SharePoint has always been a good tool, but like most it's useless if it's not adopted (hello, self service password reset!). You have to lower the barriers to entry for SharePoint use while maintaining a strict security policy. You certainly can't make it so easy to use that your maintenance staff has access to your 10K report document repository.
The trick is SharePoint single sign-on (SSO), no? Users authenticate into AD, get put in some groups, you go through the people picker and give site access to groups and BOOM, you're done. No. You're not done. That works for about one day until users change jobs, you create a site for partners to access, you have a site for ex-employees to transfer their 401K, and so on and so on.
 You need to fully integrate SharePoint single sign-on into your role based access control for employees, partners, contractors, alumni, customers, etc. Use varying levels of authentication for each, you are able to offer SSO but utilize roles for what sites each has access to. If the roles are dynamic (and they should be), you never have to touch them again.
You need to fully integrate SharePoint single sign-on into your role based access control for employees, partners, contractors, alumni, customers, etc. Use varying levels of authentication for each, you are able to offer SSO but utilize roles for what sites each has access to. If the roles are dynamic (and they should be), you never have to touch them again.
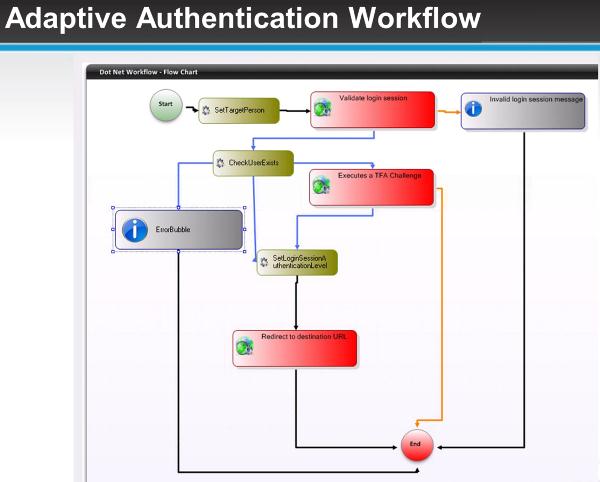
But what does this have to do with single sign-on, that sounds like authorization not authentication. Here's the key...each of those types of users (employees, customers, partners, etc) are going to be able to authenticate a different way and have access to the correct sites. We call it adaptive authentication.
For example, a customer can authenticate into SharePoint using their Facebook credentials. By having a SharePoint claims provider (such as EmpowerID), that customer is authenticated and has access to all public information. If the customer wants to view their account information, they will need a higher level of authentication and they will be prompted to verify who they are with their customer credentials or EmpowerID account or even a second factor authentication like an SMS message.
The same thing happens with your employees. The user logs in with their EmpowerID credentials and has access based on their role. But we also bump up the authentication level and require an RSA token or biometric authentication when they try to access the company financials.
All of your users can access what they are supposed to with one set of credentials and they don't even need to have an Active Directory account to make it work. BUT you are also able to selectively heighten authentication policy based on the role and site being accessed. It's not a matter of just being a member of a certain group, it goes much beyond that all the while reducing barriers to entry for your users and keeping your security policy appropriately strict.
Take a look at what EmpowerID just did for a large healthcare portal with over 150,000 users authenticating to the portal via SAML, WS-Trust, WS-Federation and OAuth-based technologies from over a thousand different healthcare groups.

 While having a discussion with a partner this week, he pointed out that enterprise single sign-on and federation are being confused much less often these days. That led me to asking a few people what the difference is and finding that there is still confusion about the two.
While having a discussion with a partner this week, he pointed out that enterprise single sign-on and federation are being confused much less often these days. That led me to asking a few people what the difference is and finding that there is still confusion about the two.


 What you need is
What you need is 
 The cloud is like the wild west right now. Cloud applications are roaming the plains like gunslingers in a Spaghetti Western. That's a crazy analogy but the point is that all the hard work IT has done over the last decade to corral identities within your network has been rendered useless in the cloud.
The cloud is like the wild west right now. Cloud applications are roaming the plains like gunslingers in a Spaghetti Western. That's a crazy analogy but the point is that all the hard work IT has done over the last decade to corral identities within your network has been rendered useless in the cloud.
 You want your users to be able to log in to the network, their on premise applications, their cloud applications and all of your partner applications. You want your partners to be able to log in to the applications they need. And you want this to be easy; both for the users involved AND for the IT security team that needs to make it happen.
You want your users to be able to log in to the network, their on premise applications, their cloud applications and all of your partner applications. You want your partners to be able to log in to the applications they need. And you want this to be easy; both for the users involved AND for the IT security team that needs to make it happen.

