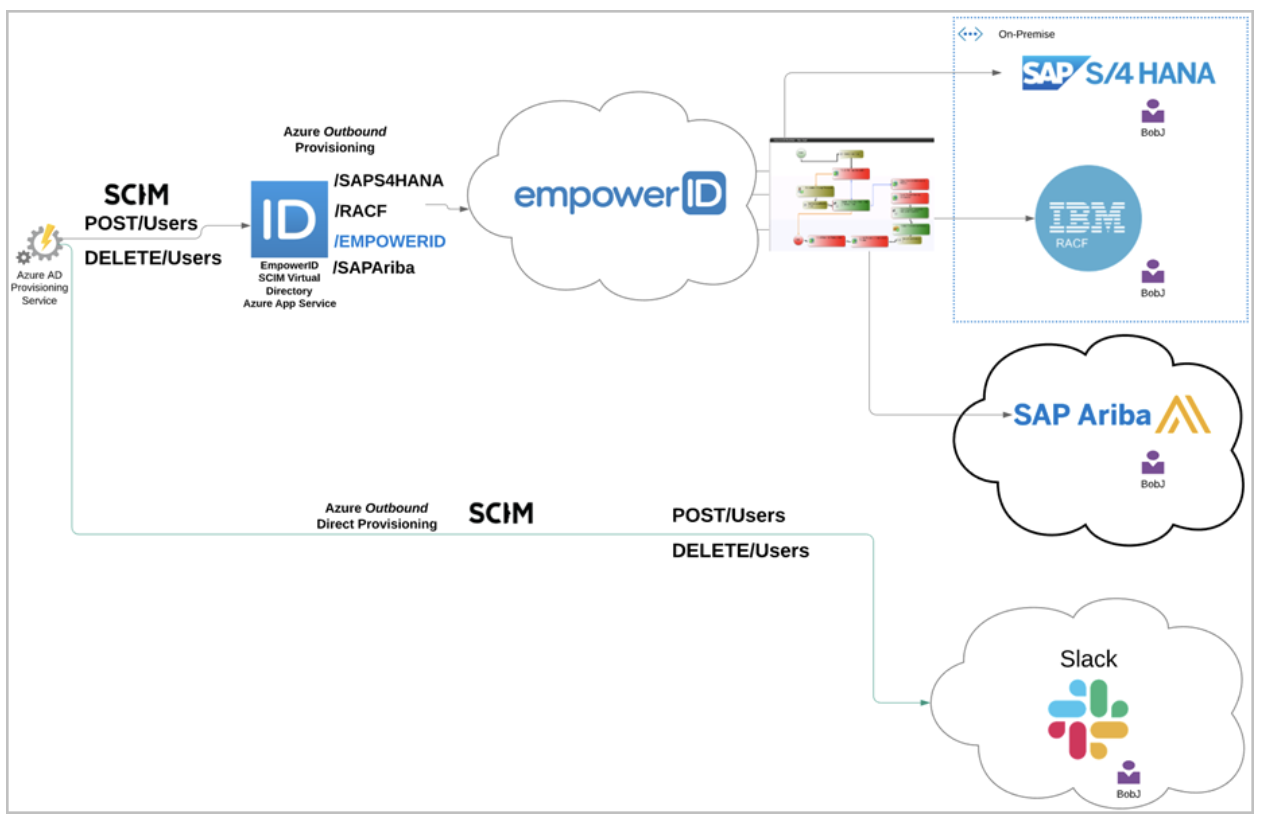
With the advancements in AI and Cybersecurity, modern organizations are seeking innovative ways to harness the efficiency and security gains unlocked by these developments. Agentic Workflows represent a groundbreaking approach to automation, enabling systems to adapt dynamically and make intelligent decisions with minimal human intervention.
What is an Agentic Workflow?
An Agentic Workflow is a system where autonomous agents execute tasks, make decisions, and manage complex processes independently or with minimal human intervention. Unlike traditional workflows that follow a predetermined sequence of steps, agentic workflows are dynamic and adaptable, capable of adjusting their behavior based on real-time data and contextual information. By integrating AI and LLMs, these workflows gain the ability to understand, reason, and interact in ways that traditional automation cannot.
Key Characteristics:
- Autonomy: Agents operate independently, reducing the need for manual oversight.
- Adaptability: Workflows adjust dynamically to changing conditions and inputs.
- Intelligence: Integration with Artificial Intelligence (AI) and Machine Learning (ML) enables advanced decision-making.
- Interactivity: Agents can interact with users, external systems, and other agents to achieve complex objectives.
How Do Agentic Workflows Work?
