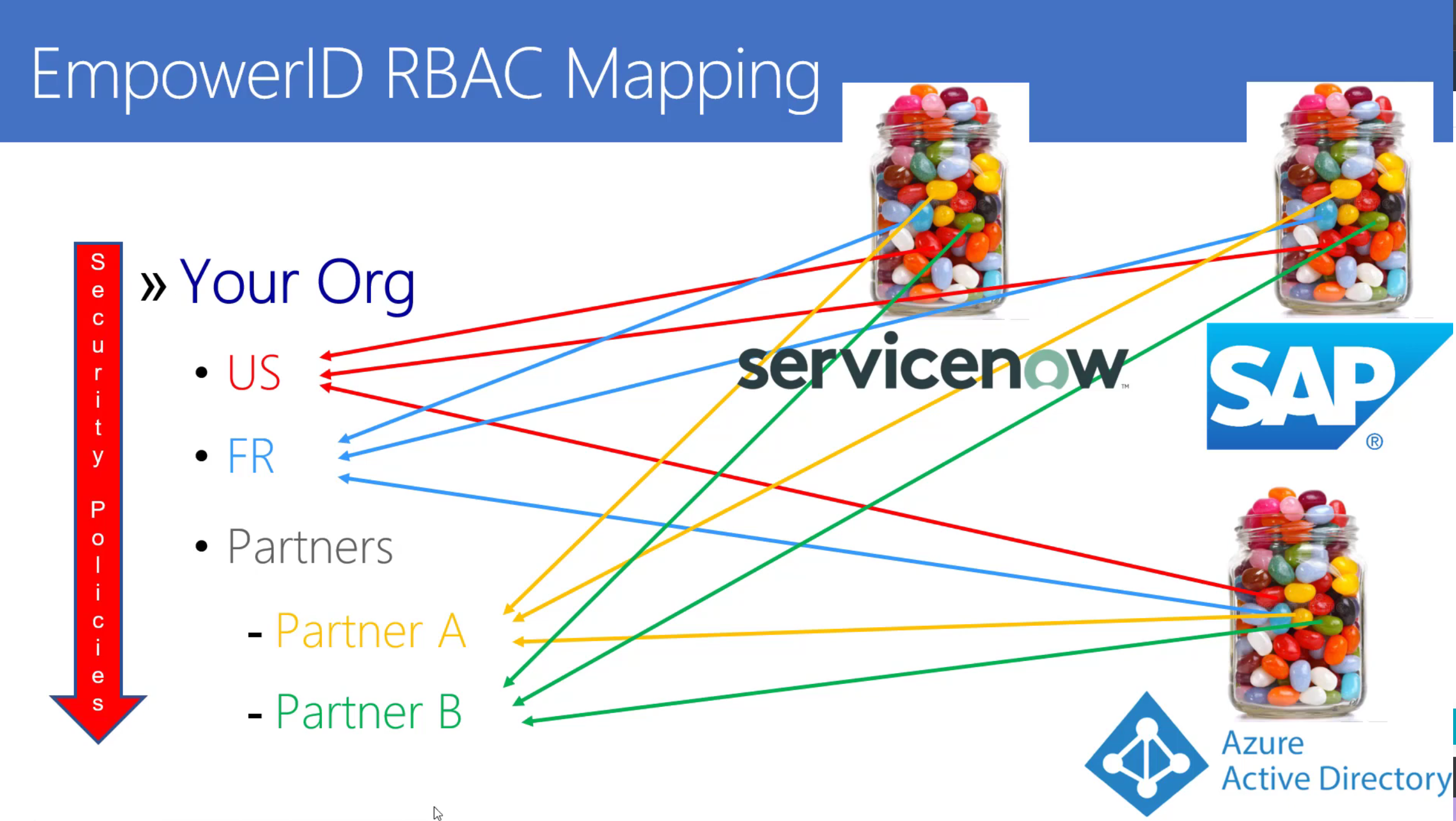
ServiceNow is a powerful platform for IT service management (ITSM) and enterprise service management (ESM), helping organizations streamline their business processes, automate workflows, and provide efficient services to employees and customers. But what if you could take your ServiceNow experience to the next level by integrating it with Identity and Access Management (IAM) capabilities?
For ServiceNow experts seeking to enhance their service management capabilities while addressing the complexities of Identity and Access Management (IAM), the integration of EmpowerID with ServiceNow offers a powerful best-of-breed solution, bridging the gap between IAM and service management. Let's delve into the key aspects of how EmpowerID enhances your ServiceNow experience.
