The average user in a medium to large enterprise has 16 applications that they need to access to do their job. This means 16 username / password combinations. Doing the math, this translates to a metric boatload of help desk calls to support this many passwords.
There are three things you can do about this:
- Provide single sign on (SSO)
- Provide self service password reset
- Synchronize passwords between the applications
 There are advantages and limitations to each option. Single sign on is probably the best solution, having your users log in once and then be authenticated into each application. However, if the application doesn't support federation, you will need to do password vaulting and you still have the problem of a lot of passwords. Many legacy systems will have this limitation.
There are advantages and limitations to each option. Single sign on is probably the best solution, having your users log in once and then be authenticated into each application. However, if the application doesn't support federation, you will need to do password vaulting and you still have the problem of a lot of passwords. Many legacy systems will have this limitation.
Providing self service password reset is also a great option. It allows you to delegate changing passwords once forgotten and can have built in security like two factor authentication or forced enrollment. But, you're supporting 16 applications and you might as well fix the problem before the horse leaves the barn.
That brings us to password synchronization. You will give your user a single password that is the same for each application. When they change it in one place (for example, Active Directory), it will be synchronized to each application. Users will still need to enter a password each time, but they only have to remember 1 not 16.
Before I go any further, the same EmpowerID module for password synchronization also provides self service password reset, giving you option 2 & 3 in one fell swoop. Since EmpowerID is a single code-base platform, EmpowerID SSO Manager also can work in conjunction with Password Manager to provide all three options to work together.
EmpowerID is a hub and spoke model, with a metadirectory sitting squarely in the middle keeping identity data and passwords synchronized. You will most likely have a source of truth for the password, whether it be the EmpowerID directory or Active Directory. Once this password is changed, EmpowerID will write out that password to all affected applications using stored procedures or APIs.
If there are different password complexity requirements, EmpowerID can enforce the most restrictive and ensure that the user has a single password for all applications. If there are mutually exclusive password policies (no special characters in one but special characters required in another, we should explore single sign on).
The first question is usually, what starts this process? How can you synchronize a password if it is encrypted in the source of truth directory? We can't, nobody can. We need to force the synchronization process to start by changing the password initially. Once EmpowerID has the password, we can follow the security guidelines of each application to synchronize the new password to these 16 applications.
The simplest way to do this is to force the user to change their password on the next login, whether it is to EmpowerID or to Active Directory. This setting is easy to turn on and gives the user an easy way to create the new synchronized password. We can also build the password change action into any authentication workflow or give them the requirement to change the password x days before expiration.
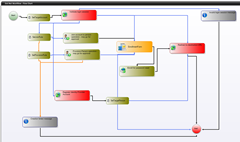 But we haven't really saved IT a lot of time yet unless it's easy to implement and configure. That's where EmpowerID's visual workflow comes in. Every identity action your users take goes through a workflow which can be customized and personalized. For our password example, this means that for users with more highly privileged access can be forced to change passwords more often or to also need two factor authentication with OATH tokens.
But we haven't really saved IT a lot of time yet unless it's easy to implement and configure. That's where EmpowerID's visual workflow comes in. Every identity action your users take goes through a workflow which can be customized and personalized. For our password example, this means that for users with more highly privileged access can be forced to change passwords more often or to also need two factor authentication with OATH tokens.
This workflow maps to your business process and gives you flexibility in how you manage your passwords and users, giving different policies for different roles or applications. In short, it makes password management flexible.
But once the users have a single password, the metric boatload of time saved by IT can go towards the single sign on (SSO) project you've been looking at.
Tags: Password management