The traditional model for self service password reset drives me crazy. The user gets asked questions to prove they are who they say they are. And the system just resets their password. Easy, right? Secure, wrong.
Here is the issue, I can guess most of the answers to your questions by looking at your facebook timeline and the pictures on your cubicle wall. Your first car, your daughter's name, your eye color, and so on. That just isn't as secure as it should be.
 What you need is two factor authentication with your self service password reset. The first factor is the questions, in other words "what you know." The second factor is something you have, whether it's a pager or mobile phone or a keyfob device. With proper two factor authentication, someone is not only going to have to steal your user's memories but their phone also!
What you need is two factor authentication with your self service password reset. The first factor is the questions, in other words "what you know." The second factor is something you have, whether it's a pager or mobile phone or a keyfob device. With proper two factor authentication, someone is not only going to have to steal your user's memories but their phone also!
This still doesn't get you everywhere you need. It is also important to have complexity requirements, either to match or exceed your Active Directory domain policy. My own personal preference, make the complexity pertain to password length rather than crazy characters. It's harder to hack a 72 character sentence than P@ssw0rd. And it's easier to remember the sentence.
Having a proper password synchronization and SSO tool also improves your password security. If users have a dozen passwords to remember they are going to make them easy to hack. They are going to forget them a lot and use easy to hack questions. Make life easier on your users and your security will increase...counter intuitive but true.
Get a second factor in your self-service password reset, it's easy and secure for your users. Click below for a demonstration of how simple this can be.



 Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.
Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.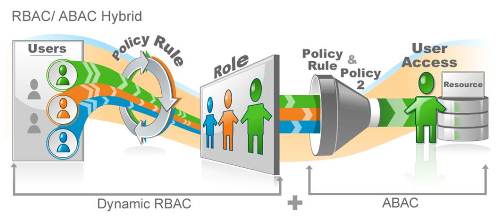

 Dynamic security groups in Active Directory
Dynamic security groups in Active Directory
 The cloud is like the wild west right now. Cloud applications are roaming the plains like gunslingers in a Spaghetti Western. That's a crazy analogy but the point is that all the hard work IT has done over the last decade to corral identities within your network has been rendered useless in the cloud.
The cloud is like the wild west right now. Cloud applications are roaming the plains like gunslingers in a Spaghetti Western. That's a crazy analogy but the point is that all the hard work IT has done over the last decade to corral identities within your network has been rendered useless in the cloud.
 This means having an identity management platform that is built on the idea of roles. Provisioning to different systems based on roles. Granting access to resources based on roles. Workflow levels based on roles. Single sign-on based on roles. Roles have to be core to the identity and access management platform that you choose.
This means having an identity management platform that is built on the idea of roles. Provisioning to different systems based on roles. Granting access to resources based on roles. Workflow levels based on roles. Single sign-on based on roles. Roles have to be core to the identity and access management platform that you choose.
 You want your users to be able to log in to the network, their on premise applications, their cloud applications and all of your partner applications. You want your partners to be able to log in to the applications they need. And you want this to be easy; both for the users involved AND for the IT security team that needs to make it happen.
You want your users to be able to log in to the network, their on premise applications, their cloud applications and all of your partner applications. You want your partners to be able to log in to the applications they need. And you want this to be easy; both for the users involved AND for the IT security team that needs to make it happen.