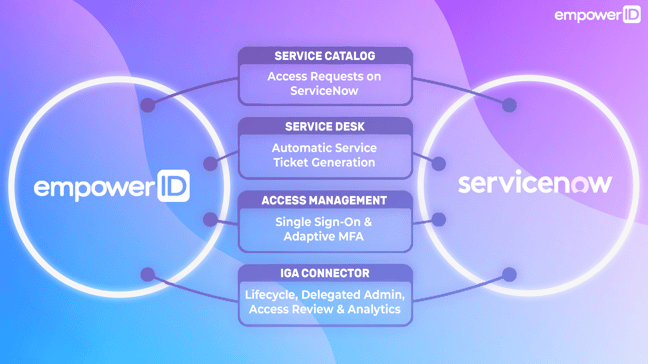
Identity Lifecycle for ServiceNow
The EmpowerID Identity Lifecycle for ServiceNow automates account provisioning and access assignments, making it a game-changer for organizations. By implementing policy-based "Compliant Access," one can effectively eliminate security challenges and human errors commonly associated with manual user creation and access assignment within ServiceNow.
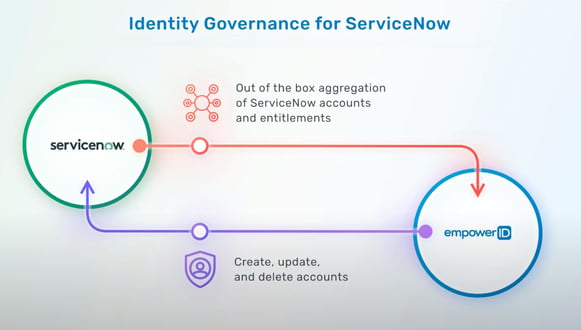
One significant advantage is the ability to detect changes originating from your HR system, which trigger manual lifecycle events. EmpowerID can efficiently handles these changes, automating the provisioning and deprovisioning of user accounts across various environments and tenants. During the deprovisioning process, it ensures a graceful handover of responsibilities and the transfer of data ownership, all in adherence to your pre-defined business policies.
ServiceCatalog and ServiceDesk Enhancements
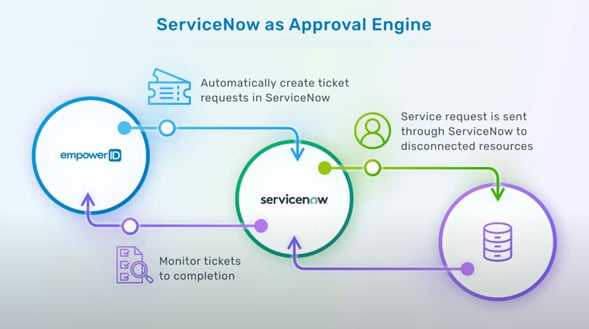
EmpowerID’s integration with the ServiceNow service desk allows the identity management tasks and self-service actions performed or initiated within EmpowerID to be integrated with the ServiceNow ticket tracking system. This ensures that all requests have a ticket in ServiceNow. Approvals can optionally be performed in ServiceNow, but the actions that happen in EmpowerID keep you updated, ensuring that you never lose visibility of what's happening in your EmpowerID system. Tickets reflect all those changes within ServiceNow.
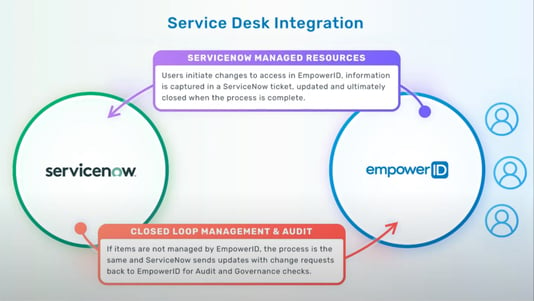
Integrating with the ServiceCatalog further allows access requests initiated from within the ServiceNow interface to be fulfilled by EmpowerID. EmpowerID has numerous IT connectors, extending the reach of ServiceNow requests to allow them to be fully automated with fulfillment.
Zero Trust Delegated Administration for ServiceNow
The concept of Zero Trust is a cornerstone of modern security strategies. However, out-of-the-box, ServiceNow's security model do not align with the principles of Zero Trust, as it involves granting users permanent unproxied access to systems. Permanent privileged access is challenging to monitor and may expose organizations to security risks.
