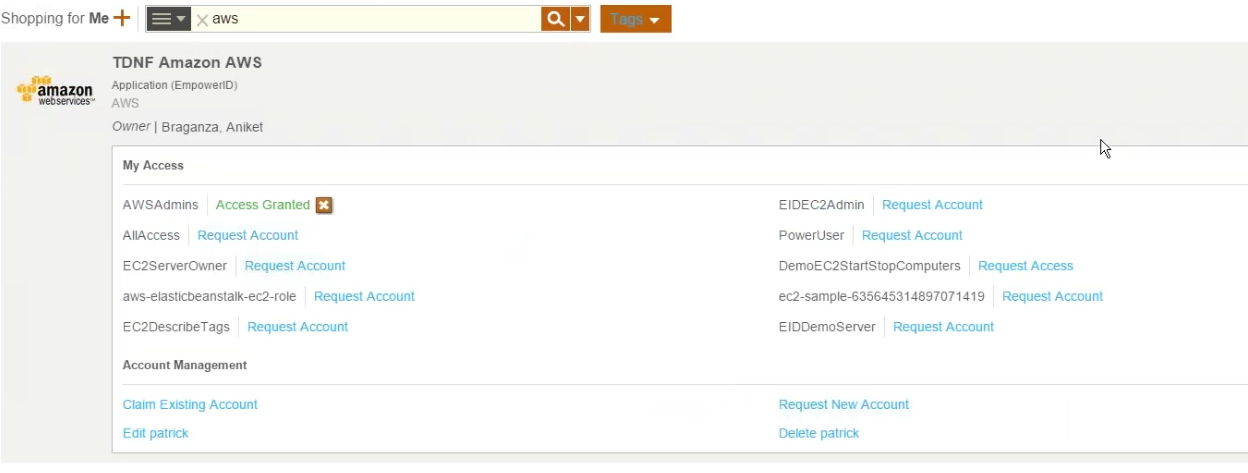
EmpowerID manages your groups wherever they might be. A huge library of connectors allows for rapid onboarding of commercial Cloud and on-premise applications. The most popular systems are fully supported with in-depth functionality for managing groups and roles in systems such as Office 365, Google Apps, Amazon AWS, SalesForce.com, AD, LDAP, AS/400, Box.com, local groups on Windows Servers, SharePoint, and others. Custom-developed applications can be easily accommodated using the EmpowerID Universal Connector.

Compliance and Recertification:
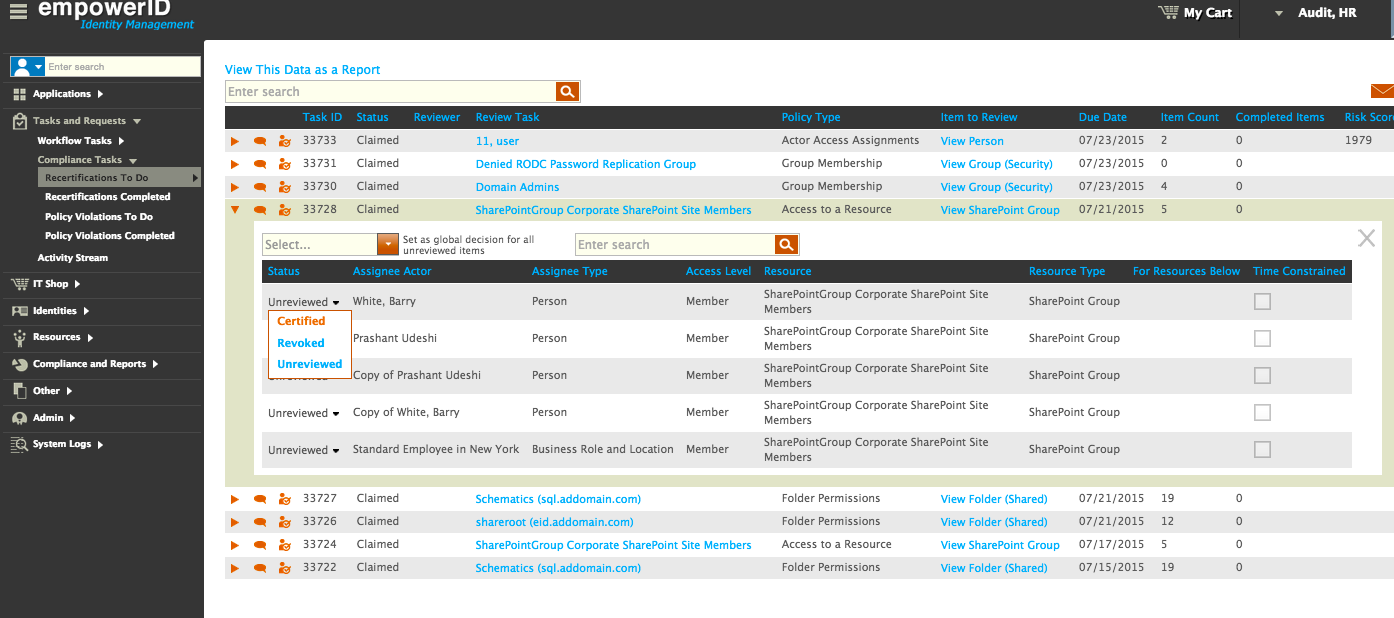
