Security for identities. Managing user access to applications. Auditing user access.
“Ugh”, you might think, “That sounds like more cost, more time, and more responsibility for IT”.
But a platform approach to Identity and Access Management (IAM) that is rich in innovation can result in lower costs, better productivity, and reduced demands for IT resources, while providing managers with better and more timely information.
Take for example a home healthcare provider with $2 billion in revenue and 40,000 employees in 40 states facing constant pressure to reduce costs as a result of declining government reimbursements for their services. This organization had already used their considerable size advantage to create efficiencies and reduce costs wherever possible. Then their Chief Security Officer (CSO) conducted a review of IAM technology and presented his management with a plan that would improve the productivity of their employees, reduce the workload on IT, improve the security for patient data and assist their organization in continuing to be a leader in the quality of patient services.
Built from a series of acquisitions in an industry that experiences high turnover, this organization lacked an efficient process for provisioning home healthcare workers into the many web applications they need to perform their work. The process began with HR creating a manual request for IT to provision a new user into the apps they require, and once this was completed, the new user had to register themselves and create a password in each application. This process was complex and required too much effort for the home healthcare employees to learn and to maintain.
The CSO’s experience with several of the oldest and most installed IAM platforms made him wary of starting a new project with one of them because of their high licensing costs and the difficulty in customizing them to meet an enterprise’s specific needs. He wanted a solution that would be easier to implement and easier to mantain.
After evaluating multiple products, he chose the EmpowerID platform for its different and innovative approach to Identity and Access Management. Built on a single codebase with a workflow core and shipping with hundreds of ready to deploy workflows, the CSO was impressed with EmpowerID's broad functionality and its ability to easily design and to automate complex IAM processes with its visual Workflow Designer.
The CSO determined during a software trial that EmpowerID’s powerful Role-Based Access Control (RBAC) engine could create effective roles based on both an employee’s place in the organizational hierarchy and their location, and it could scale easily for the size of their staff. EmpowerID proved itself to be flexible in also offering Attribute-Based Access Control (ABAC) for their scenarios where the use of contextual policies to govern access is more appropriate.
He also discovered that EmpowerID’s integrated Single Sign-On (SSO) module federates not only with more recent web applications that natively support SAML authentication, but also with legacy applications that lack SAML capabilities. Thus he could accommodate all of his user scenarios end to end, from provisioning to access, using EmpowerID, rather than having to integrate two or more applications.
The CSO concluded that EmpowerID’s “all in one” approach could create the solution they needed in a shorter timeframe with fewer professional services and less risk to their project timeline and budget. The ability to show his management faster ROI helped him to obtain funding for the project.
EmpowerID’s User, Group and SSO Manager modules were then deployed to provision and to manage federated identity for the application portal, allowing new users to be added within hours, instead of days, and enabling the use of one login by a healthcare provider to access all of their applications.
New user onboarding was further simplified by creating a feed from the organization’s PeopleSoft HR application to EmpowerID, which in turn creates all the user accounts and access privileges in the applications they need, based on their business role. New users require less training and are ready to go to work as soon as they claim their identity upon first logging into the application portal.
The home healthcare staff appreciate EmpowerID's friendly HTML5 user interfaces that adapt to the screen size of any device they use, whether a tablet or a smartphone, and the reduction in effort to get to their clinical applications, while patients are pleased that less time is consumed by administrative tasks during their scheduled visits.
EmpowerID’s multi-factor authentication capability (using an OATH token and SMS one time password) was implemented to strengthen system access security and to better protect the privacy of patient data, which is important in meeting regulatory and audit requirements.
EmpowerID also assists the organization’s auditors with data governance – the discipline of ensuring that access to corporate and patient data is secure and is subject to the proper controls. EmpowerID not only improves the quality of data, is also supports configurable Separation of Duties (SOD) policies, attestation procedures and system dashboards for quick visibility of pending tasks and system statistics. EmpowerID provides dozens of reports out of the box and it supports Microsoft’s SQL Reporting Services to quickly provide the information that different users need.
As a result of successfully automating their new user provisioning process and providing a seamless single-sign on experience for its home healthcare staff, this organization is realizing substantial productivity savings that will pay for EmpowerID in a period of just eighteen to twenty-four months.
The CSO’s vision for a single, flexible platform that could be implemented on-time and within budget to automate and to securely manage multiple aspects of the enterprise, creating new efficiencies and cost-savings, has been fully realized with EmpowerID's deployment.
Ranked by KuppingerCole as a Product Leader, Innovation Leader and Overall Leader in their recent Leadership Compass for Identity Provisioning, EmpowerID helps diverse organizations across the globe improve identity security and access governance, increase productivity, lower costs, and improve service delivery through its innovative and cost-effective approach to IAM.

