When you embark on an RBAC project, you have to consider that you already have roles in place. Application roles, location roles, OUs, and security groups. All of these have to be mapped to your management and organizational roles.
Let's start with mapping location roles to physical locations. Your OUs are probably organized by location or geography. Many of your RBAC permissions are based on location and you want to have a single parent role for each location with multiple OUs and directory locations mapping to the single location based role.
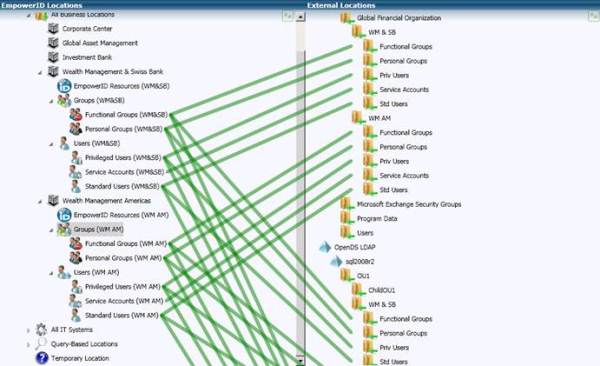
As you can see, you can map multiple external roles to a single empowerID role. This allows you to manage more permissions and access with a single role in empowerID.
This concept becomes even more important with application roles. A single sales manager role in empowerID can map to the salesforce.com role, the Exchange role, and the SharePoint role. It takes you out of the business of managing roles and permissions in every single application on your network and cloud.
The benefit to you is that you can make the empowerID roles dynamic, have the user's roles change based on any attribute changes in Active Directory or any other connected system. So that sales manager gets promoted to sales director and all of his/her roles change immediately. Not only in empowerID but that streams all the way down to all of his/her application roles.
Take a look at our whitepaper on enterprise authorization and the RBAC / ABAC hybrid approach. Or save yourself some wear on your reading glasses and arrange for a demonstration of role mapping for complete RBAC.