In today's "work from anywhere" model, cloud-based identity management solutions are quickly becoming the norm. To enable interoperable cloud provisioning, Microsoft has embraced the System for Cross Domain Identity Management (SCIM) protocol in Azure. SCIM was created as a powerful means of standardizing, simplifying, and automating identity management for users, groups, and devices across cloud-based applications and services, and Microsoft is betting big on it.
The challenge with SCIM is that it has yet to become widely adopted, and many applications simply do not support it. If you have custom applications with repositories of identity information or use an on-premise or cloud application like SAP S/4 HANA or SAP Ariba, or even a major HR system like UltiPro, you will not be able to integrate those systems with Azure unless you or the vendor builds a SCIM interface for each. This is no small task because, while the protocol is simple, building the interface is not.
EmpowerID stepped into the gap and designed a Workflow-Driven SCIM Virtual Directory Server (VDS) that can sit between Azure and your non-SCIM applications. You simply connect those applications to EmpowerID and register the EmpowerID SCIM VDS in Azure. There is no need to wait for vendors or put in the time and effort needed to build a SCIM interface; EmpowerID takes care of everything for you.
Authentication Challenges: Unraveling the Complexity
-
Diverse Directory Systems: Organizations often deploy their directory systems, each with its set of permissions and administration controls. However, these systems fail to provide the granular level of access required, turning into additional entities for IT systems to manage.
-
Privilege Abuse and Security Risks: The adoption of multiple directory systems increases the surface area of attacks through privilege abuse. Without comprehensive controls, organizations face heightened security risks, leaving their systems vulnerable to exploitation.
-
Slow Adoption of SCIM: Despite the promise of standardization and simplification, the System for Cross Domain Identity Management (SCIM) has experienced slow adoption. Many applications lack support for SCIM, leaving organizations unable to leverage its benefits fully.
Why SCIM?
Enjoy all the Advantages of SCIM without the Effort – Created in 2011 as an open standard, lightweight provisioning protocol for the "Cloud age," SCIM provides a uniform way for applications to communicate identity information with each other. Although the adoption of SCIM has been slow, it is the way forward. With EmpowerID’s SCIM VDS, organizations can convert their applications to SCIM without waiting for vendors to come onboard or doing the heavy lifting of converting their legacy proprietary applications to SCIM.
Seamlessly Integrate All Your Applications with Azure Provisioning Services – The EmpowerID SCIM Virtual Directory is a microservice and a SCIM server that can be deployed as an App Service in any Azure tenant. Simply plug the VDS into any Azure environment, secure it with an Azure managed identity, and then register as many of your enterprise applications as needed. If the VDS knows about these applications, it will pass Azure provisioning commands to that system, SCIM compliant or not.
Workflow-Driven Virtual Directory Services – More than just a "SCIM gateway," which is more than just an application that simply passes identity lifecycle commands like "provision this user" or "add this user to that group" from one system to another, the EmpowerID VDS treats everything as a workflow. This keeps your business logic in the process. Commands are evaluated by the VDS, which can trigger policies, invoke naming conventions, generate strong passwords, and send policy violations for human approval before any final provisioning action occurs. You determine what needs to happen when Azure makes a provisioning call.
HOW DOES THIS WORK?
The SCIM Virtual Directory is a microservice and a SCIM server created by EmpowerID that can be deployed as an App Service in Azure tenants. This makes the SCIM VDS the intermediary between Azure and any applications registered in EmpowerID. Provisioning calls are made to the EmpowerID SCIM VDS, and the call is then directed to the appropriate system.
For example, if you have connected EmpowerID to Salesforce and an HR system, and a new user is provisioned in Azure AD, EmpowerID intercepts the call to provision the new user and directs it to the appropriate systems in EmpowerID.
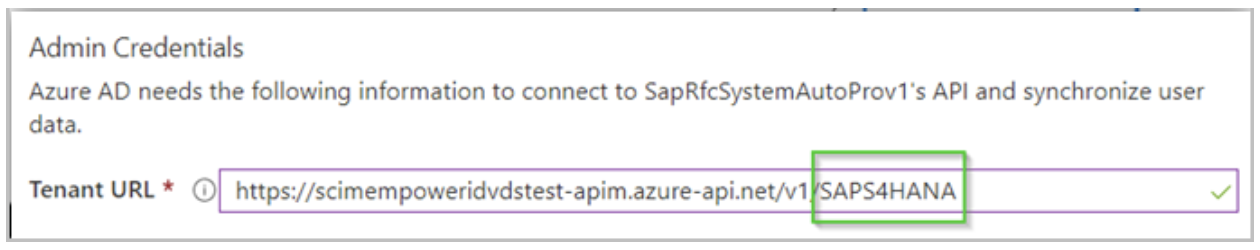
This allows for any policies and other business logic to be evaluated first. Once your business logic completes, the account is provisioned in the appropriate systems, and everything is kept up to sync. The natural question arises as to how EmpowerID knows what system to update. The answer to the question is the URL you set for your applications in EmpowerID. Without going into detail, you simply specify the path to the application registered in EmpowerID. The image below depicts this.