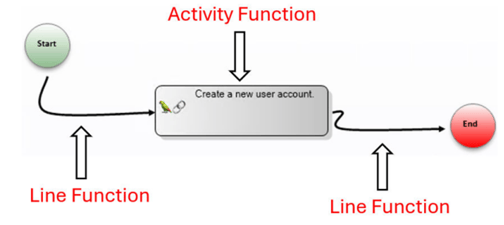
The workflow consists of distinct predefined activities, line functions that connect these activities, and transitions that manage the flow of operations. The purpose of an Agentic Workflow is to streamline complex processes where agents can independently perform tasks, make decisions, and respond to different conditions in real-time, with or without human intervention.
- Activities: Discrete units of work or tasks that the agent performs. Each activity encapsulates specific functionality, such as processing data, interacting with an API, or making decisions with the help of an LLM.
- Line Functions: Define the logic that governs transitions between activities. They determine the conditions under which the workflow should move from one activity to another. For instance, a line function might evaluate data from the previous activity and decide whether to proceed to the next activity.
- Transitions: Manage the flow between activities, dictating how the workflow progresses based on outcomes or conditions evaluated during execution.
Applications in Identity and Access Management (IAM)
In IAM, agentic workflows can automate complex processes such as user provisioning, role assignments, and access control. Agents can make real-time decisions based on user behavior, context, and predefined policies, enhancing security and efficiency.
- Automated User Provisioning: Streamlining the creation and management of user accounts.
- Dynamic Role Assignment: Assigning roles based on contextual data such as user behavior, location, or risk assessments.
- Adaptive Authentication: Adjusting authentication requirements in real-time based on threat levels or anomalous activities.
- Policy Enforcement: Ensuring compliance with security policies across various systems and platforms.
Example: Automating User Provisioning with Agentic Workflows
Let's delve deeper into an example within the Identity and Access Management domain—Automated User Provisioning.
Scenario
A new employee joins the organization, and you need to set up their accounts, assign appropriate roles, and grant access to necessary applications. Traditionally, this process involves multiple manual steps and coordination between HR and IT departments.
Agentic Workflow Solution
An agentic workflow can automate this entire process:
- Trigger: The workflow is initiated when HR adds a new employee record to the system.
- Activity 1 - Gather User Information:
- The agent retrieves the employee's details, such as name, department, job title, and location.
- Activity 2 - Decide on Role Assignment:
- A line function evaluates the user's department and job title to determine the appropriate roles.
- For example, if the employee is in the Sales department, they might need access to CRM systems.
- Activity 3 - Create User Accounts:
- The agent creates user accounts in necessary systems (e.g., EntraID, email services).
- Activity 4 - Assign Access Rights:
- The agent assigns permissions and access rights based on the roles determined earlier.
- Activity 5 - Notify Stakeholders:
- The agent sends notifications to the employee with their account details and to the manager confirming completion.
Advantages of Agentic Workflows
- Real-Time Decision Making: Agents can evaluate conditions and make decisions on-the-fly, enabling workflows to adapt instantly to new information.
- Scalability: Easily handles increased workload without significant changes to the underlying infrastructure.
- Integration Capabilities: Agents can interact with various systems and APIs, facilitating seamless integration across platforms.
- Reduced Operational Costs: Automation reduces the need for manual intervention, lowering labor costs and minimizing errors.
Role of AI and LLMs in Agentic Workflows
EmpowerID's Agentic Workflow Service (AWF) integrates Artificial Intelligence (AI) and Large Language Models (LLMs) to enhance the automation and intelligence of identity and access management workflows. By leveraging AI and LLMs, AWF enables autonomous agents to perform complex tasks, make informed decisions, and adapt to real-time conditions with minimal human intervention.
- Intelligent Decision-Making
AI algorithms within AWF empower agents to analyze data, recognize patterns, and make decisions based on predefined criteria and learned experiences. Machine learning models allow agents to assess risks, predict outcomes, and optimize processes by learning from historical data and adapting to new information.
- Natural Language Processing (NLP)
LLMs like GPT-4 enhance AWF by providing advanced natural language understanding and generation capabilities. Agents can interpret user inputs expressed in natural language, process unstructured data, and generate coherent and contextually appropriate responses. This enables more intuitive interactions between users and the system.
- Contextual Understanding and Adaptation
AI and LLMs enable AWF agents to comprehend the context of interactions, considering factors such as user behavior, environmental variables, and historical data. This allows workflows to adjust dynamically, responding to changing conditions and inputs to provide appropriate outcomes.
Conclusion
Agentic Workflows have the potential to transform Identity and Access Management by introducing automation that is both intelligent and adaptable. By leveraging this approach, organizations can enhance security, ensure compliance, and significantly reduce the manual workload on IT departments.
Embracing agentic workflows in IAM is a strategic move toward a more secure and efficient future, where systems are not just automated but also capable of making context-aware decisions that align with organizational policies and objectives.
Tags: Agentic Workflow, IAM, Identity Management, Automation, Cybersecurity