EmpowerID will become the key tool allowing your directory security team to breeze through audits, saving time and money. The modern organization, has groups scattered across a wide mix of on-premise and Cloud applications and directories. This highly fragmented and siloed environment is a huge headache when it comes to producing the data required for periodic group membership recertification. This process becomes almost automatic as EmpowerID continuously monitors and inventories your on-premise and Cloud directories detecting groups memberships and any changes. EmpowerID handles the entire group lifecycle so when it comes around to audit time there already exists a complete audit trail for all group centered activities from self-service to delegated administration. Built-in attestation policies allow for rapid periodic recertification of group membership by their owners to eliminate the hassle of auditing this critical infrastructure. Risk-based separation of duties policies allow for toxic combinations of access to be defined, detected, and remediated if discovered.
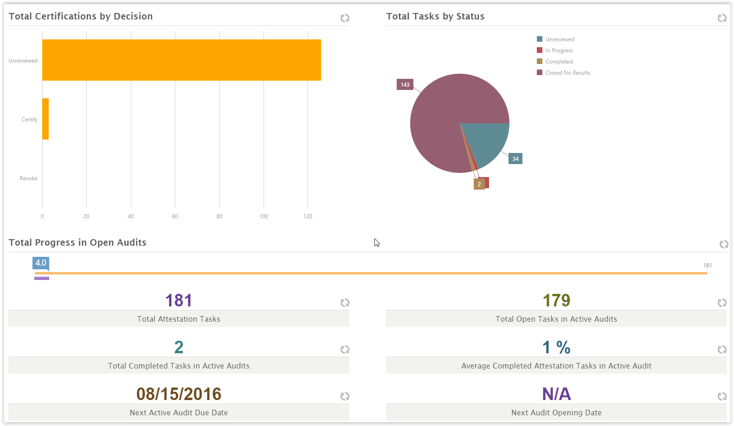
Reporting and Alerting:
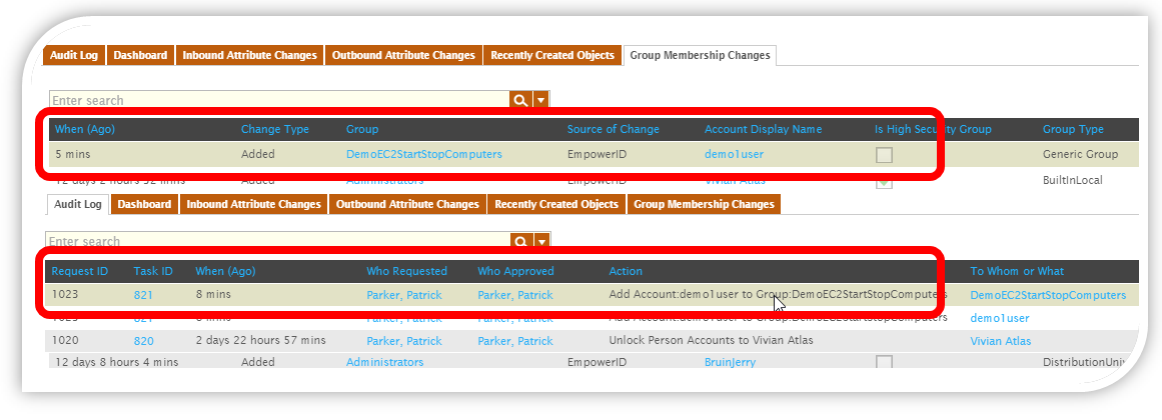
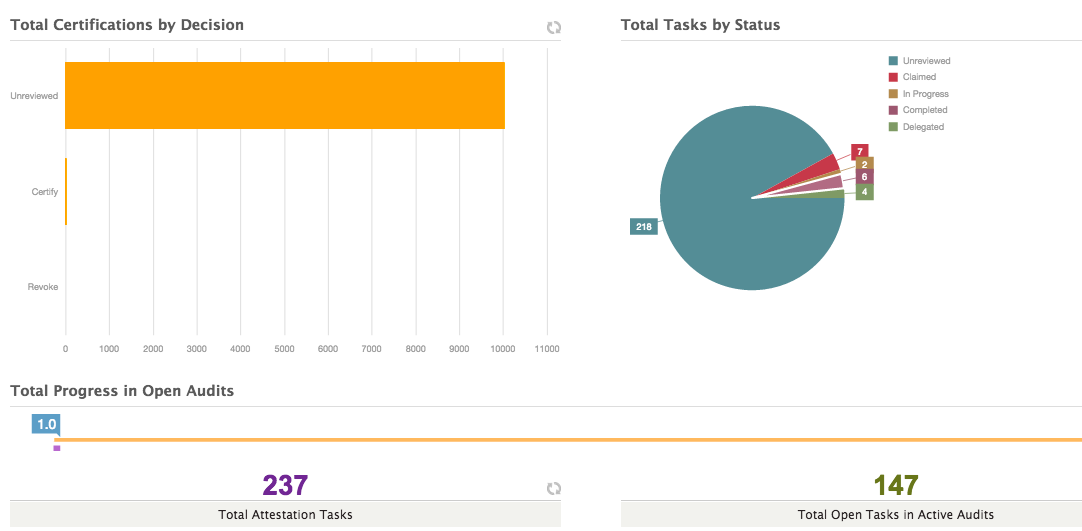
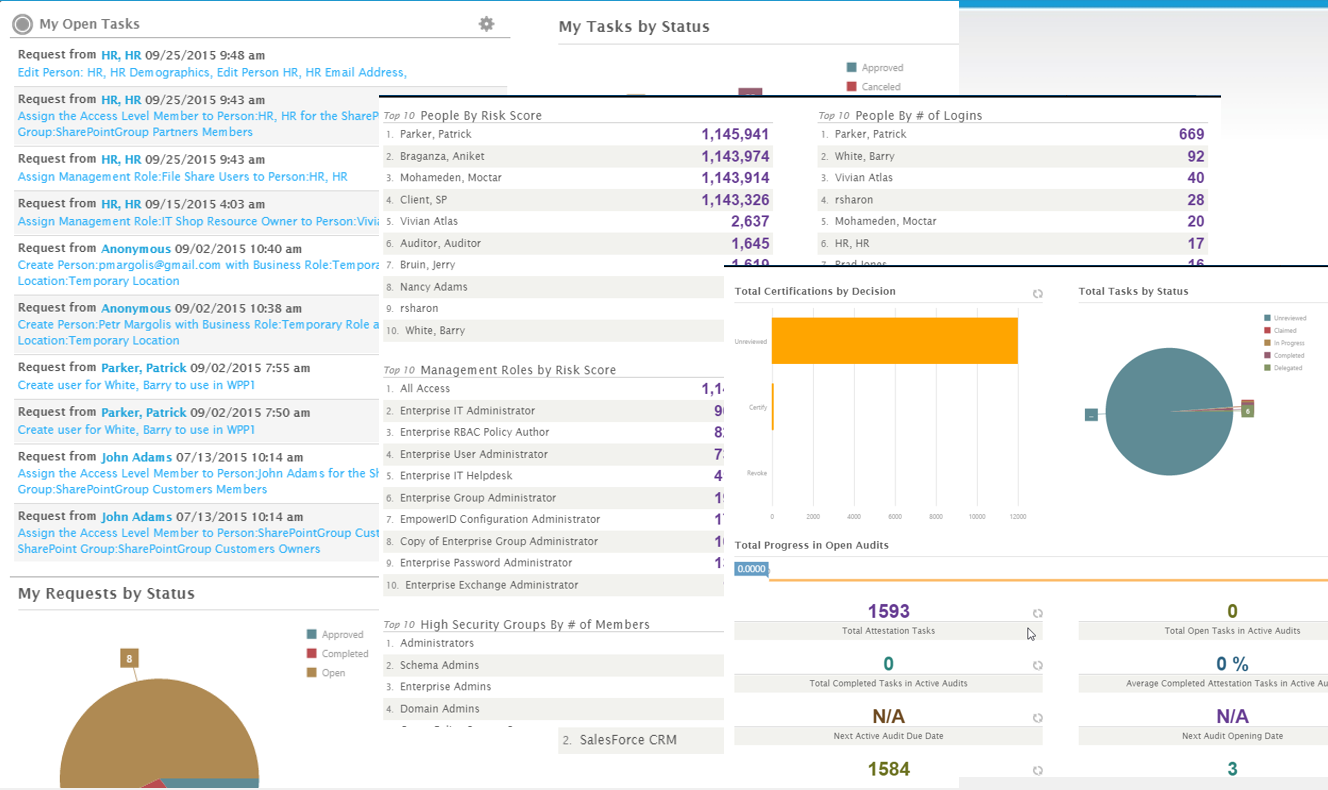
EmpowerID brings intelligence and in-depth visibility to assist with managing your Cloud and on-premise groups. All systems are continuously inventoried and monitored for changes. This