In our previous article, we covered the benefits and drawbacks of different authorization models, namely:
- Role-Based Access Control (RBAC)
- Attribute-Based Access Control (ABAC)
- Policy-Based Access Control (PBAC)
We summarized that each of them had its unique characteristics. However, for organizations aiming to scale and manage thousands of users, no single method covers all use cases and application technologies. This is because certain types of applications and use cases are better suited for a structured role-based approach, while others require real-time contextual decisions.
While there are overlapping qualities among these models, individually, none of them can address all the necessary aspects of access control. To meet the needs of these organizations, a combination of the benefits from all these authorization models is required to fully ensure the security requirements of enterprises from every possible angle.
This is where the need for a hybrid authorization model arises. With all these considerations, we at EmpowerID embarked on a journey to create a perfect authorization recipe – one that encompassed all aspects of authorization without the drawbacks associated with each model. The result of this endeavor is a unique hybrid approach that combines role and attribute compliance, which we aptly named "Compliant Access Delivery."
The overall goal of Compliant Access Delivery required using the best of each approach implemented following the principles of Zero Trust and Least Privilege. Based on RBAC relational modeling, it provides the backbone or
structure for defining an organization and its overall policies while leveraging the flexibility and real-time contextual nature of ABAC and PBAC to offer the most comprehensive access control solution.
Compliant Access Delivery
“Compliant Access Delivery” is, first, the capability to map out in advance the position appropriate access for employees, partners, and customers and the risk policies that will measure and ensure continued compliance and to then monitor and enforce this compliant state through automation.
.png?width=734&height=317&name=MicrosoftTeams-image%20(29).png)
The natural follow-up question to this is “What makes access compliant?” Compliant access is appropriate to the person to whom it is assigned in accordance with the organizational standards and business policies to minimize risk. Compliant Access Delivery synthesizes multiple Identity and Access Management (IAM) technologies with a business modeling approach to automate and maintain each user's appropriate access to IT systems while continuously minimizing risk.
![]()
Compliant Access is a well-defined target state against which the current state can be
measured.
![]()
The key to Compliant Access are the words “appropriate” and compliant with “business policies.” With Compliant Access, the devil is in the details, and that is where traditional solutions miss the mark. Due to its distinct language, processes, and policies, Compliant Access cannot be delivered by an IAM system that doesn't bridge the divide between the technical system and the business. With its operating procedures, industry norms, and regulatory restrictions, the business defines which jobs are appropriate, what constitutes a risk, and what is considered non-compliant. To achieve this, EmpowerID leverages both the organization’s business model and its language to enforce and provision Compliant Access across Cloud and on-premises systems.
How Does Compliant Access Leverage Your Business Model?
Defining business-appropriate access is a challenge for IT organizations using their existing IAM systems. These systems were designed to manage only the technical aspects of access control and universally lack a conceptual “bridge” to tie the technical entitlements to the business’s operating model and the activities or “Functions” performed by its participants.
Everything we cover in this blog can be explored further in our whitepaper “A Guide to Authorization”. You can find that whitepaper here:
Business Processes and Functions
Businesses are composed of processes for producing and delivering goods or services. These processes involve tasks performed by internal and external participants. Each task can be divided into functions needed for its completion. For instance, creating a purchase order is a function within a purchasing process. While a purchase order is recognizable and its creation straightforward, not all employees should have this ability. During access reviews, managers can easily identify authorized users. This simplicity contrasts with technical entitlements that grant system access, often named confusingly. Functions bridge the gap between technical access and business understanding, ensuring a clear separation between business and IT.
Risk Policies
Compliant Access must be "appropriate" and align with an organization's "business policies." These policies are specific to the organization and cater to its operations, industry, processes, and regulations. Notably, these policies are distinct from the organization's IT systems. For example, the customer acquisition process's risks remain consistent across different Customer Relationship Managers (CRMs) like SalesForce.com or HubSpot. Users' end-to-end functions can be defined before any IT system interaction. Identifying higher-risk functions and potential fraud combinations empowers threat mitigation. Crucially, establishing risk policies at the function level ensures core business activities are monitored effectively. Business users often face confusion when risk policies are tied to technical entitlements instead of familiar business concepts, hindering visibility into actual actions.
