Adaptive authentication conjures up images of complexity. Turning over your identities to HAL 9000 or something equally scary. But, in reality, it can be simpler than that. Remember the goal of identity and access management per Gartner is to ensure that "the right people get the right access to the right resources at the right time, enabling the right business outcomes."
Part of compliance to that principle is knowing who the right people are and what the right resources are. So, let's break out the actors in this adaptive authentication scenario into 2 people and 2 resources. Then it's simple to determine what the right access is.
People (or roles): 1) marketing manager and 2) finance director.
Resources: 1) salesforce.com, 2) folder containing 10K documents, and 3) internal SharePoint portal.
Each user will dynamically belong to a role based on their title, department and location for example. In this case, we will consider these users as roles.
Both roles need access to Salesforce.com. It is considered a security level 2 application when being accessed by any role outside of sales and requires a second factor authentication when accessing.
Only the finance director needs access to the 10K documents but since these are highly secure level 3 security resources, not only is a second factor authentication is needed, but a notification needs to be sent to the CFO every time someone accesses the documents.
And both roles need access to SharePoint; no adaptive authentication needed.
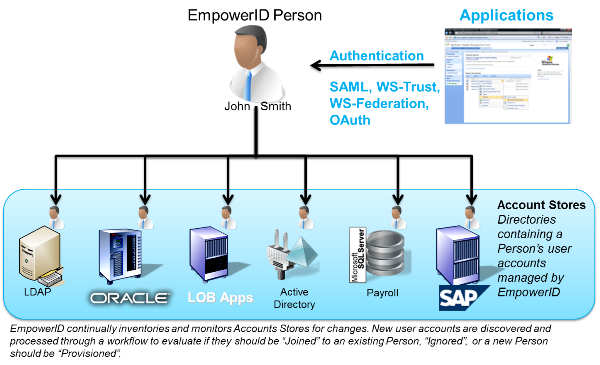
This is what makes adaptive authentication possible. The empowerID directory is actually an identity provider and users authenticate against it. Since it supports federation, it will use your Windows authentication, but still be managing all of your application and resource access.
So, in the first scenario, when the two users try to access salesforce.com; empowerID will see that their roles are not in sales and force a second factor authentication before authenticating them to salesforce.com.
The same thing happens when each user tries to access the financial documents in the 10K folder. empowerID stops the marketing manager dead in his tracks since he doesn't have access to that resource. When the finance director accesses the folder, empowerID enforces the second factor authentication and sends a notification to the CFO. In this instance, you could also do identity proofing, have a workflow approval, or even grant only temporary access.
The same two users go to SharePoint and both are already authenticated. Of course, once in SharePoint, the users have different experiences based on their roles in empowerID, but we aren't forcing any extra authentication here.
Adaptive authentication is a fairly straight forward concept that doesn't have to be any more complicated than what we described above. You set security levels on your resources (as granular as you would like); you create roles for your users. Certain roles have more stringent authentication requirements for certain security level resources.
You are able to improve security without forcing these more strict security measures on every single role and resource.