The last part of the path points to the application in the image. This is how EmpowerID knows where to direct the call made by Azure.
This allows you to SCIM-enable any system connected to EmpowerID without needing to create a specific SCIM connector for that system. EmpowerID does it for you, helping you leverage Azure AD provisioning quickly and easily for many systems with some advanced features.
WORKFLOW-DRIVEN VIRTUAL DIRECTORY SERVICES
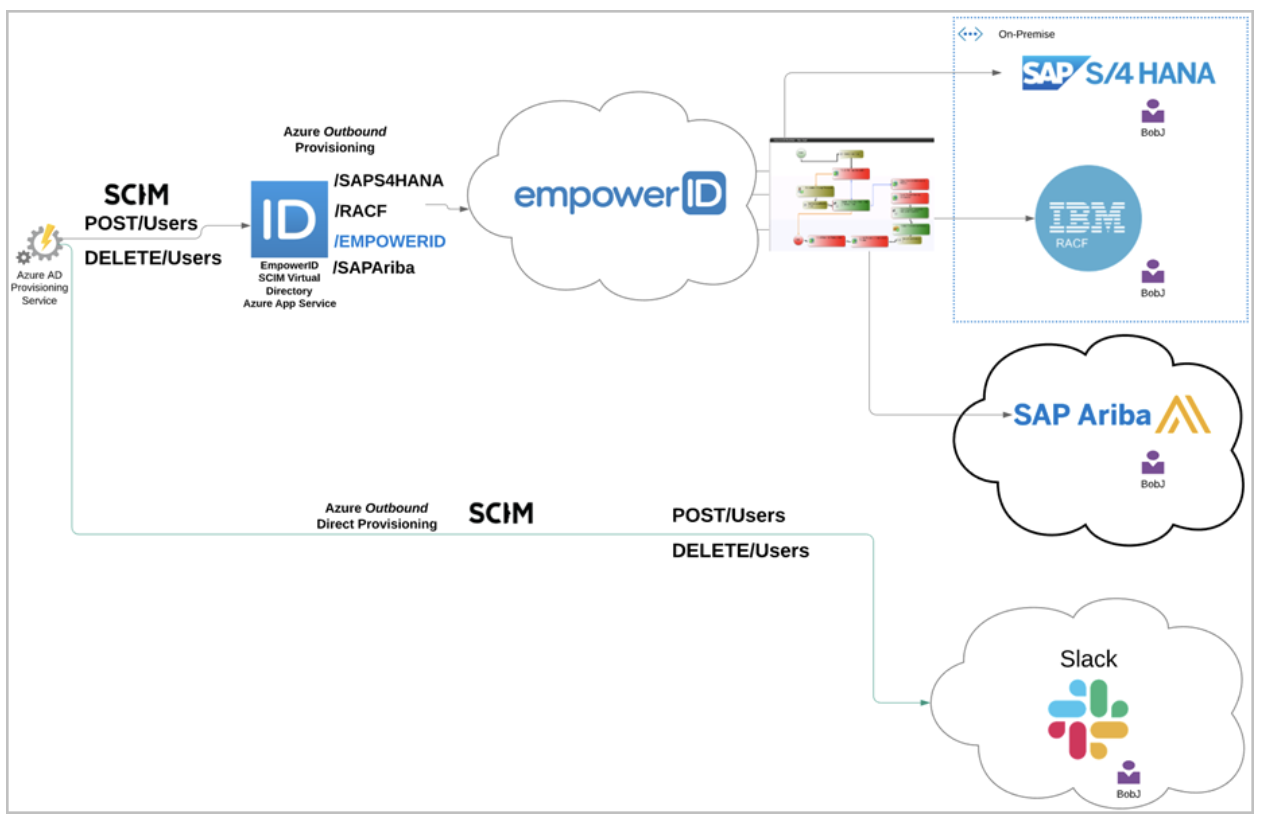
Traditional SCIM connectors operate on a "fire and forget" principle. They simply pass commands from one system to another without any intermediate layer of logic. In essence, they function more as a SCIM gateway. The EmpowerID SCIM VDS, on the other hand, takes a different approach. It not only passes commands from one system to another but also evaluates your business processes in the process.
We refer to this approach as "everything is a workflow," and it is at the core of the EmpowerID paradigm. Organizations need to inject their business logic into the process to maintain complete control.
The image above illustrates the difference between the two approaches. In the first flow, Azure AD Provisioning Service sends commands to the EmpowerID SCIM VDS. EmpowerID then invokes the appropriate workflow for the command, allowing business processes to be executed before forwarding those commands downstream to a connected system. In the second, lower flow, Azure sends the same commands directly to a connected system, where they simply occur in that system with no control over the transactions. With EmpowerID acting as an intermediary, the entire process can be evaluated and interrupted if necessary.