Life would be a lot easier if we only had to manage our employees' identities. But we have customers, partners, and contractors. These external identities have the same needs for identity management as our internal identities. In fact, they might have more needs as we know a lot less about them.
 The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.
The most common scenario that we see is when a customer (the external user) registers for services with our client. The needs are very simple: self-registration, role based access control, approval workflows, and federated single sign-on (SSO). I'm kidding, that's not simple.
Let's start with the self-registration. When your external user first finds your site, you will want their registration to be simple, giving them immediate access to the most public facing resources. EmpowerID's built in forms designer allows you to have them fill out the important information and create an account in the metadirectory.
The RBAC engine will give them the most basic of permissions at the same time that it either kicks off an approval workflow to grant more permissions or inventories another identity store (CRM for example) to determine their role and give higher privileges.
So, now you know who they are and can design some provisioning rules for other applications. With the roles in place, you know that customers that meet certain criteria get access to different applications and resources. Role based provisioning will automatically create accounts in these applications.
Permissions are managed with these roles too. Polyarchical roles allow you to protect resources at a very granular level without having to create a role for every single type of external user.
Now we get to the heart of the matter, you know who your external users are, what their roles are and what access you give each role. Now your users need to access these resources and applications.
Enter single sign-on (SSO). You have provisioned a user account in the EmpowerID metadirectory. This metadirectory can act as an identity provider or service provider, meaning that you can authenticate with EmpowerID and federate out to other applications or you can authenticate with other credentials, federate with EmpowerID and then with your other applications.
EmpowerID as an identity provider is incredibly powerful, it is also a Secure Token Service, allowing it to send tokens to the federated applications and giving users immediate access based on their role. EmpowerID supports federation with SAML, OpenID, OAuth, WS-Trust and WS-Federation.
For applications that aren't federated, EmpowerID can also perform Web Access Management (WAM), sending user credentials securely and giving the same end user experience.
On the flip side, you can also federate with other identity providers such as Facebook or Twitter, giving users the ability to authenticate with credentials they use every day. EmpowerID is still in the middle and provides role based access to the connected applications.
EmpowerID is one of the only IAM solutions on the market that manages external users' provisioning, authentication and authorization. EmpowerID supports anonymous provisioning, allowing users to register for the services and be given a baseline of permissions. EmpowerID can federate with Facebook, Twitter, etc. to authenticat, claim accounts in other applications and manage any attributes.
EmpowerID can then perfrom two factor authentication, device registration or identity proffing to further confirm the user's identity. This seamless HTML5 interface works on any device allowing mobile usage and a better overall user experience.
Schedule a demonstration and see how you can manage your external identities, giving them more secure and easy access to your resources.

 Additionally, the applications they are accessing are growing more varied and widespread. You have legacy applications, cloud applications, web applications, and mobile applications. Organizations demand an IAM platform that can authenticate and authorize not against the ones that support a specific standard, but all of them.
Additionally, the applications they are accessing are growing more varied and widespread. You have legacy applications, cloud applications, web applications, and mobile applications. Organizations demand an IAM platform that can authenticate and authorize not against the ones that support a specific standard, but all of them.
 Groups are not roles. Especially when they are static by nature. Over 85% of organizations manage groups manually, you can never really be certain that the correct users are in the correct groups if that is the case. You need your roles to be dynamic and rule-based. You need your RBAC to be augmented by ABAC for on the fly
Groups are not roles. Especially when they are static by nature. Over 85% of organizations manage groups manually, you can never really be certain that the correct users are in the correct groups if that is the case. You need your roles to be dynamic and rule-based. You need your RBAC to be augmented by ABAC for on the fly 
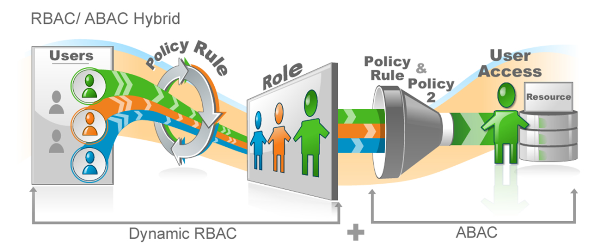 RBAC is definable, the user is a member of a role or isn't. If the user is part of the dental chair warehouse worker role, then they are granted access to resources that role needs. This role membership handles the user's coarse grained access...what files and folders they can access, in what applications do they have user accounts, what group memberships they have.
RBAC is definable, the user is a member of a role or isn't. If the user is part of the dental chair warehouse worker role, then they are granted access to resources that role needs. This role membership handles the user's coarse grained access...what files and folders they can access, in what applications do they have user accounts, what group memberships they have. Let's use that example of the dental chair warehouse worker. This worker needs access to a particularly sensitive section of your ERP system to order a gold plated footrest on the top of the line dental chair. But, your security team insists that the warehouse worker should only be able to access ERP during his shift.
Let's use that example of the dental chair warehouse worker. This worker needs access to a particularly sensitive section of your ERP system to order a gold plated footrest on the top of the line dental chair. But, your security team insists that the warehouse worker should only be able to access ERP during his shift. It should be an identity ecosystem. When a user is initially provisioned from HR (or a contractor database or a customer self-registration), you apply an initial role to that user dynamically based on what you know about them. That role (or roles) determine in which systems the user needs to be provisioned. An example is: sales rep in Toledo will need an Active Directory account, an Exchange mailbox, an ERP account and a salesforce.com account.
It should be an identity ecosystem. When a user is initially provisioned from HR (or a contractor database or a customer self-registration), you apply an initial role to that user dynamically based on what you know about them. That role (or roles) determine in which systems the user needs to be provisioned. An example is: sales rep in Toledo will need an Active Directory account, an Exchange mailbox, an ERP account and a salesforce.com account.
 Windows has created a false premise that the best way to manage
Windows has created a false premise that the best way to manage 
 EmpowerID makes role based SharePoint permissions possible by being a
EmpowerID makes role based SharePoint permissions possible by being a 
 Reading an article by Earl Perkins titled
Reading an article by Earl Perkins titled 
 The biggest benefit to attribute based access control (ABAC) is its flexibility. You basically are assigning permissions to anyone who meets a certain criteria. Dynamically. As soon as you change a person's job, location, employment status, any attribute in any system you want, you are changing their permissions.
The biggest benefit to attribute based access control (ABAC) is its flexibility. You basically are assigning permissions to anyone who meets a certain criteria. Dynamically. As soon as you change a person's job, location, employment status, any attribute in any system you want, you are changing their permissions.
 As George Orwell said, "All animals are equal but some animals are more equal than others." How does this apply to resetting passwords? Everyone needs passwords reset, but some need a little extra security around their password resetting.
As George Orwell said, "All animals are equal but some animals are more equal than others." How does this apply to resetting passwords? Everyone needs passwords reset, but some need a little extra security around their password resetting.