includes the creation of new groups, group membership changes, and deletion of groups. All changes are logged and the source of the change is noted. Alerts can notify group owners and administrators when membership changes in sensitive groups. These changes can also be rolled back automatically if desired. Hundreds of statistics and metrics are displayed in friendly dashboards allowing visibility into how your environment is changing and a large list of out of the box reports keeps everyone up to date.
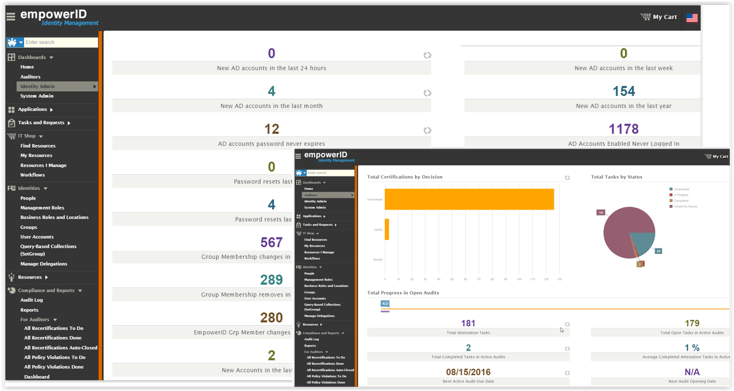
Please contact us to find out how we have helped hundreds of organizations get a handle of their identity landscape and how we can help you.