This is where EmpowerID's unique approach shines. EmpowerID overlays a unified security model on top of native applications or systems, such as ServiceNow. This overlay effectively integrates EmpowerID's granular security model with the native system, allowing for fine-grained delegated administrative privileges. In essence, EmpowerID transforms ServiceNow into a Zero Trust-capable system.
With EmpowerID, granular administrative control can be delegated to users within specific business units or partner organizations. This level of fine-grained delegation supports even the most complex global organizations and multitenancy scenarios, all without the need to grant native administrative privileges.
ServiceNow Compliance and Recertification
EmpowerID brings granularity, control, and functionality to ServiceNow, simplifying the audit process and compliance management. Auditing ServiceNow environments can be challenging, particularly in proving who has access to specific applications and roles.
EmpowerID solves this by maintaining an up-to-date audit and providing complete control over access across all your ServiceNow tenants. This transparency streamlines the certification process and almost automatically produces the necessary proof for audits.
EmpowerID also includes built-in attestation policies that allow for rapid periodic recertification of ServiceNow group and role assignments, eliminating the hassle of auditing this critical infrastructure. The categorization of external users and risk-based Separation of Duties policies further enhance the compliance and governance capabilities within ServiceNow.
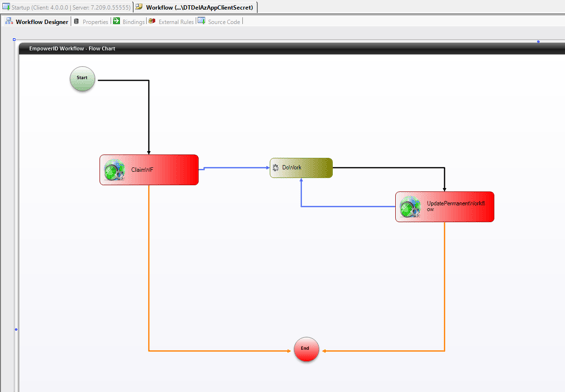
Orchestration Pack – Entitlement Sync and Workflows
The Orchestration Pack for ServiceNow empowers process designers to leverage EmpowerID capabilities within their ServiceNow business processes. This pack introduces workflow activities, web services, and example workflows, offering unparalleled flexibility.
