Managing your internal identities is the bread and butter of identity management. You know who your users are (at least you should) and you have a good idea of what they need to do their jobs. If you don't, call us and we'll get EmpowerID running toute suite.
 But there is a whole new realm of identity management you need to think about: partners and customers. Your external identities. You don't hire them so you probably don't have a tried and true process of provisioning. You certainly don't want to give them Active Directory accounts but they need access to a lot of services and systems that you provide.
But there is a whole new realm of identity management you need to think about: partners and customers. Your external identities. You don't hire them so you probably don't have a tried and true process of provisioning. You certainly don't want to give them Active Directory accounts but they need access to a lot of services and systems that you provide.
We are seeing more and more of this in the marketplace, how to expose services to your external identities and how to track them. It sounds just like identity management but not all of the traditional solutions work here.
This is where the platform approach really works. You can provision new users, heck even offer self-provisioning, and assign roles immediately. These roles have access to certain parts of the application or portal. The IAM platform can confirm that this is indeed a customer in the CRM system, and provide advanced access or more privileged roles based on any number of criteria that you know about them.
By storing this external user identity in the metadirectory, you can authenticate directly against that directory, utilizing SharePoint 2010's claim provider functionality. Now, in one place you have provisioning, role assignment, and authentication. You can easily keep track of your external users, have an audit trail of their authentication and role changes, and manage external customers and partners like they're employees. But easier.
Gone are the days of trying to create a separate domain for external users and not being able to restrict access to customer facing applications. Utilizing the EmpowerID platform, you can treat customers, partners and other external users with the same role based security that you do your internal users.
Take a look at what we did for a very large insurance and healthcare portal to help manage access for external users and schedule a demo now!

 The problem is that Active Directory houses some very sensitive information and many extremely important business processes are keyed off of it. As such, you can't let an end user change their title or direct reports or gain access to the shared folder that houses the 10Q documents. So, when delegating, keep RBAR in mind.
The problem is that Active Directory houses some very sensitive information and many extremely important business processes are keyed off of it. As such, you can't let an end user change their title or direct reports or gain access to the shared folder that houses the 10Q documents. So, when delegating, keep RBAR in mind.
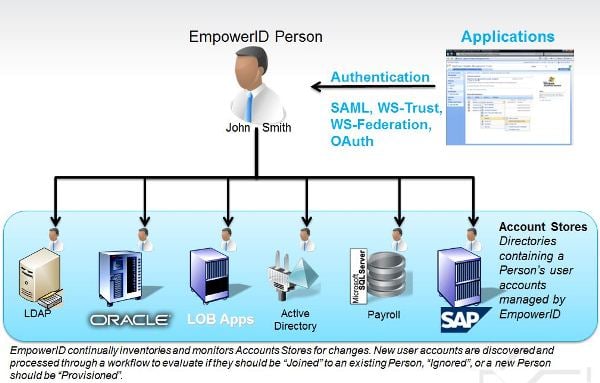
 When you start work in the morning, you authenticate against Active Directory; when you start thinking about identity and access management, you start thinking about Active Directory. Active Directory is at the heart of it all but is often oddly neglected.
When you start work in the morning, you authenticate against Active Directory; when you start thinking about identity and access management, you start thinking about Active Directory. Active Directory is at the heart of it all but is often oddly neglected.
 The question is, will users ever take this advice and stop using passw0rd as their password? No. And, even if they do, they will continue to write it on a post-it note affixed to the bottom of their keyboard. This is the inevitable and painful flaw in any password policy.
The question is, will users ever take this advice and stop using passw0rd as their password? No. And, even if they do, they will continue to write it on a post-it note affixed to the bottom of their keyboard. This is the inevitable and painful flaw in any password policy.
 Once confirmed as a problem, what about a solution? There are two ways to go about this, Google Apps password reset or Google Apps single sign-on. It depends on your infrastructure I'm sure and I'm probably looking at this from a very EmpowerID-centric view, but neither is a difficult proposition.
Once confirmed as a problem, what about a solution? There are two ways to go about this, Google Apps password reset or Google Apps single sign-on. It depends on your infrastructure I'm sure and I'm probably looking at this from a very EmpowerID-centric view, but neither is a difficult proposition.
 A common requirement for single sign on (SSO) for partners is that access to systems be role based. This means that when a partner authenticates in to your system, you can give granular access to this user based on their role (or what you know about them).
A common requirement for single sign on (SSO) for partners is that access to systems be role based. This means that when a partner authenticates in to your system, you can give granular access to this user based on their role (or what you know about them).
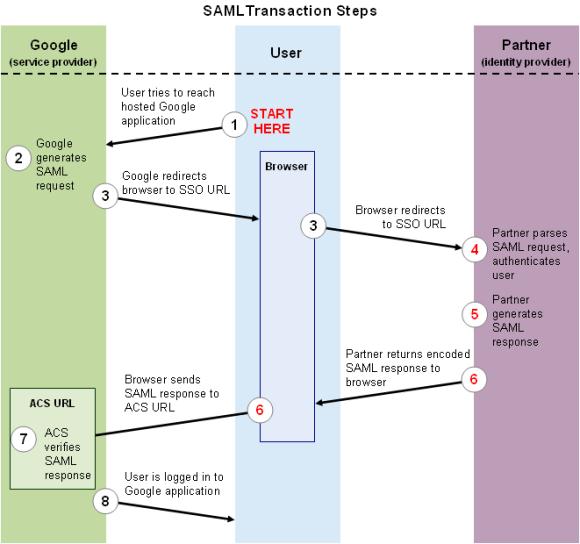.jpg)

 You need to fully integrate
You need to fully integrate 
 It's an age old question, do you want to go with roles or Active Directory group management? The answer is, why do you have to choose? Do both. Roles and groups.
It's an age old question, do you want to go with roles or Active Directory group management? The answer is, why do you have to choose? Do both. Roles and groups.