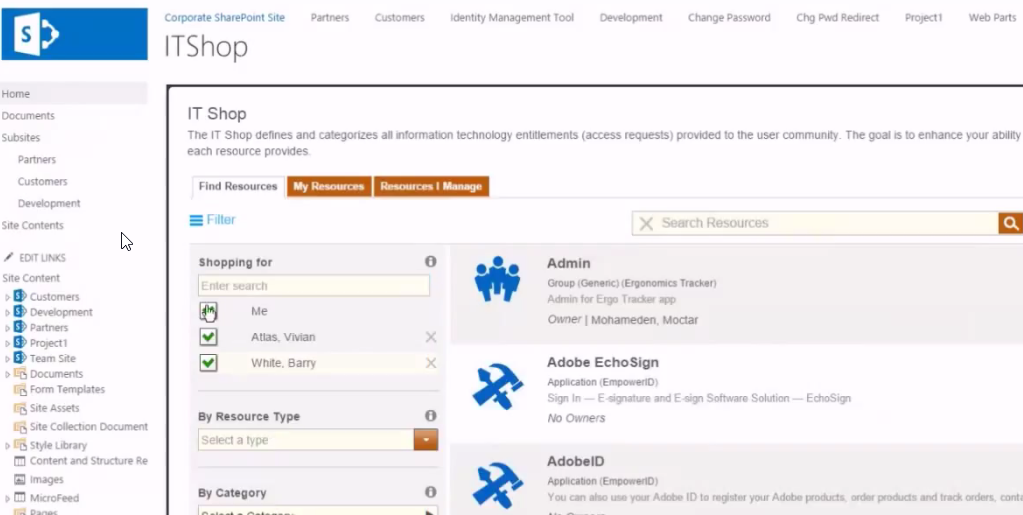





 We have a very large home healthcare client with a very common problem: most of their employees are on the road needing access to corporate and cloud applications using a tablet. These users have numerous critical applications they need to access for medical history, prescriptions, scheduling and all of the traditional cloud applications. If they couldn't authenticate and log on, they certainly could not call the helpdesk while sitting with their patients.
We have a very large home healthcare client with a very common problem: most of their employees are on the road needing access to corporate and cloud applications using a tablet. These users have numerous critical applications they need to access for medical history, prescriptions, scheduling and all of the traditional cloud applications. If they couldn't authenticate and log on, they certainly could not call the helpdesk while sitting with their patients.

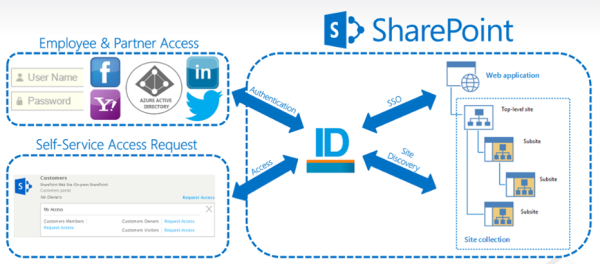
 Of those, 16 web and cloud applications, probably half of them support federation, usually SAML or OAuth. Note: EmpowerID supports SAML, OAuth, OpenID, WS-Trust, and WS-Federation. You can federate with those applications, knowing that it trusts that you know who you users are. Your
Of those, 16 web and cloud applications, probably half of them support federation, usually SAML or OAuth. Note: EmpowerID supports SAML, OAuth, OpenID, WS-Trust, and WS-Federation. You can federate with those applications, knowing that it trusts that you know who you users are. Your 
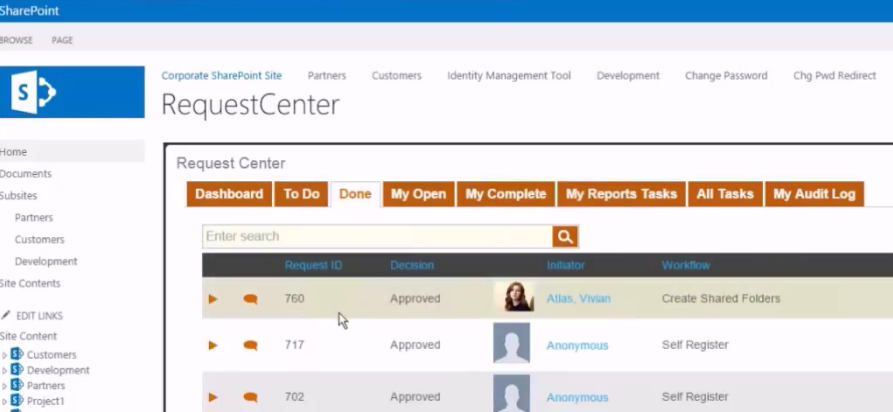
 The first two Identity Management hurdles you have to overcome are provisioning and Single Sign-on. Without proper IdM planning you could very easily end up back in the dark ages of manual provisioning for your cloud applications.
The first two Identity Management hurdles you have to overcome are provisioning and Single Sign-on. Without proper IdM planning you could very easily end up back in the dark ages of manual provisioning for your cloud applications. When SSO projects come our way, the initial conversations are always around SAML federation, Web Access Management (WAM), or password vaulting. We talk about identity providers, service providers, SharePoint claims, and multi-factor authentication. Customers talk about their applications and user experience in SSO. What they don't bring up is how to manage those external users because other SSO vendors avoid that conversation like the plague.
When SSO projects come our way, the initial conversations are always around SAML federation, Web Access Management (WAM), or password vaulting. We talk about identity providers, service providers, SharePoint claims, and multi-factor authentication. Customers talk about their applications and user experience in SSO. What they don't bring up is how to manage those external users because other SSO vendors avoid that conversation like the plague.
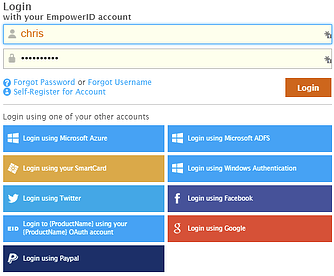
 Single sign-on does not have a magic bullet; instead, it requires a swiss army knife. Meaning many different ways to get users authenticated into an application using only one set of credentials. A German partner of ours calls this
Single sign-on does not have a magic bullet; instead, it requires a swiss army knife. Meaning many different ways to get users authenticated into an application using only one set of credentials. A German partner of ours calls this  The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.
The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.