For example, it includes a job that synchronizes and maintains an up-to-date list of requestable groups and roles from the EmpowerID Identity Warehouse to custom tables in your ServiceNow tenants. These workflow activities permit users to request access to entitlements in any EmpowerID-connected system directly from the ServiceNow Service Catalog.
Notably, example workflows are fully customizable, with no restrictions on modifications. This flexibility allows ServiceNow process designers to incorporate these workflows into existing and future workflows, tailoring them to specific organizational needs.
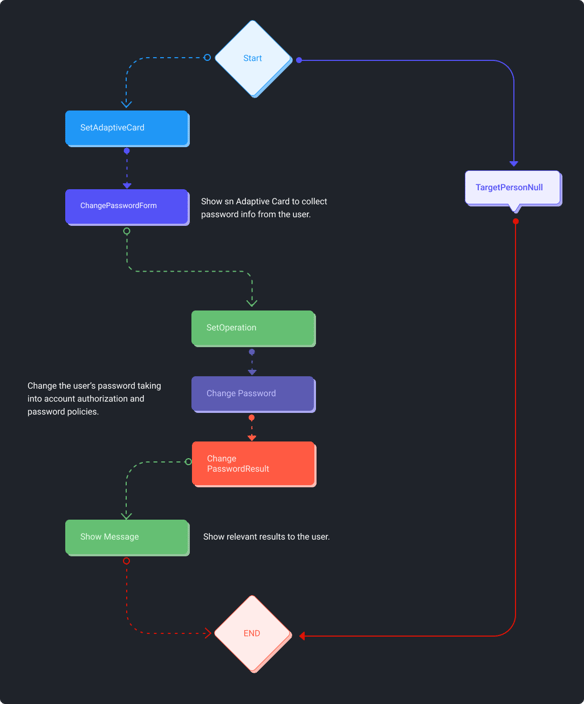
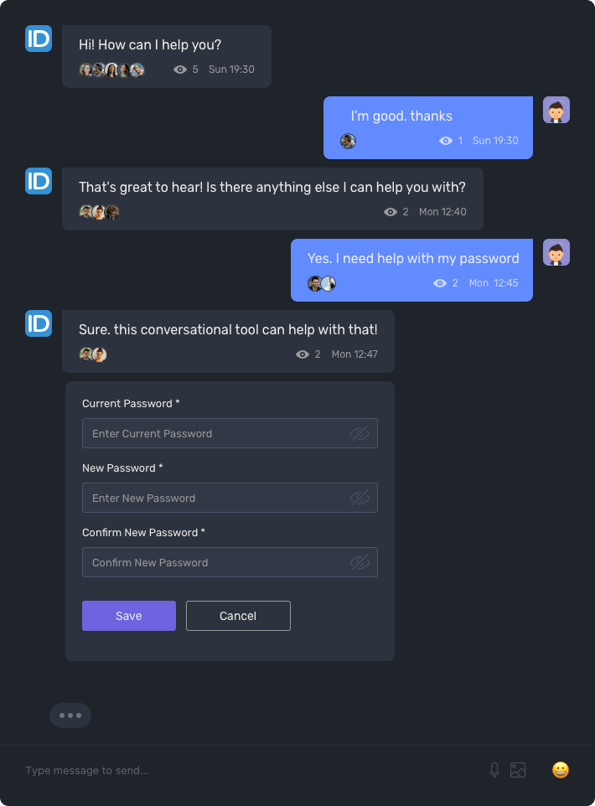
AI-Powered Chat Bot Virtual Assistant
EmpowerID's AI-powered chat bot virtual assistant empowers users to perform self-service automation across various routine tasks, including password resets and unlocks. The chat bot offers users the convenience of self-service automation through their preferred communication channels, such as SMS, Teams, web, mobile, and the ServiceNow portal.
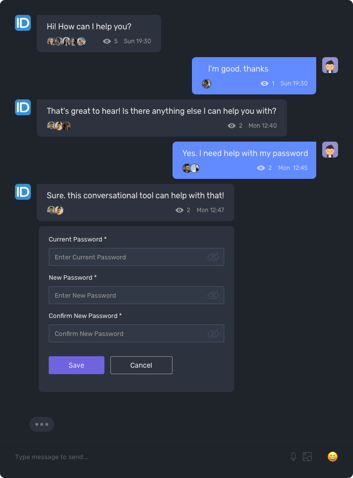
Behind the scenes, the chat bot interacts with EmpowerID's visually designed workflows to securely automate Identity Governance and Administration (IGA) processes that interact with both Cloud and on-premise applications and systems. Users can perform tasks like password resets, application and group access requests, SAP role access requests, privileged credential management, mobile login to SSO applications, and more, streamlining routine tasks and improving user productivity.
Key Capabilities of EmpowerID in the ServiceNow Environment
- Single Sign-On (SSO): EmpowerID enables seamless SSO for ServiceNow, streamlining user access with one set of credentials and enhancing security.
- User Provisioning and Deprovisioning: EmpowerID automates user onboarding and offboarding, reducing administrative overhead during employee transitions.
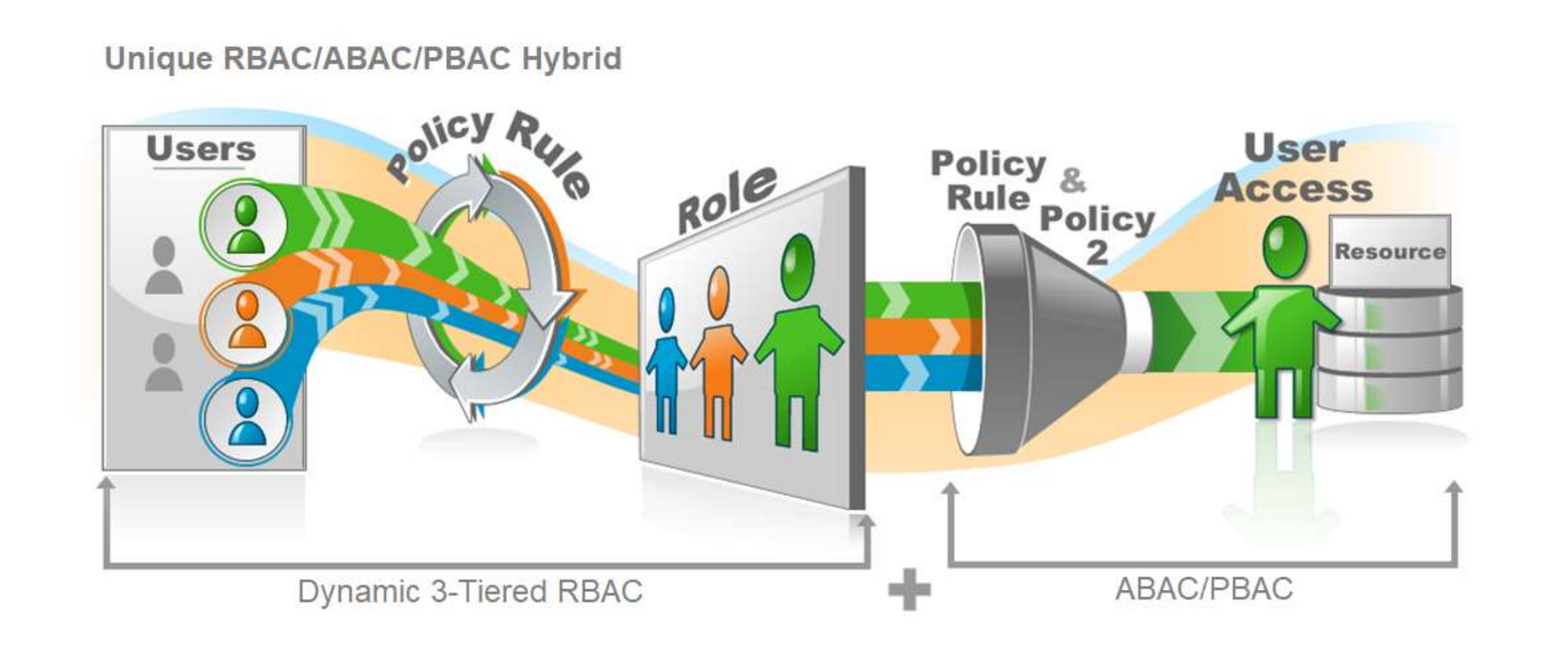
- Role-Based Access Control (RBAC): EmpowerID extends granular RBAC policies to ServiceNow, ensuring users have appropriate access based on their job roles.
