 For years and years,Microsoft has been recommending AGDLP as the way to manage your file system permissions. User and computer accounts are members of global groups which are members of domain local groups that give resource permissions. This is, to put it mildly, the old and busted way of doing things (OBWDT for short).
For years and years,Microsoft has been recommending AGDLP as the way to manage your file system permissions. User and computer accounts are members of global groups which are members of domain local groups that give resource permissions. This is, to put it mildly, the old and busted way of doing things (OBWDT for short).
And here is why: try telling me who has access to that file. You know, a user who is nested within a nested group that nobody knows who manages. In fact, you don't even know the last time that group was updated.
So, how do you solve this? True role based access control (RBAC for short).
If you are doing RBAC correctly, you have a metadirectory that is assigning roles dynamically or statically to your users. These roles are granted access to resources. Your RBAC-based file share manager will continuously inventory and monitor for new shared folders and follow a workflow to give the appropriate roles access.
Here's the other side of the coin. A user knows about a shared file or folder and wants access; I saw this use case on an IAM board on LinkedIn today in fact. How does that user request access? Does he or she have any idea what group or groups manage access? No.
Why not give an easy self service format for the end user to request access to the folder that is routed to the correct approvers? Without the end user needing to know a single thing about AGDLP or other technical nonsense. RBAR (rights based approval routing) to the rescue. This workflow knows who can approve and how long that user can have access. A top secret folder being accessed by a contractor, give them access for 3 days, no longer.
Just because Microsoft (MSFT) recommends using an old and busted technique (OBWDT) like AGDLP shouldn't stop you from looking into RBAC to properly solve your file system permissions issues. Schedule a demo ASAP.

 But you cannot manage a user's identity. Because each person is multiple users. They are a user of Salesforce.com, a user of Exchange, a user of quickbooks, et cetera. A user has a department, a title, and a role; but each application they use, gives them a different role, has different identity information about them. Somehow you have to take all of those users and recompile them into a person.
But you cannot manage a user's identity. Because each person is multiple users. They are a user of Salesforce.com, a user of Exchange, a user of quickbooks, et cetera. A user has a department, a title, and a role; but each application they use, gives them a different role, has different identity information about them. Somehow you have to take all of those users and recompile them into a person. 
 I had a customer years ago who couldn't keep Active Directory identity information accurate, so they gave everyone access to ADUC. You know, so that the users could update their own address, etc. This company went bankrupt; that's what happened when you give fully privileged ADUC access to more than the handful that should have it, you go bankrupt.
I had a customer years ago who couldn't keep Active Directory identity information accurate, so they gave everyone access to ADUC. You know, so that the users could update their own address, etc. This company went bankrupt; that's what happened when you give fully privileged ADUC access to more than the handful that should have it, you go bankrupt.
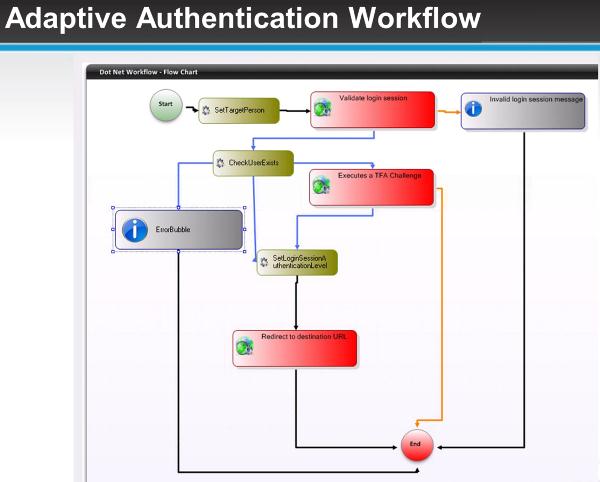


 The trouble is that your users' identities stretch far and wide nowadays. There are tons of internal systems that they need access to, scads of databases holding pertinent pieces of their identities, even multiple AD accounts belonging to the same person. You have data governance being handled by AD security groups without an easy way of knowing who has what access. You have cloud applications that need to know who your user is and what they can do.
The trouble is that your users' identities stretch far and wide nowadays. There are tons of internal systems that they need access to, scads of databases holding pertinent pieces of their identities, even multiple AD accounts belonging to the same person. You have data governance being handled by AD security groups without an easy way of knowing who has what access. You have cloud applications that need to know who your user is and what they can do.
 What you need is
What you need is 


 Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.
Consider what you know about a user from your HRIS: name, department, title, location, shoe size; all the relevant identity information for you to decide their most basic roles (you can determine more granular roles as you learn more about them). From these basic roles, you can provision them into the correct systems.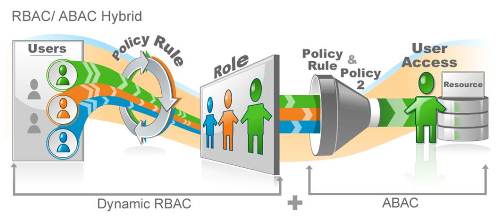

 Dynamic security groups in Active Directory
Dynamic security groups in Active Directory
 The cloud is like the wild west right now. Cloud applications are roaming the plains like gunslingers in a Spaghetti Western. That's a crazy analogy but the point is that all the hard work IT has done over the last decade to corral identities within your network has been rendered useless in the cloud.
The cloud is like the wild west right now. Cloud applications are roaming the plains like gunslingers in a Spaghetti Western. That's a crazy analogy but the point is that all the hard work IT has done over the last decade to corral identities within your network has been rendered useless in the cloud.