Bridging the Gap between Business and Technology
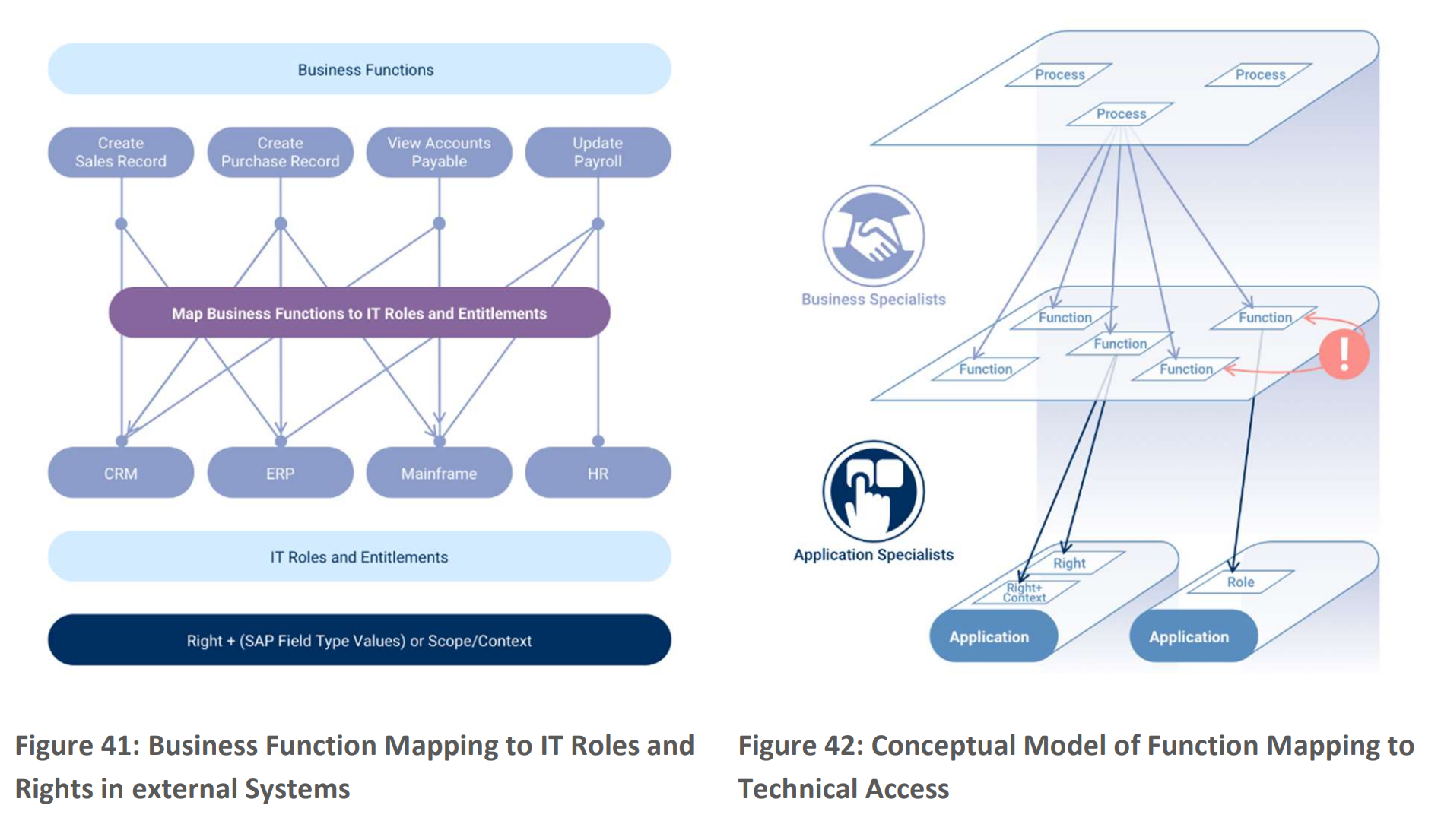
To align business-appropriate access and risk policies, focusing on functions is crucial. This requires bridging them to IT systems, where business specialists play a key role. They map out business processes, activities, and roles involved (Figure 41). Collaborating with IT experts, they convert functions into task-based application roles within specific systems (Figure 42). EmpowerID supports mapping roles to functions and even mapping fine-grained permissions to functions. This clarifies which IT entitlements enable functions, who can perform them, and how access is assigned. Functions enhance business clarity in your IT landscape.
![]()
Sign up for our Newsletter!
![]()
Learn How CAD can evolve your Authorization Model
Tags: Active Directory, IAM, Virtual Directory, Access Governance, cloud security