 Free Office 365 Manager license with every User/Group Manager purchase!
Free Office 365 Manager license with every User/Group Manager purchase!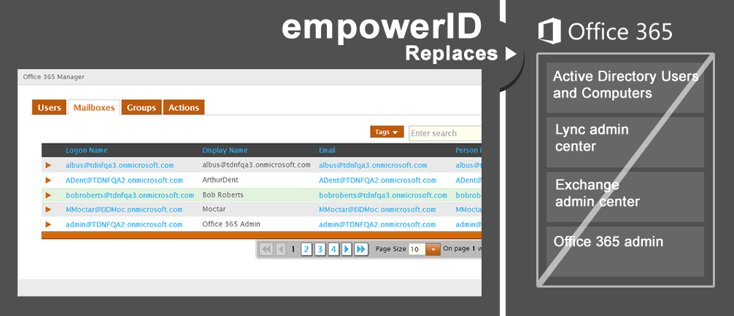

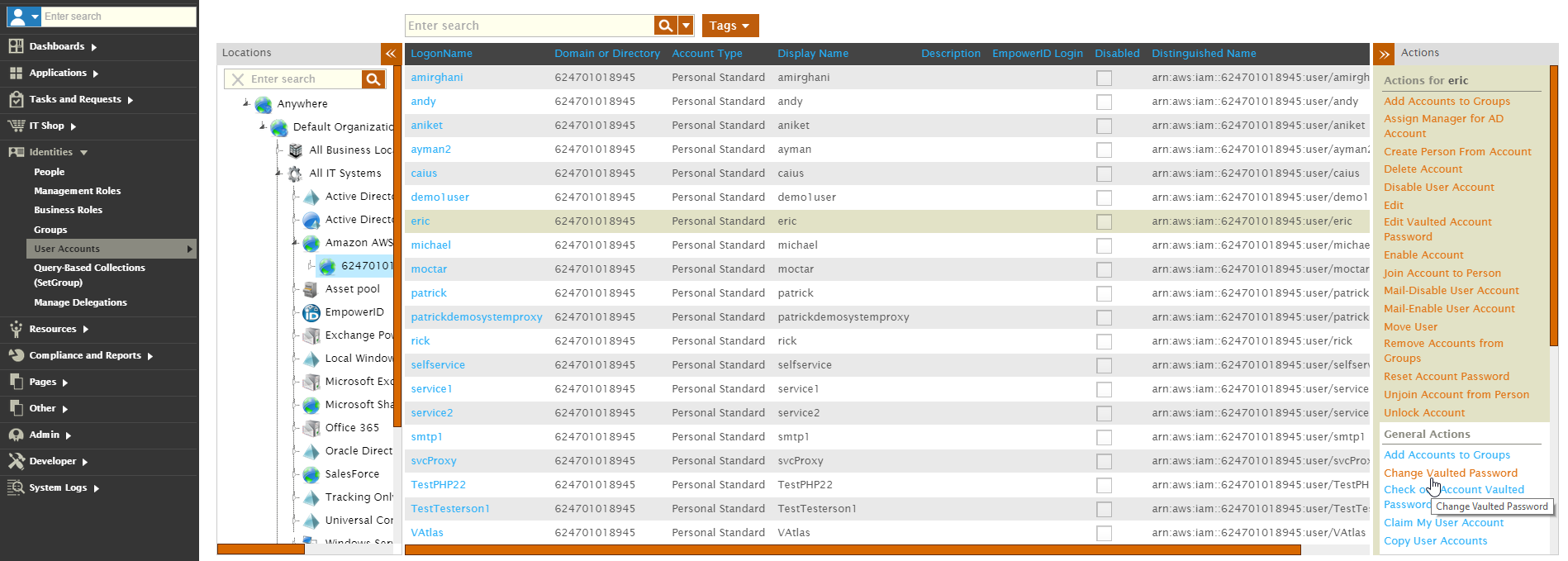
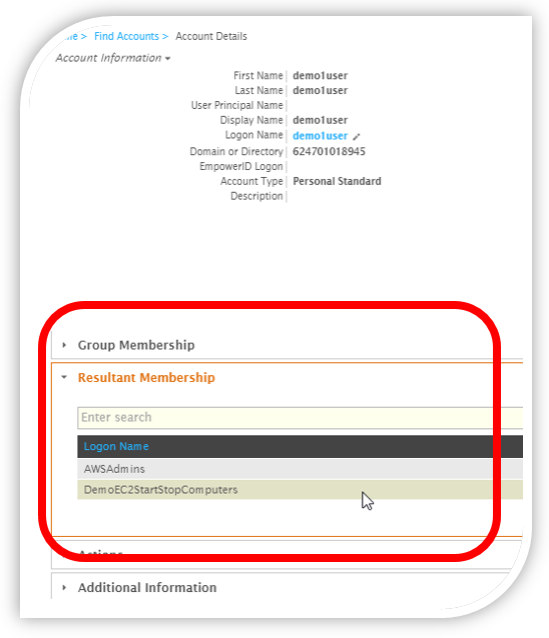
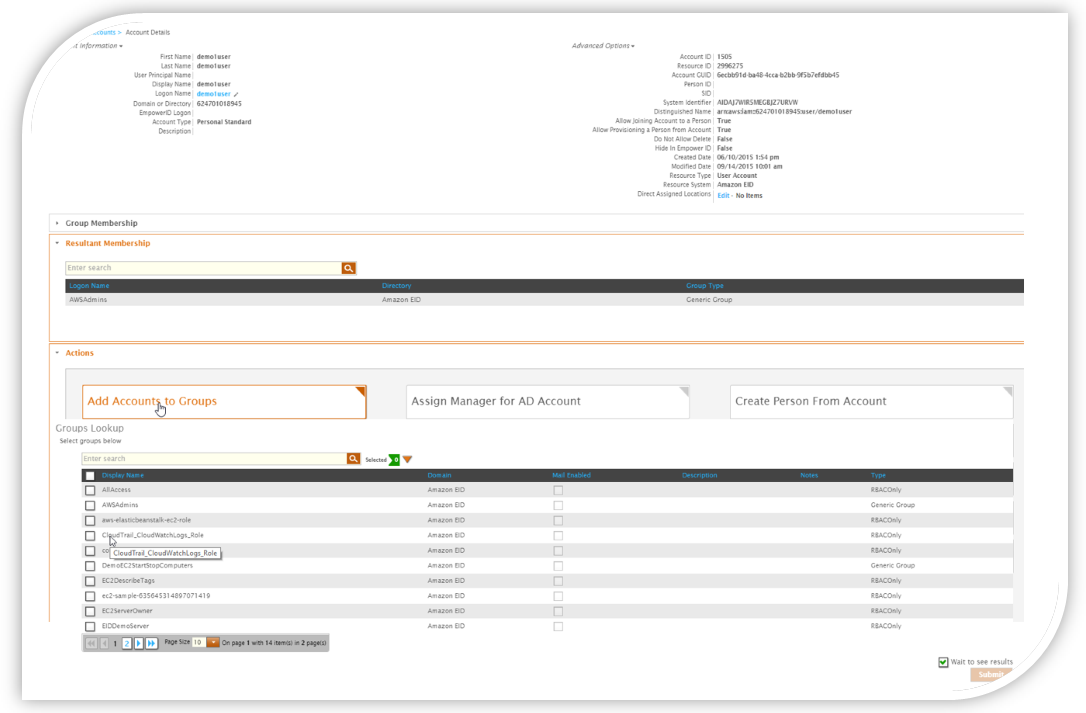 Let's review the group changes for the user below
Let's review the group changes for the user below