- Self-Service Capabilities: EmpowerID empowers users with self-service features for actions like password resets and profile updates, reducing IT support tickets.
- Governance and Compliance: EmpowerID offers access certification and compliance management, ensuring ServiceNow aligns with regulatory standards and internal policies.
- Workflow Orchestration: EmpowerID's workflow engine streamlines service requests, approvals, and other processes within ServiceNow.
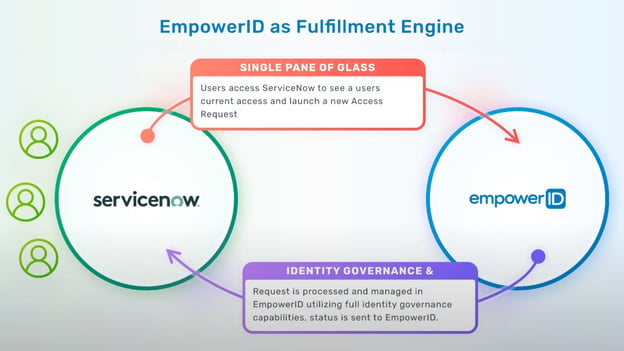
Enhancing IT Service Management with EmpowerID
- Efficient User Onboarding: EmpowerID's user provisioning allows new employees to access ServiceNow immediately, improving IT issue resolution.
- Service Desk Productivity: Self-service options reduce service desk tickets, enhancing productivity and allowing teams to focus on complex tasks.
- Automated Access Requests: Streamlined access request workflows enable users to request specific ServiceNow functionalities, which are automatically approved and provisioned.
Strengthening Identity and Access Management with ServiceNow
- Unified Identity Management: EmpowerID centralizes user identities within the broader IAM strategy, encompassing the entire enterprise.
- Access Governance: EmpowerID's access certification and audit capabilities apply to ServiceNow, certifying access to functions and data, bolstering security and compliance.
Conclusion
In conclusion, the EmpowerID and ServiceNow integration delivers a comprehensive solution that seamlessly combines the capabilities of IAM with service management. This integration enhances identity lifecycle management, provides Zero Trust delegated administration, simplifies compliance and recertification, and offers flexible orchestration and automation through AI-powered chat bot virtual assistants. It's a powerful tool for ServiceNow experts looking to maximize the potential of their service management platform while addressing IAM challenges.

.png?width=734&height=317&name=MicrosoftTeams-image%20(29).png)